Enhanced Security: ExchangeDefender Now Supports Custom Authenticator Apps for MFA!

ExchangeDefender has recently enhanced our MFA features (multi-factor authentication) to help you enforce domain-level MFA compliance and to make it easier for users to be enrolled and protected by a layered authentication process automatically.
Simply put, we’re making it easier for you to keep everyone protected.
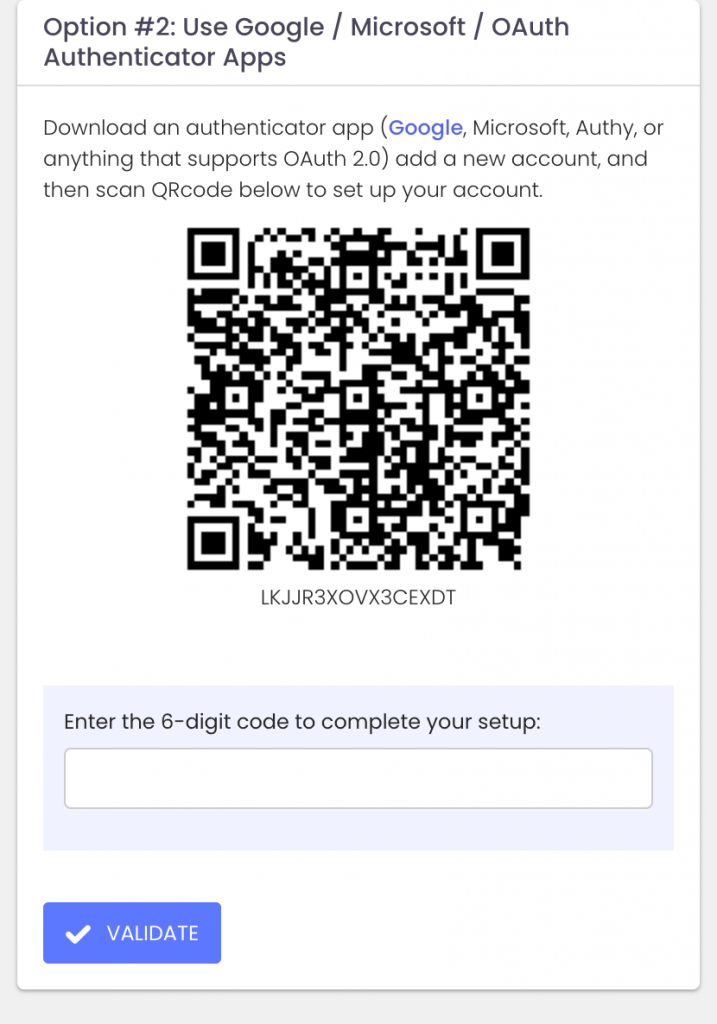
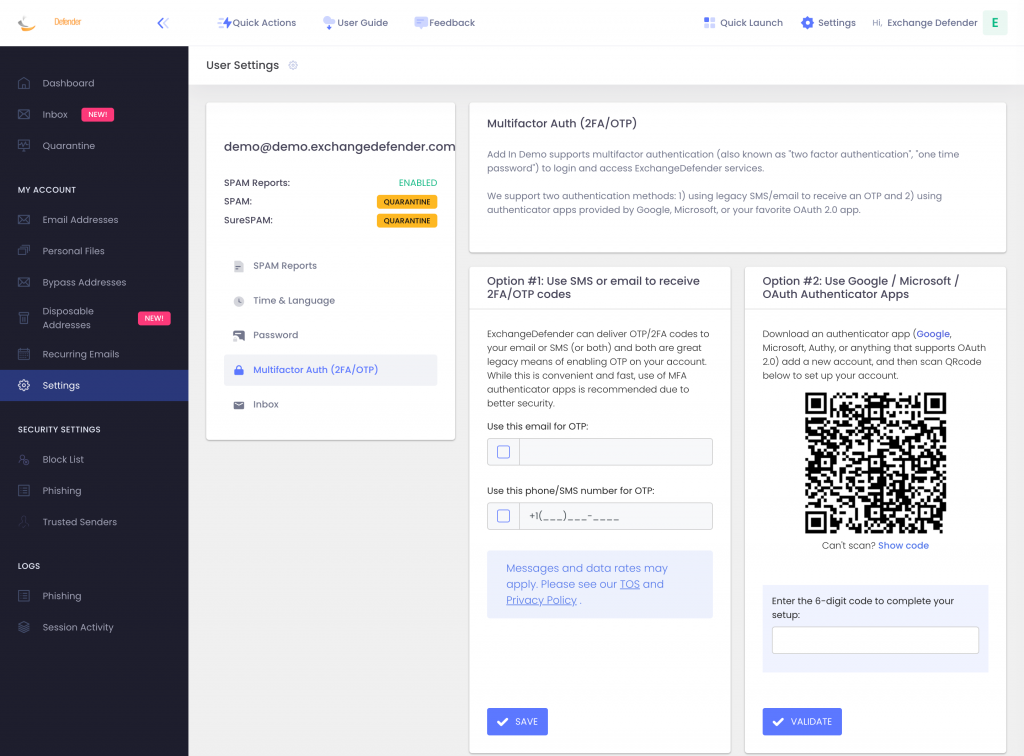
Today we are announcing ExchangeDefender MFA support for custom authenticator apps. By now everyone is familiar with our typical MFA functionality, available under your Settings at https://admin.exchangedefender.com. Just scan the QR code on your device and you’re set!
BUT WHAT IF YOUR DEVICE DOESN’T HAVE A CAMERA?
ExchangeDefender now supports MFA app enrollment using a QR code. This is great for scenarios in which:
– You don’t have a camera on your device
– The QR code doesn’t seem to scan (problems with the camera or monitor)
– You want to use a text-based MFA app
– You want to integrate PowerShell/no-code with MFA
– You want to share your MFA codes with others
If you’re in one of those scenarios, note the text under the QR code when you start the enrollment:
Click on the Can’t scan? Show code link and you’ll get the TOTP secret (aka secret code, MFA code). Paste it in your solution and paste back the 6 digit code it generates. That’s it, you’re done. MFA is now enforced and ExchangeDefender will rely on the codes generated by your app to validate MFA and grant access to your account.
All our features come from user feedback so if there is something we need to be doing to keep you more secure please let us know!
Enhanced MFA Enforcement Policy: Strengthening ExchangeDefender Security Measures

For years, ExchangeDefender users have enjoyed enhanced login security via multi-factor authentication security (aka MFA, 2FA, OTP). In our March feature update, we hope to improve your security and enhance MFA enrollment to keep you and your data safe. Allow us to introduce to you the new MFA Enforcement Policy!
Note from the boss: Before we get to any discussion of policies, our official recommendation is to enforce MFA on every service we provide and to rotate passwords at least once a quarter. I know, nobody likes the second validation prompt but this is a standard in the industry and I can’t think of a bank or a vendor that doesn’t require it. Maybe I’m jaded because we’re a cybersecurity company.. and with all the layers of MFA/VPN/auth we have in place I spend an insane amount of time trying to find my key or wait for the new pin to display in my authentication app. Because when I interact with a vendor that holds my information and they have no login security.. all I can wonder is what else they’re not doing to keep my data safe? Is this a real business or some WordPress plugin?
At the same time, I understand we have a ton of customers in SMB space where sometimes (obnoxious) tech can be slow and difficult to implement. But you pay us to keep you safe – and to keep your backups safe, and to keep your business continuity safe, and to do that we absolutely must require MFA. But we also can’t expect staff who have clicked on a Release/Trust link for over a decade to be cool with suddenly being forced into MFA enforcement workflow on Monday. So we designed a compromise. I hope it fits your organization and I hope you adopt it as fast as possible.
Sincerely,
–Vlad Mazek, CEO Own Web Now Corp.
In March 2024 you will have the ability to enforce or require MFA enrollment at the domain level. What this means is that you’ll be able to require MFA enrollment with an authenticator app for everyone with just one click at https://admin.exchangedefender.com:
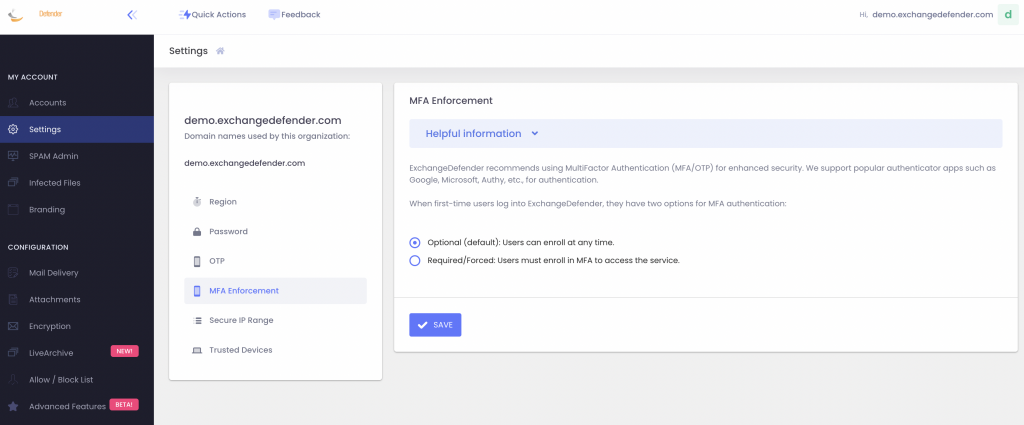
With this policy, you can secure your users’ login with multi-factor authentication without making them enroll a device.
How does it work?
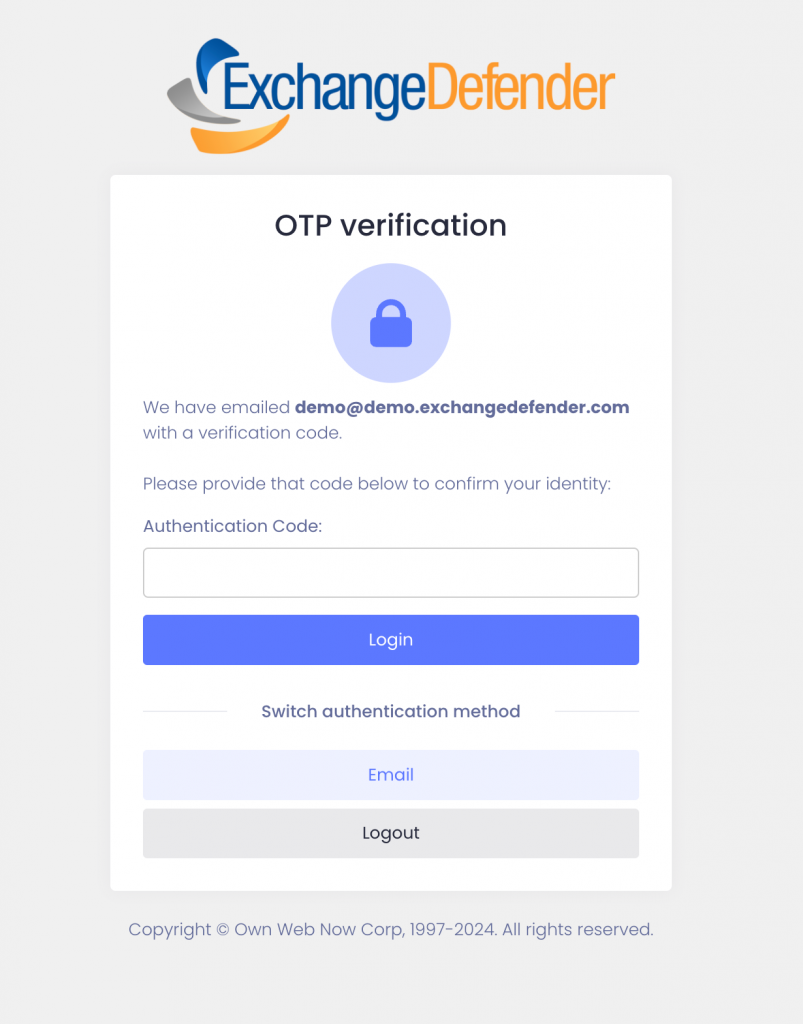
When your users go to admin.exchangedefender.com and attempt to access Inbox, WFS, or LiveArchive we will check their MFA enrollment and if none is found we’ll just tell them we have to verify their identity:
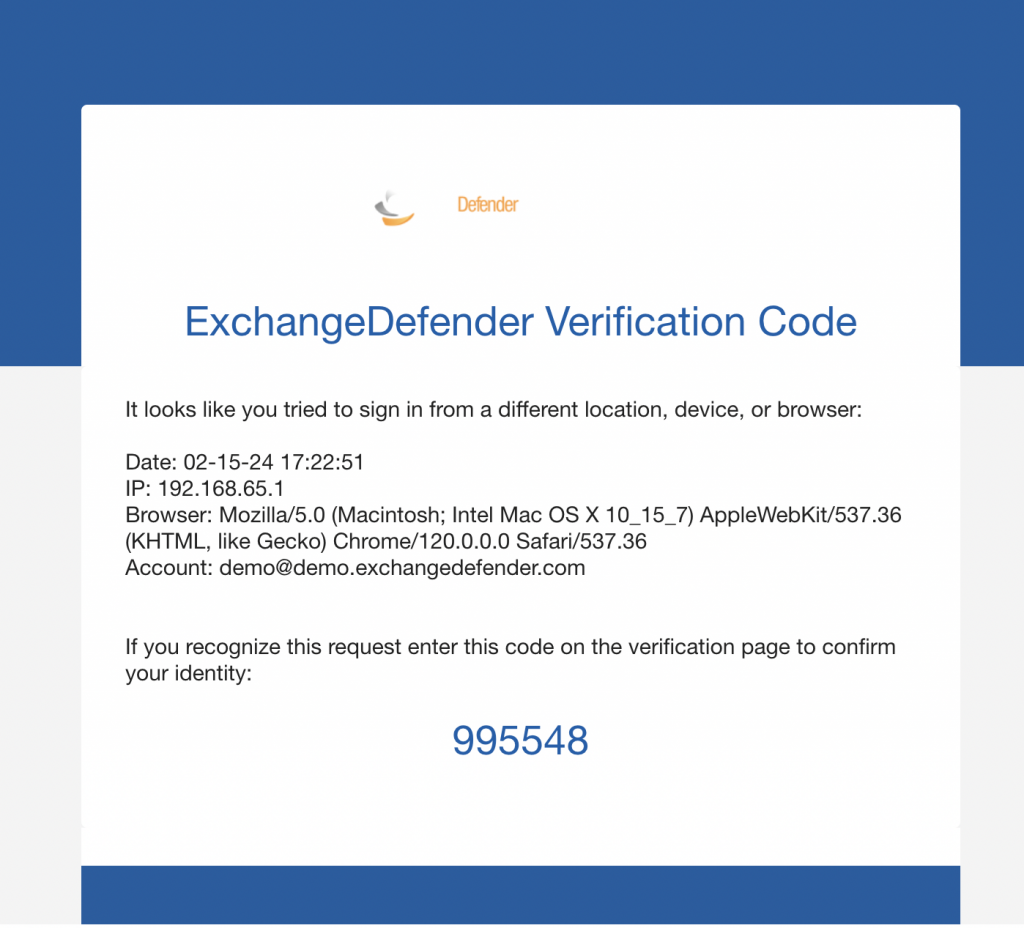
When they check their mailbox they’ll see an email from ExchangeDefender and just provide the code back.
This way your ExchangeDefender login is technically secured at ExchangeDefender with MFA even if you haven’t enrolled a device in MFA yet. There is no way to get into the secure areas of your account without enrolling into MFA. But what if someone guessed the password, they can just enroll a device and hijack the account, right? No.
When you set MFA Enforcement to Required/Forced, all your users are automatically set into an MFA mode that relies on their email address for secondary verification. When they visit admin.exchangedefender.com for the first time and provide their username and password the system will check their MFA enrollment and if email MFA is detected the system will send them an email with a verification code to proceed. This way we’re using the email MFA as a way to verify their identity and then we enroll their authenticator app as usual by scanning the QR code.
ExchangeDefender Quarantine Reports behavior will not change at all as a result of the change in the MFA Enforcement policy. ExchangeDefender Quarantine Reports do not rely on the login system at all as the user is never prompted to authenticate to trigger the release of the message. Instead, quarantine operations are tokenized and one “release” request does not automatically grant any other release or trust requests with the same token. It also doesn’t automatically log them into ExchangeDefender so there is no getting by the MFA!
Secure your logins now
It’s 2024 and the world has changed when it comes to authentication and identity when dealing with services online. Experiencing a cybersecurity threat or compromise is an incredibly expensive and frustrating experience that can easily be avoided by requiring an ID check before granting access to sensitive information. ExchangeDefender MFA Enforcement Policy is your way to protecting your organization from unauthorized and unverified access.
Improved SPAM Release Security: Quick Release

ExchangeDefender is giving users more power to lock down their valuable data. Now that ExchangeDefender handles business continuity and backups for M365/Gmail tenants there is even more information in ExchangeDefender that demands more flexibility with security policies. First, let’s talk about the upcoming feature that allows you to lock down your ExchangeDefender SPAM Quarantine Report activity.
Bit of background: ExchangeDefender Quarantine Reports are an immensely popular ExchangeDefender feature (coming up for an upgrade this spring btw!) that sends users a list of quarantined messages with a set schedule. Users tend to rarely look in Junk Items or review SPAM unless they are waiting for something so this is a cool feature that our users just love. Scroll down the list of quarantined messages and release or trust just by tapping the link. Super convenient, but does it meet your security requirements?
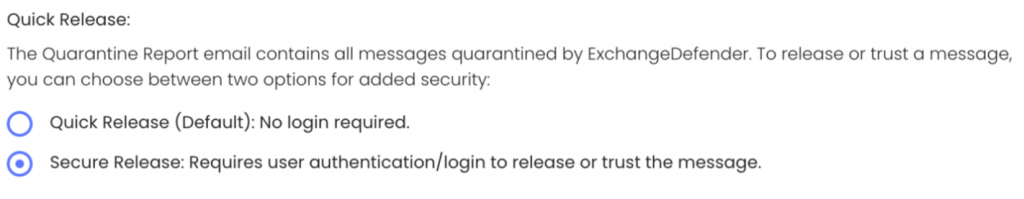
ExchangeDefender Quick Release feature now enables you to choose between convenience and a more secure release process. For many organizations, having the message released or get added to trusted senders with just a click is a huge time saver and user convenience. But if your Microsoft M365 / Gmail account gets compromised (which happens ALL the time) or you deploy a new security/business/CRM (mostly AI stuff) that scans links then this “convenience” can turn into an Inbox packed with SPAM messages that some hacker/service inadvertently released.
If this happens to you, know that ExchangeDefender can help with the “Secure Release” setting. By enforcing Secure Release, when the user clicks to release or trust a message they will be prompted to authenticate before they can release/trust the message. This way if you get hacked or install link scanning/crawling software in your tenant will not be able to access the messages without a password.
Now please, go setup your favorite authenticator app with ExchangeDefender MFA (next up, you can set it to be mandatory/required)
ExchangeDefender Phishing Firewall and Microsoft Defender
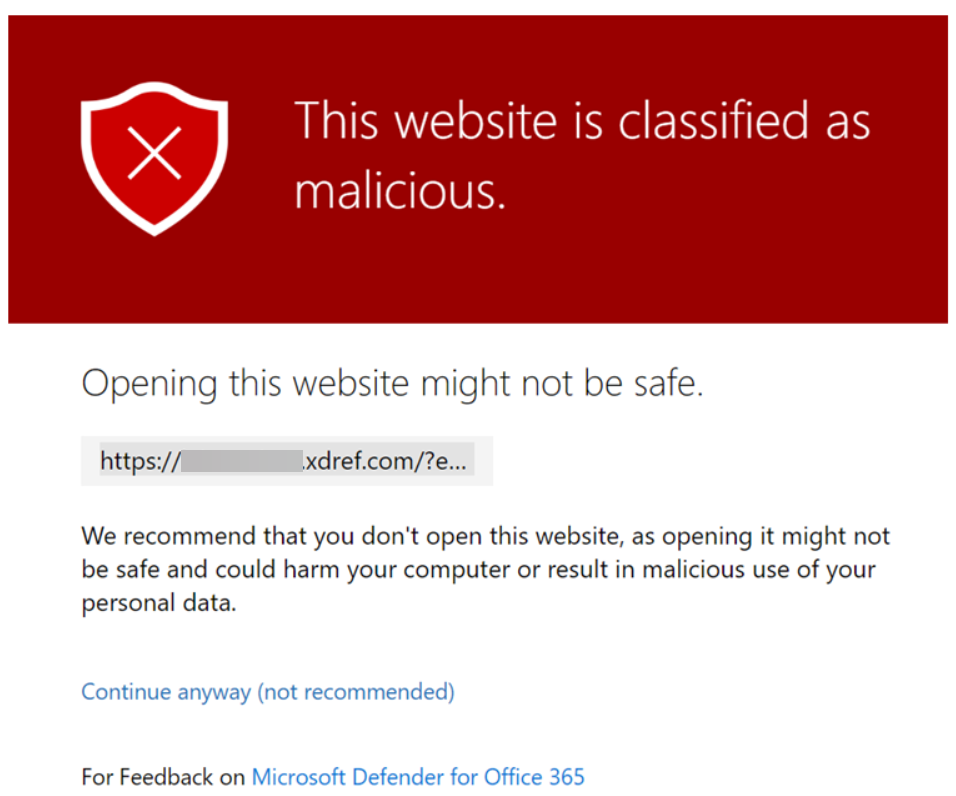
Now and then Microsoft Defender will encounter something potentially dangerous when it’s processing your browsing activity. Most of the time it is just the URL of a site they’ve blacklisted.
Enter ExchangeDefender Phishing Firewall. We rewrite every URL going through our service to give our users an extra layer of security and prevent malware and phishing. If you’ve seen the xdref.com links in your email, that’s US keeping you from accidentally clicking on a legitimate link and getting a zero-day exploit compromising your PC. Well, Microsoft Defender looks at the same link and its contents and can flag an entire URL of your phishing firewall. Then you end up seeing this:
How do I get this resolved?
Since this URL is exclusively used by you and your clients, make sure you’re using ExchangeDefender Outbound Service to route outbound mail (our outbound service strips all the xdref.com URLs).
Next, please report the problem with the URL to Microsoft at this location:
https://security.microsoft.com/reportsubmission?viewid=url
How do I fix it?
There are two ways to solve this problem within your tenant at Microsoft 365. The fastest way is with PowerShell:
New-TenantAllowBlockListItems -ListType Url -Allow -Entries ~xdref.com~ -NoExpiration
The more user-friendly way to allow the URL is through the Microsoft Defender Portal at the following URL (make sure you’re logged in first):
https://security.microsoft.com/tenantAllowBlockList
Microsoft tends to move its security components around a lot so if the URL changes login to the Microsoft 365 Defender Portal and go to: Policies & Rules> Threat Policies > Rules section > Tenant Allow/Block Lists.
To learn more about Microsoft Defender and how to manage its security policies on this topic please see the following KB article.
Tip: ExchangeDefender recommends executing this process when the client is onboarded, but it will work at any time.
Cybersecurity and Healthcare: what you need to know
Ransomware attacks on U.S healthcare organizations are predicted to quadruple by 2021, according to recent industry reports. Hackers are increasingly targeting healthcare due to the vast amounts of personal health information, which is considered 50 times more valuable on the black web than their financial information. The need for the ability to secure personal information is urgent, and requires immediate attention of the medical industry.
2022 CYBERSECURITY CHALLENGES
Malware, ransomware, and viruses
M365 application threats
Phishing attacks
Information protection
Misleading websites
Employee error
Account takeovers
Hackers deploy malware and ransomware to shut down and control devices, and even servers. Many healthcare organizations tend store health information without proper encryption leaving them vulnerable to external threats. Phishing attacks have been the newest and most successful method of cyber-attacks in which cyber criminals send mass emails from “reputable” sources to obtain sensitive information. Hackers link these emails to misleading websites to entice the user to enter their personal information, mainly their username and password to gain complete access, and commence in account takeover efforts.
OUR SOLUTIONS FOR HEALTHCARE
Thousands of Healthcare organizations trust ExchangeDefender to protect their data, and to keep their employees, and client information safe and secure. We protect your practice from malware, ransomware, and phishing attacks using Email Security, our advanced multilayered security suite. We secure patients’ information by enabling our Email Encryption which offers military grade security and prevents data leaks. Healthcare practices must be HIPAA compliant, and rely on ExchangeDefender for Email Archiving and Compliance. This service ensures compliance with long-term tamper-proof email archiving and unlimited storage. Our Web File Server protects your organization from cloud application threats, enables your team members to upload, manage, and share documents securely. The service is encrypted, and provides full reporting of all activity for accountability and transparency. Security tip: To increase your organization’s resistance against cyber-threats, start with powerful email security, add web security and data protection, and to ensure that you always have access to email even during service disruptions, our email outage protection.
Are you a medical office looking for IT solutions? We can help, visit www.365defender.com to see our services!
5 reasons to secure your law firm right now

Hackers are making big money on the legal industry lately, and it seems to only be getting worse. Law firms are vulnerable to cyber attacks due to the nature of their profession. They handle very sensitive information about their clients like: financial records, company secrets, and health information. Cyber-criminals are taking advantage of the fact that the legal sector is slow-moving when it comes to securing their data. If you’re a lawyer, or work for a law firm, here are five major reasons why you should take measures to secure your company right now:
Reason #1: There is a dramatic increase of data breaches
Law firms pose a higher risk for data leaks due to their business nature of storing and sharing sensitive information. Data leaks are the most common result of cyber-attacks. Due to the lack of security used by many law firms, it is easy for hackers to perform data breaches via malware, phishing, and even denial of service.
Reason #2: Phishing scams are most popular
3.4 billion fake emails are sent each day. In 2020, 74% of organizations in the United States experienced a successful phishing attack. It is becoming increasingly difficult to decipher whether an email is a phishing campaign or not due to the growing sophistication in the attacks.
Reason #3: Hacked email accounts is a major problem
There is a hacker attack happening every 39 seconds, and email is the main use of communication for most professional services. Criminals can take over most of your accounts associated with your email once they have gained access.
Reason #4: Lack of security as a priority
Less than half of all law firms in the U.S use some form of encryption software with custom policies to protect their client’s privacy. This means that a lot of your client’s confidential information is just sitting on a laptop or computer unsecured.
Reason #5: Ethical & regulatory obligations are weighing in
To comply with the ABA’s rule 1.6: Confidentiality of Information, lawyers must make a reasonable effort to secure client information. To operate in an ethical manner according to the American Bar Association, lawyers should have security policies in place to ensure the protection of client data.
Bottom line: Cybercriminals love law firms as targets for their cyber attacks. It is crucial for the modern law firm to protect themselves against email-borne threats, and data leaks. ExchangeDefender specializes in law firm data security, compliance, and continuity solutions. The legal industry relies on ExchangeDefender to mitigate risks of cyber and email attacks. We secure your law practice, and protect your clients by eliminating the danger of data breach or ransomware.
What is Phishing? (a simple explanation)

According to recent reports from the FBI, Phishing has become the most common form of cyber attack in 2020 and 2021. Phishing is a method that hackers use to steal your sensitive information like usernames or passwords. It is most often used for identity theft, where cybercriminals send a phishing campaign (via email) to gain access to your bank accounts, personal information, and more.
The goal of a Phishing attack is to: gain credentials like bank pin numbers, usernames and passwords, gain personal data like your name, home address, and email, and also medical PHI information like treatment information and insurance claims.
Where does Phishing happen?
Approximately 96% of phishing attacks are delivered by email. In 2020, it was estimated that 1 in every 4,200 emails was a phishing email according to a Symantec report. To put the numbers in perspective, for ever 1 second of internet activity, 3.4 million emails are sent.
There are also fake websites, social media accounts, and phone calls that are used by criminals to try to steal lucrative information. Beware of these websites, always check for the lock sign in your URL, and make sure that the spelling is correct.
What does Phishing look like?
Inside of a Phishing email you’ll find a malicious link, that (when clicked) will transfer you to a fake website that will request your credentials in the form of “logging in”. Most phishing emails, when you look at the subject lines, you’ll find that the following keywords are present, like:
- Urgent
- Request
- Important
- Payment
- Attention
The email would appear to be from a brand that you trust, like Amazon, Microsoft, or Facebook. The email “from” address is not actually from the brand, but rather faked to appear like it is.
What happens when a Phishing attack has been successful?
2020 Phishing statistics show that about 90% of users cannot identify a sophisticated phishing email. It’s not because we’re dumb, its because the attacks are executed so well. It is becoming increasingly difficult for companies to secure their data because office workers are human, and humans make mistakes. After a successful phishing attack, about 60% of organizations lose their data, 50% are infected with ransomware and get their credentials or accounts stolen.
Need Phishing protection for your business? Keep your company and data safe with ExchangeDefender PRO!
Interested in learning more about Phishing protection, click here.
4 cybersecurity stats that every lawyer should know

Cyber-attacks on the legal sector are on the rise. Legal practices are big targets for hackers due to their access to sensitive information, and severe lack of security.
Here are four statistics that ring alarm bells in the industry:
Number one: One in four law firms have experienced a security breach of some kind. Even more have had malware or viruses according to a 2019 American Bar Association survey.
Number two: Data breaches cost your local small practice an estimated average of $36,000 dollars. To put in perspective, a new legal assistant salary for the year would costs the firm about the same price. Also, at least 31% of their clients terminate their relationship with the firm afterwards.
Number three: 61% of ransomware victims in the legal sector were Law Firms in 2020. It is the highest of the legal profession, with Courts, and Legal Services coming in second.
Number four: 94% of malware and ransomware attacks were delivered by email in 2020. There are new malware and viruses being discovered every day.
The bottom line
Law firms pose a higher risk for data leaks due to their business nature of storing and sharing sensitive information. ExchangeDefender provides affordable email security, email archiving, and email continuity solutions to the legal industry. One of our largest client bases, the legal industry relies on ExchangeDefender to mitigate risks of cyber and email attacks.
Secure your law firm, explore our small business plans today!
Email Security that protects your small business

Running a business isn’t easy, and protecting your business from cyber-threats is becoming increasingly more difficult. Hackers want it all, your personal and business details, your client’s payment information, and so much more! It’s no surprise that small businesses are prime target, about 43% of SMBs lack any type of cybersecurity defense plan. That means almost half of all small businesses don’t have any (cyber) security to protect them against cyber-attacks.
ExchangeDefender PRO is our crowned jewel, our most advanced multi-layered email security suite that protects your business against email-borne threats like SPAM, viruses, malware, phishing, spoofing, and more! Small businesses have smaller budgets, and we understand that which is why our cyber security solution starts at just $5 per user, per month. Adding security to your organization would bring peace of mind as it would safeguard your business against malware and sophisticated phishing attacks. There’s simply no excuse not to protect your business. We tell our clients, if you can afford a Big Mac from McDonalds, you can afford cybersecurity.
ExchangeDefender PRO stops email-borne threats
ExchangeDefender’s powerful email security suite offers a multi-level protection against email-borne attacks. The advanced threat protection features help defend users against threats hidden in emails, attachments, and links. Approximately 90% of all cyber threats originate via email, which requires businesses to have advanced threat protection. ExchangeDefender’s email protection goes beyond the average spam and virus filtering service.
ExchangeDefender PRO prevents data loss and theft
88% of businesses suffer a data breach due to lack of proper email security protocols. Our email protection enables companies to custom their own keyword policies, along with other sensitive data (credit card numbers, social security numbers etc.) they wish to keep private. ExchangeDefender PRO offers complete enterprise-grade threat protection that can help your company defend against the most sophisticated attacks, in addition to the more traditional threats like spam, viruses, and malware.
ExchangeDefender PRO prevents account takeovers
ExchangeDefender Email Protection keeps businesses a step ahead of hackers with AI-based threat detection. Corporate Account Takeovers has costed U.S businesses millions of dollars in 2019, and therefore has become the new focus of security concerns for SMB. ExchangeDefender PRO provides the strongest defense against spear phishing, account compromise and domain fraud. It offers protection to employees from falling prey to sophisticated email-based attacks.
It’s time for you to feel safe with our full stack email security solution, compatible with all major email service providers – including Office 365, on-premise Exchange, and G-suite for business. Get Started for just $5 per user, per month!
Riddled with data breaches, Healthcare needs encryption

The healthcare industry has seen a sharp increase of data breaches since the onset of Covid-19. As we encouraged minimal in-person interaction to minimize the spread, the rise of Telehealth services grew 46% in 2020. It is known that the medical sector has been slower than others when it comes to leveraging new technology. The lack of data security is apparent as 89% of healthcare providers have suffered some type of data breach within the past two years.
So, what’s the deal? Why is the healthcare industry such a big target for hackers?
The healthcare sector mainly consists of businesses that provide medical services, create medical equipment, and develop the drugs that fill our prescriptions. It is a gold-mine for big data that contains sensitive information about patients like date of birth, addresses, medical records, and so much more. Hackers target the industry with data breaches and ransomware to gain full access of medical information of millions of people. 41% of Americans have had their protected health information or PHI exposed in the last three years. The sector’s biggest challenge is managing and securing large volumes of sensitive data. It is extremely difficult to minimize security breaches, and reduce cyber theft when security is not seen as a priority.
Struggling with strict compliance standards
The nature of information that the healthcare industry collects, is subject to some of the strictest data privacy and compliance standards. Healthcare is unique as it manages large volume data that is constantly changing. Complying with data security standards is a major struggle for healthcare as they use Electronic Healthcare Records (EHR), and adopt new cloud technology. Patient EHRs enable doctors to treat via telehealth, and share data digitally which is encouraged by the HITECH act. Unfortunately, many hospitals and clinics have not implemented a secure method of sharing this information which does not fulfill HIPAA standards.
No security training leads to user errors
This is the fact of life, right? Users cannot manage something effectively without understanding how it works. Approximately 90% of data breaches in 2019 were caused by human error, a drastic increase from 61% two years prior. In general, human error is the leading cause of data breach within an organization. For healthcare, about 40% of employees have received no cybersecurity training whatsoever. This lack of security training is costing the medical sector millions of dollars in damages per year, with the average record stolen costing about $400 each.
Empower medical professionals to implement Encryption software
Healthcare professionals can easily send and receive secure messages with ExchangeDefender Corporate Encryption. Personnel can communicate sensitive data with confidence using a powerful, user-friendly web interface that can auto-detect personal identifiable information (PHI) like patient names, date of birth, lab test results, medical bills, and more! It can prevent accident data leaks by triggering custom policies that the organization creates based on security standards. Using Corporate Encryption will automatically help medical workers comply with HIPAA and HITECH regulations.