ExchangeDefender Security Compliance

ExchangeDefender is helping our clients and partners comply with email validation & authorization requirements. DMARC (SPF + DKIM) help prevent unauthorized hijacking/spoofing of your domain name and are used by email services to separate legitimate email from SPAM.
We’ll offer assistance for SPF + DKIM
In order to assure reliable email delivery, ExchangeDefender is offering assistance with SPF + DKIM rollout from September 20th through October 20th. All domains must be brought to compliance by October 30th, 2021 in order to continue relaying mail through ExchangeDefender. We’ll even do it for you, for free.
For more information on our new email security standards, please see our DMARC webinar, and read our DMARC guide.
Every domain that uses ExchangeDefender to send or receive email is required to update their SPF and DKIM records. Failure to comply will result in having your email bounced.
How to get started:
Step 1: Contact your DNS Administrator
You will need to contact your DNS administrator or DNS hosting provider to create the following DNS records:
SPF Record
DNS Record Type: TXT
DNS Record Value: “v=spf1 include:proxy.exchangedefender.com -all”DKIM Record
DNS Record Type: TXT
DNS Record Hostname: default._domainkey
DNS Record Value: “v=DKIM1; k=rsa; s=email; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAwkMvl3dS3g9XbhxtD16tSx/l+s0cxVv73/NCHywH2HFED61k+orBj4QY96FJcUD7MOwmwjC7Igtz5P9fVOLFoMr+d8g8c5J5OIA8Xj2ap4jsEnSF3rRrCNJDxojPvtGA1+ENwGpheHtniZG/fgVguDL+M1zXNRsYTybzKwU49tmP4RyIFIC8NEV7jqrGSVWpQSXc12JlvmLQX1J5tdnWvTR7/NGOzyth0rYP1STKj1hHU9ZVN+x8VFiumlPdpDQBMn5Bzu/Cs6pzrSHJqGBcVer4mccpnCOX9bG3sR7wU6nDIv3rvwIlfBymylcZruJvjsXZAZaameUBpgGgmibpkwIDAQAB”
Step 2: Validate your DNS records
After the DNS records are published please validate them using public tools like MX Toolbox (https://mxtoolbox.com/SuperTool.aspx) or DMARC Analyzer (https://www.dmarcanalyzer.com/dkim/dkim-checker/). Until your DNS records validate, you are not in compliance and will have issues with email delivery.
Step 3: Turn on DKIM signing
After your DNS records have been published and validated, you will need to turn on DKIM signing. Go to https://admin.exchangedefender.com, login as Domain Administrator and go to Mail Flow -> DKIM Signature.
Finally, click on Accounts and confirm that all your email addresses are listed and associated with appropriate users.
We’d love to help, if you’d like us to take care of this for you free of charge please fill out this form:
https://www.exchangedefender.com/security-lockdown
General Data Protection (GDPR) and ExchangeDefender: Get your resources to demonstrate compliance
ExchangeDefender, at it’s core, is all about protecting our clients: it should come as no surprise that we are big fans of GDPR. If you haven’t been inundated by GDPR, or by a million “we’ve updated our privacy policy” emails from every web site you’ve ever signed up for, or you’ve landed here simply because the deadline is tomorrow, Friday, May 25th: rest assured we’ve got you covered.
ExchangeDefender is 100% compliant with GDPR. You are covered as are your clients on ExchangeDefender and we have presence across European Union to handle any issues or complaints that come up as a result of GDPR implementation.
What you need to know
GDPR, essentially (and no, this is not legal advice), is a European Union data privacy regulation that turns the tables on marketers and gives residents of EU very specific rights and control over their personal data. The regulation is very broad in terms of scrutinizing everyone that may be holding (controller) or managing/processing (processor) personal data and ExchangeDefender fits both of those roles at times depending on the product or service we’re talking about.
If you’d rather do without me talking at you for 6 minutes, we have a ton of other resources that you can share with your clients. I would start with this document available for download here:
What you need to do now
1. Start by reviewing our new Privacy Policy. I know, I know, you’re done with
2. Contact us if you’re seriously building out a business around GDPR and get our marketing folks to hook you up with branded collateral (minimum client count
3. Review our GDPR collateral, particularly the webinar with the deep dive of the ExchangeDefender implementation. This is the most important thing you could do but it’s 27 minutes long and I know everyone doesn’t have that kind of time or attention span – I get it – but if you’re seriously working with us and need GDPR assistance, you will have to go through the training eventually.
Where to go next
We are very excited about GDPR and have put significant resources to design our products and services around the regulation because we believe it will have a broad impact well beyond Europe. Privacy, data integrity, right to be forgotten, right to withdraw consent, right to find out what sort of information companies have about you – those are fundamental rights in our opinion.
And if you ignore them the penalties are going to be extensive.
What we’re choosing to do at ExchangeDefender is to create a service around protecting people on the Internet – not just from SPAM but really safeguarding all communication you do as a business. Take a look at our GDPR resources and see how we can get you started on the same path – at the very least you can use our reach and resources to comply with GDPR.
The false sense of cloud security: “I don’t need backups or archiving, we’re in the cloud.”
One of the most common misconceptions we get to deal with in the email business is the notion that the almighty cloud eliminates the need for backups, redundancy, compliance archiving, and disaster planning in general. Nothing could be further from the truth so please share this checklist with your clients and decision makers so they can make informed decisions about how much protection is needed for critical business data.
Now, let’s tear apart the myths we hear most often:
It’s in the cloud so it’s already backed up. You will not find a single cloud service provider that will offer their backup policies in explicit detail. This is not just a matter of secrecy (exposing the network and storage design) but also of implementation: some services just don’t have a backup only a lagged copy. Never, ever, assume that your cloud provider cares about your data more than you do, it’s no coincidence that the first thing you do with every service you sign up for is a mandatory acceptance of terms of service that you’ve likely never read. Your data is your sole responsibility.
It’s in the cloud and they say it’s there forever. Sometimes marketing gets falsely associated with the actual service deliverables: “You will never have to delete email to make space” doesn’t translate into “Your email will never disappear” – all major email providers have a well documented trail of losing clients mail, deleting their mailboxes “for policy violations” and otherwise shunning any responsibility.
It’s in the cloud so someone is actively managing it. Cloud service providers manage the cloud service, management of your personal data is often the secondary concern. That sounds harsh so allow me to elaborate the top down view: Imagine your service just crashed, massive catastrophe: What is your primary concern? Restoring access to service to send/receive email, or restoring clients data from 5 years ago? Now align those priorities with the budget: What is more important to the cloud provider: service operation or access to old data? Many services are even pushing for not keeping all of your data in the cloud at all, the notion of archive boxes and focused views is all about not having the responsibility for your data.
It’s in the cloud so it meets compliance. Your regulatory compliance requires assurance that data could not have been deleted. That kind of assurance only comes with services like ExchangeDefender Compliance Archiving which archives messages before anyone has a chance to tamper or delete the data. Furthermore, the backend system for an archiving or compliance solution is radically different because of the liability: companies that insure confidential data storage are far more concerned about redundancy, backups and data loss than they are about the uptime and service availability.
Now that the myths surrounding the false sense of cloud security are shattered, let’s look over a brief plan you need to implement to safeguard your data:
1. Document everyone with access to email.
2. Come up with a policy for adding/removing employee email.
3. Identify any regulatory compliance requirements.
4. Identify business case scenario requiring long term archiving.
5. Document who has access to what and how changes are tracked.
6. Come up with a data retention and data backup plans.
7. Understand the law and security, make neccessary adjustments.
8. Designate a Compliance Officer to manage everything.
9. Test your backups and compliance archiving routinely.
10. Periodically audit everything in the previous 9 steps.
Truth is, there are hundreds of steps in cloud security management for each of the 10 items I listed above: The goal isn’t to give you a blueprint, the goal is to make you aware of complexities and the issues that can come up when the basics are ignored. If you would like the details, give us a call, email is what we do for a living and (unfortunately) our expertise is developed over the years of cleaning up our clients neglect of their email infrastructure – let us and our partners know how we can help.
Top 5 Mistakes Companies Make With Compliance
ExchangeDefender Compliance Archive was designed as a blend of services and products to help organizations achieve regulatory compliance. This complex process is always evolving with new regulatory requirements, changes in organization structure, and unique reporting requirements.
At ExchangeDefender we specialize in helping organizations with their eDiscovery needs. Here are the biggest fallacies we hear all the time:
“We have a backup”
Email backups are not sufficient for nearly any modern regulatory compliance requirements for email retention. Not only can the messages be deleted before backups run, but running reports across the entire organization is next to impossible, not to mention excessively expensive. We recently assisted a partner managing a small 15 employee office in their backup and restore process to locate a message from 5 years ago, costing the organization over $18,000 in IT labor alone.
“We have a product/compliance service”
Having a product or a service subscription is different from being in compliance with regulatory requirements. The difference between having a product and being in compliance is similar to “We have a CPA” and “We have filed our tax returns on time” – mistaking the two can be costly and dangerous.
“We are never going to need that”
Most organizations downplay the importance of long term email archiving and eDiscovery. An overwhelming majority of subscribers to our eDiscovery service don’t have a specific regulatory requirement at all, they do it to effectively defend themselves from legal threats that are all too common these days. With email being the gateway for all corporate communication, it is the first place record retentions, legal holds, and subpoenas are issued for electronic records and there needs to be a system in place to effectively deliver that information.
“What we have is enough”
Regulatory compliance goes far beyond poorly interpreted recommendations and laws. It is a process of producing reports, identifying problems, and assuring that corporate communications policies are being followed, or at least addressed, in case there is an issue. If the organization does not have people in charge of managing the compliance on a monthly basis or there are no current reports searching for dangerous or sensitive content or there is no ongoing maintenance or an established incident record – the organization is likely out of compliance even if they purchased the right software or signed up for the right service at one point.
“We have a someone managing that”
Someone is not a good person to rely on when you get a subpoena and they are even more difficult to get into a courtroom. Plus, how much would you trust them to demonstrate expertise and defend the implementation of the compliance archiving and eDiscovery solution? Many organizations make a mistake of thinking that just signing up for a service or purchasing a product is sufficient for compliance but it’s really just a starting point. You need the personnel, product, service, and reporting to fully achieve regulatory compliance.
ExchangeDefender Compliance Archiving and eDiscovery are a part of a professional service that helps get your organization and its means of communication on path to achieving regulatory compliance. Whenever someone is fully confident that they have their compliance in order we simply ask them to “show me your last Compliance Officer Report” and almost everyone struggles to produce the report or even name the Compliance Officer, the processes being used for archiving, the type of data protection, or the way in which the entire process is tested and audited. With ExchangeDefender Compliance Archiving, you not only get a service, you get a partner that will work with you every step of the way in achieving your regulatory and organizational needs for proper record keeping.
Achieving eDiscovery and Compliance Archiving requirements in 5 steps
 Signing up for the Compliance Archiving service is the first step in reaching regulatory compliance when it comes to email retention and eDiscovery. The following five steps will put you on the right path of achieving and maintaining that compliance:
Signing up for the Compliance Archiving service is the first step in reaching regulatory compliance when it comes to email retention and eDiscovery. The following five steps will put you on the right path of achieving and maintaining that compliance:
1.Understand what you need to keep and for how long.
Your regulatory/oversight body will provide details about how long you are required to hold on to your email. In our experience with Compliance Archiving, you also need to pay attention to the Statue of Limitations that your business may be liable for. Very often the discovery process for lawsuits includes legal hold requests and record requests that are longer than regulatory requirement.
2. Get the right product and implement it correctly.
Your compliance has to be all encompassing – all email must be archived. With ExchangeDefender Compliance Archiving all of your inbound, outbound, and interoffice email is collected, archived and protected in the cloud. You can search for any document at any time and be certain that it has not been tampered with and that no emails have been deleted – something that sets our eDiscovery/archiving apart from backup solutions.
3. Keep an eye on it to make sure it works
Just setting up a compliance archiving solution is not sufficient enough. there is no protection for technical negligence in regulations. You are expected to keep your mail server and everything connected to it secure. Penalties for data loss, compromised credentials, and data leakage are severe and are not a valid excuse for not having compliance.
4. Create Compliance Officer reports frequently.
Compliance Officer within your organization must create reports on a monthly basis to assure no confidential information is allowed to leave the organization. Some industries have an even more specific and severe restriction on the type of communication that can take place over email and what sort of information can be sent – compliance officers run eDiscovery reports to assure nothing confidential is being shared and address problems and exceptions routinely
5. Routinely audit the entire system to maintain compliance.
Organizations grow and change over time and remaining compliant with new regulations is key. ExchangeDefender Compliance Archiving service often sends out advisories, best practices, tips and suggestions to adjust your process because you are always expected to be in full compliance with the latest requirements. Every time you add a new employee or change your mail server configuration or new lines of business – compliance must extend to cover these new records that may be of interest to someone down the road.
“One of the biggest mistakes organizations make with regulatory compliance is thinking that it’s a service, product or a one-time effort: quite the opposite!”
Achieving regulatory compliance means implementing the right product, conducting routine audits, complying with changes in regulations and having full control of the environment where messages are stored as employees come and go.
In the event of an audit, you will be asked to produce record and you will be judged on your ability to provide specific records that are requested, not the best effort you made in trying to achieve compliance. Considering the fines and legal complications, it makes sense to revisit the five steps outlined here annually and make adjustments as necessary.
Why is there suddenly a heavy demand for Encryption?
What is behind the growth in the adoption of email encryption?
Over the past year we’ve seen an explosion in sales of ExchangeDefender Email Encryption – which is a surprise given that we’ve not only had it for years but that we’ve also given it away for free. HIPAA has been around for over 20 years, dozens of other regulations that almost all companies ignore have been gone for just as long – so why now?
In one word: penalties.
Companies have long known that they can’t operate efficiently without email – and that they cannot just move files around “just to get it to them” once they see the penalties. But selling a service to someone that has avoided using or paying for it is never an easy discussion so here are the 3 quick questions that should lead you to an effective pitch in under 1 minute:
1. Who sends you encrypted messages?
2. Who could get hurt if this information went public?
3. What is your exposure? How much negligence insurance do you have?
The more they mumble, the more of those questions they cannot answer, the more details or costs or scope they don’t understand, the more they need it. End your question with this line: How comfortable would you be having this conversation in a legal deposition?
Elevator pitch: How to position ExchangeDefender Encryption as an answer to all of the above problems
→It is included in your ExchangeDefender Pro subscription and it’s transparent – no software to install, nothing to manage or configure.
→ You’ll be using the same process and same security major banks, health care providers and lawyers use – so you’ll be protected from most critical security exploits.
→ Finally, it’s dead simple to use – all your employees need to do is put [ENCRYPT] in the subject when they are sending the message. Doesn’t matter if it’s on the phone our Outlook or Outlook Web Access, it just works.
Ding. You’re done. It’s virtually impossible not to sell this service – and it’s desperately needed by anyone using email to do business or conduct confidential discussions. One more thing: Because encryption is transparent and on demand in the cloud, it also protects you when the security issue is on the recipients end – because email is never stored on their PC or device, if someone hacks their network they won’t be able to get to the info stored in your encrypted message!
If email is a business necessity then email encryption is it’s insurance policy.
If you discuss business over email, then anything confidential that should be in that email should be a matter of employee communication protocol: If you attach something sensitive to this message, you better encrypt it and CYA. This is the way things go at banks, with lawyers, with accountants, with realtors and at nearly every white collar job: Nobody wants to assume the liability so they’ll all do what it takes to protect the data.
And with high profile hacks and compromises in the news daily, is not having it worth risking the whole company?
Development Log
Over the past few months I’ve taken the time to update several different aspects of our product offerings. The updates and products we decided to implement were prioritized based on bugs & feature requests that had been submitted properly through our internal support portal.
First on the list was our Outlook 2010 & 2013 SMTP Security Add-in, which also applies to the desktop agent. We’ve added several new features, improved performance and fixed a few bugs. Listed below are the enhancements we’ve added based on user feedback.
- Added the ability to view & manage alias accounts.
- Added the ability to disable automatic refresh.
- Added a direct link to the user’s web portal.
- Fixed a link causing quick links to not work properly.
- Added version numbers to the settings page.
- Updated the “Dismiss All” label to “Review All”.
- Window size & state are now persistent between restarts.
- Added the ability to resize the window.
- Added the ability to resize columns.
- SPAM counts are now listed next to the addresses.
- Right click menu has been added.
- We’ve added the ability to trust an entire domain.
- Updated Documentation
- Updated Publisher Information
We’ve also went through an updated most of the online documentation since we’ve undergone such dramatic changes throughout the years. New images have replaced old instructional images, revised steps and procedures for various platforms and even structured the documents to allow for easy navigation. You can find all of the updated documentation here: http://www.exchangedefender.com/documentation.php
Several core internal programs have also been updated to allow our highly trained support staff to escalate and speed up response time for some of our more complex requests. One area of improvement has been geared towards Compliance Archive and simplifying the process to retrieve an export of a user’s mailbox.
We’re currently working on bringing several enhancements to LocalCloud. We’ve had several clients report issues with client stability. So we are working on a performance update, which will also allow for automatic updates in the future. We are also working on enhancing the Web Sharing file uploading service, by enhancing the upload controls and server-side timeouts.
Compliance Archive – Improved Searching!
Over the last month we have been in the process of improving the architecture behind Compliance Archive. Your information has already been migrated into this new compliance standard and we were able to do this with very little noticeable downtime. The main reason for this improvement was to help enhance database performance and finally be able to offer advance searching and audit reports.
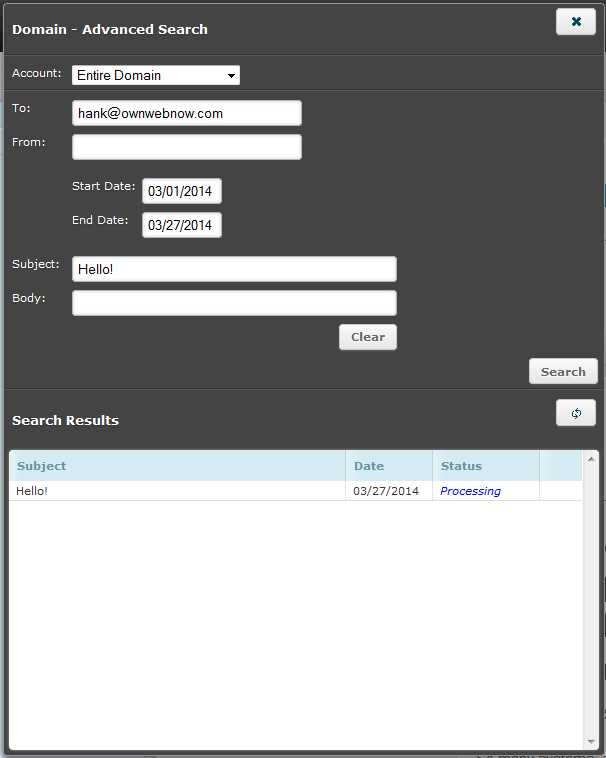
To give you an idea, on the old architecture an advanced report would take roughly 20-30 minutes and would typically time out due to (multiple refreshes) or a user’s browser becoming unresponsive. So before we built the GUI to allow for these searches, we had to get this under control.
Now with the new system not only do searches come back typically within 3-4 minutes, they are scheduled jobs. So you type in your search, submit your criteria and either wait or check back once they have finished. The best part is, you can REPEAT your searches once they’ve finished! So let’s say you’re required to perform the same mundane search once a month, now you can with only a few clicks!