Enhanced MFA Enforcement Policy: Strengthening ExchangeDefender Security Measures

For years, ExchangeDefender users have enjoyed enhanced login security via multi-factor authentication security (aka MFA, 2FA, OTP). In our March feature update, we hope to improve your security and enhance MFA enrollment to keep you and your data safe. Allow us to introduce to you the new MFA Enforcement Policy!
Note from the boss: Before we get to any discussion of policies, our official recommendation is to enforce MFA on every service we provide and to rotate passwords at least once a quarter. I know, nobody likes the second validation prompt but this is a standard in the industry and I can’t think of a bank or a vendor that doesn’t require it. Maybe I’m jaded because we’re a cybersecurity company.. and with all the layers of MFA/VPN/auth we have in place I spend an insane amount of time trying to find my key or wait for the new pin to display in my authentication app. Because when I interact with a vendor that holds my information and they have no login security.. all I can wonder is what else they’re not doing to keep my data safe? Is this a real business or some WordPress plugin?
At the same time, I understand we have a ton of customers in SMB space where sometimes (obnoxious) tech can be slow and difficult to implement. But you pay us to keep you safe – and to keep your backups safe, and to keep your business continuity safe, and to do that we absolutely must require MFA. But we also can’t expect staff who have clicked on a Release/Trust link for over a decade to be cool with suddenly being forced into MFA enforcement workflow on Monday. So we designed a compromise. I hope it fits your organization and I hope you adopt it as fast as possible.
Sincerely,
–Vlad Mazek, CEO Own Web Now Corp.
In March 2024 you will have the ability to enforce or require MFA enrollment at the domain level. What this means is that you’ll be able to require MFA enrollment with an authenticator app for everyone with just one click at https://admin.exchangedefender.com:
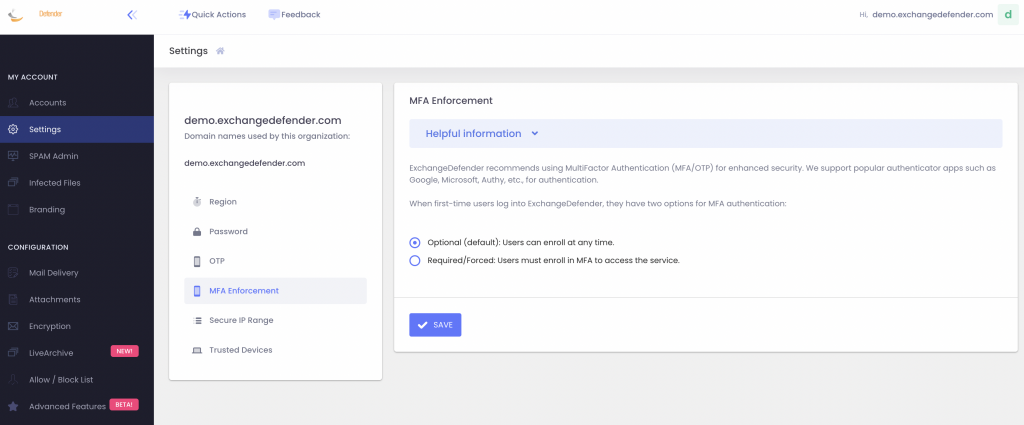
With this policy, you can secure your users’ login with multi-factor authentication without making them enroll a device.
How does it work?
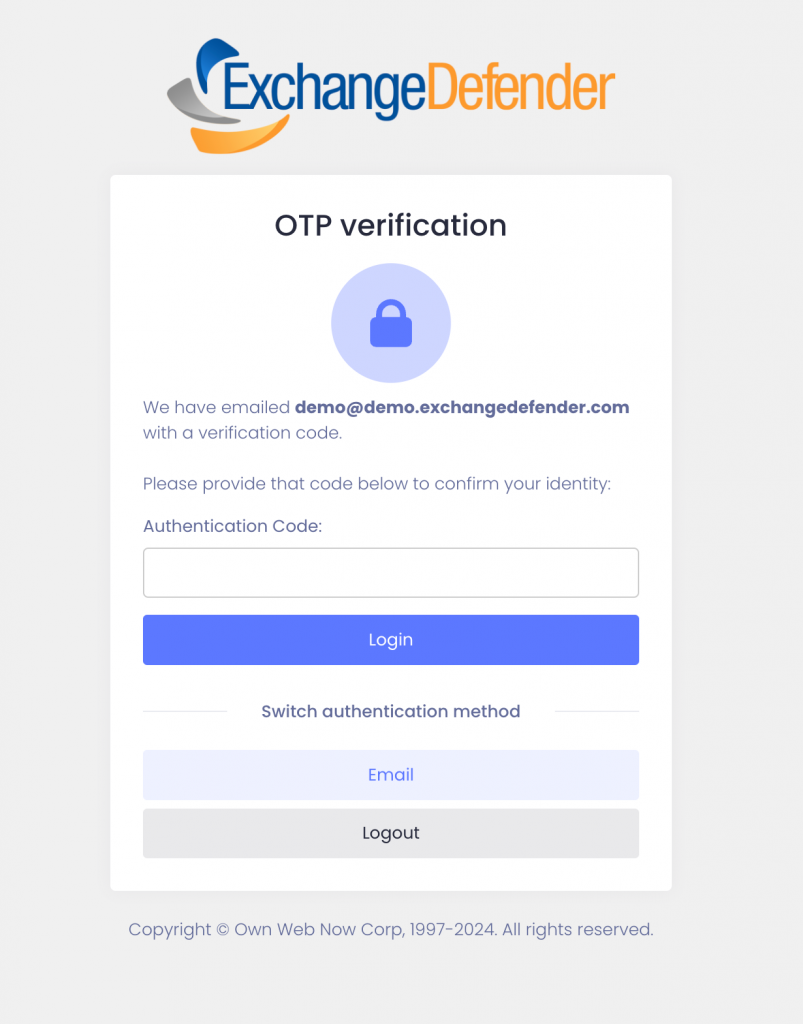
When your users go to admin.exchangedefender.com and attempt to access Inbox, WFS, or LiveArchive we will check their MFA enrollment and if none is found we’ll just tell them we have to verify their identity:
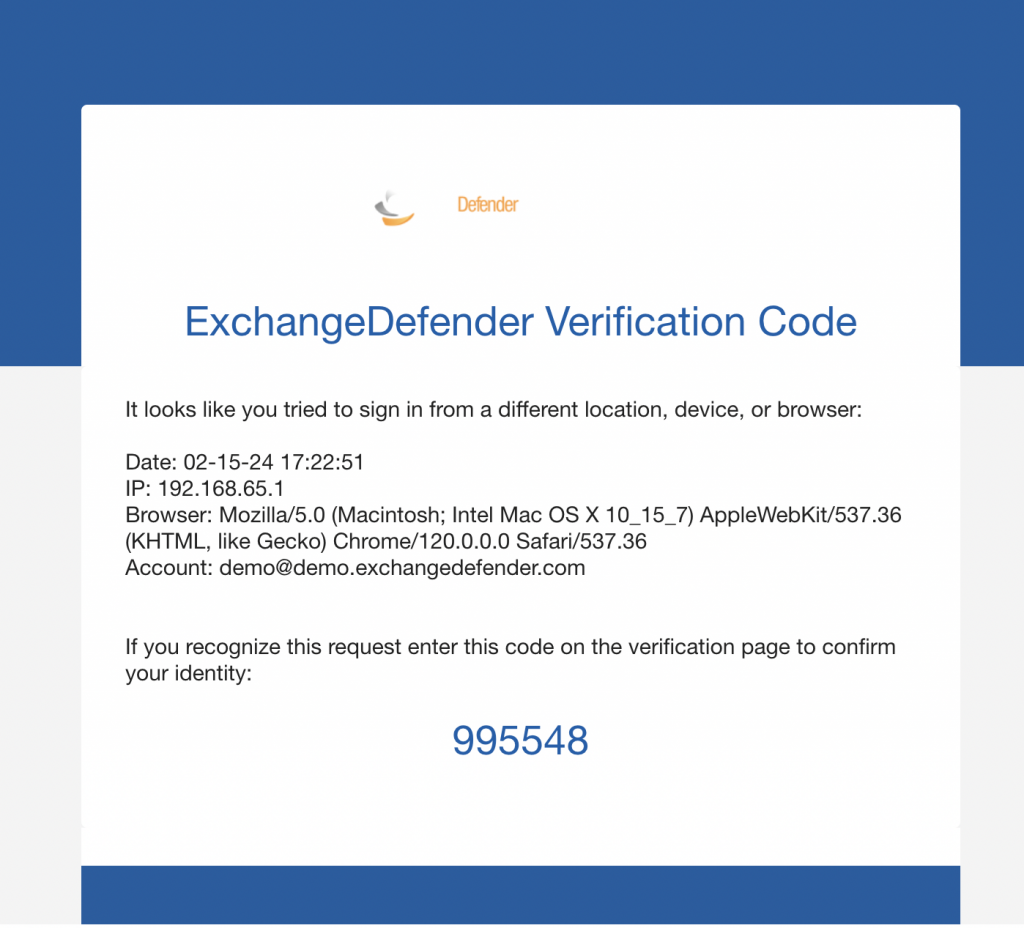
When they check their mailbox they’ll see an email from ExchangeDefender and just provide the code back.
This way your ExchangeDefender login is technically secured at ExchangeDefender with MFA even if you haven’t enrolled a device in MFA yet. There is no way to get into the secure areas of your account without enrolling into MFA. But what if someone guessed the password, they can just enroll a device and hijack the account, right? No.
When you set MFA Enforcement to Required/Forced, all your users are automatically set into an MFA mode that relies on their email address for secondary verification. When they visit admin.exchangedefender.com for the first time and provide their username and password the system will check their MFA enrollment and if email MFA is detected the system will send them an email with a verification code to proceed. This way we’re using the email MFA as a way to verify their identity and then we enroll their authenticator app as usual by scanning the QR code.
ExchangeDefender Quarantine Reports behavior will not change at all as a result of the change in the MFA Enforcement policy. ExchangeDefender Quarantine Reports do not rely on the login system at all as the user is never prompted to authenticate to trigger the release of the message. Instead, quarantine operations are tokenized and one “release” request does not automatically grant any other release or trust requests with the same token. It also doesn’t automatically log them into ExchangeDefender so there is no getting by the MFA!
Secure your logins now
It’s 2024 and the world has changed when it comes to authentication and identity when dealing with services online. Experiencing a cybersecurity threat or compromise is an incredibly expensive and frustrating experience that can easily be avoided by requiring an ID check before granting access to sensitive information. ExchangeDefender MFA Enforcement Policy is your way to protecting your organization from unauthorized and unverified access.
Unlocking the Power of LiveArchive: Exploring the Need for RDS/DB Integration

We’ve had a busy December rolling out LiveArchive with our partners and one of the most common questions that comes up is:
“Do I really need RDS/MariaDB/database service for LiveArchive? Can’t I get away with just S3 if we’re only using it for backup?”
The technical answers to this are “no” and “yes”, respectively. Unfortunately, in the real world both those answers are wrong. Allow us to explain:
ExchangeDefender LiveArchive relies on S3 object storage to store emails which is why it’s required for the service. ExchangeDefender does not require the RDS/MariaDB/database service for deployment – we will still perform the same backup of messages to object storage and place all emails into the appropriate user@domain.com folder. You can still download .eml files and open them with no issues in Outlook and other popular email clients.
Problem:
Unless you know the exact message I’d of the email you’re looking for you’ll have to download the entire user@domain.com directory and use a text search to locate it.
Solution:
Add RDS to LiveArchive so your archive looks more like this:
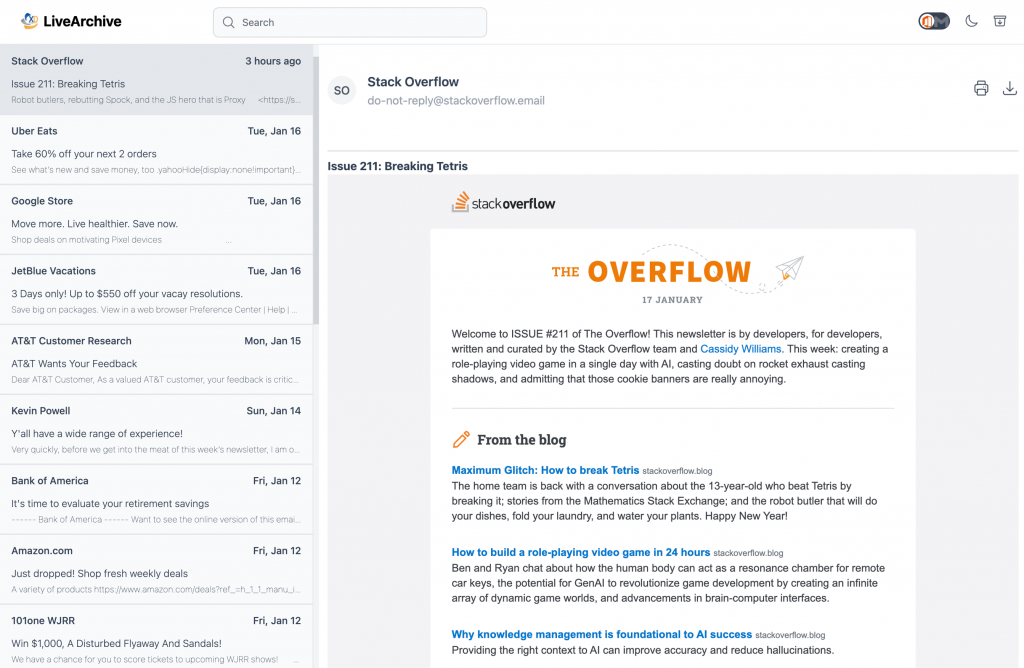
ExchangeDefender LiveArchive uses database services (choice of RDS, MariaDB, MySQL) to store message metadata which contains important message information such as message sender, recipient, subject, and attachments. That metadata is what our ExchangeDefender Web UI relies on to give you a friendly interface to access, search, export, and locate messages quickly in a friendly web interface. ExchangeDefender LiveArchive UI also enables you to filter your message view so you can do eDiscovery: enabling you to limit your search by sender, subject, and date.
We understand why some IT staff would want to do the bare minimum – the market, “nobody is buying stuff”, the complexity, nobody is ever going to look at it – and we hope that the explanation of how database services are used gives you the initiative to deploy RDS. It’s practically free (or totally free if you run it on your hardware) and it will greatly improve your performance, reduce time to recovery, and make it possible to quickly delegate eDiscovery or move data in a format that is open, documented, and will likely be around for decades. Not even tape can claim that! 
What’s the difference between LiveArchive and Inbox?
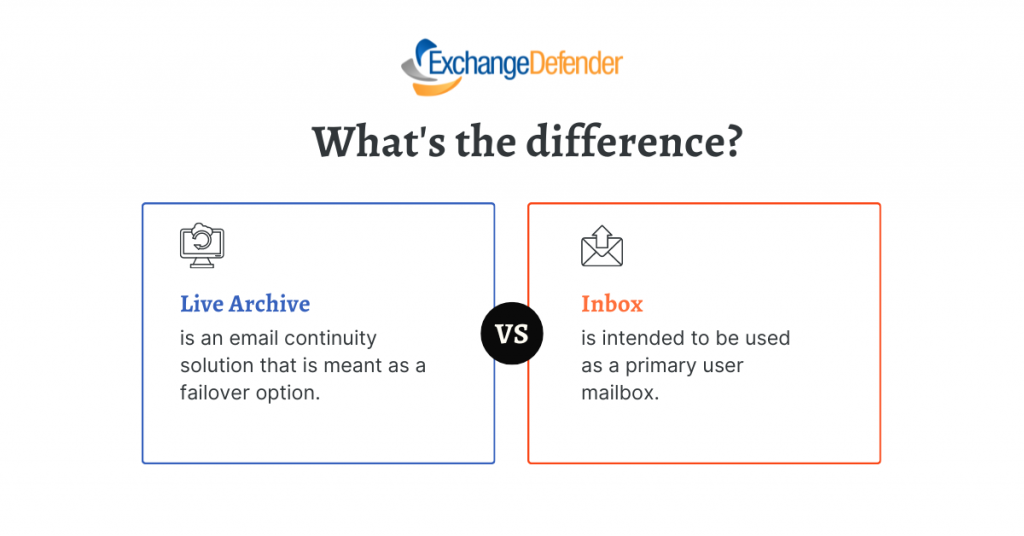
Recently we blogged about ExchangeDefender Project: Inbox and we got a good amount of interest in the beta and just as many questions. We wanted to address the biggest one: What’s the difference between LiveArchive and this Inbox.
The biggest difference is that Inbox is intended to be used as a primary user mailbox, while LiveArchive is meant as a failover for a user whose mailbox is elsewhere (Exchange, M365, Gmail, etc)
Vlad Mazek, CEO of ExchangeDefender
LiveArchive is a great service to rely on when something goes wrong – Inbox on the other hand is meant to be used all the time. LiveArchive is solely a web mail service – Inbox enables you to connect Outlook or mobile devices to it. LiveArchive is a separate web service to which users usually forget credentials or only login when things go down – Inbox is integrated in the admin app and is accessible one click away from the SPAM Quarantines that our users access daily.
They are both great solutions to different IT challenges: LiveArchive for when things go wrong, Inbox for everyday email use. Inbox has one other massive advantage to it that we’ll announce later this fall.
We expect to offer both with ExchangeDefender Pro to reduce support traffic (clients mail tracking requests caused by mail server issues: “It’s in the Inbox”) and because everything in IT can fail and it’s always prudent to have a failover/backup with LiveArchive.
BETA: Advanced Features in Admin Portal
We’re moving things around a little to make the platform easier to use and to expose more of the ExchangeDefender security settings. The threats are only getting worse and we need to be more flexible in order to protect you.
Over the next few blog posts we will be introducing you to a more polished ExchangeDefender look as we consider user feedback and change around the overall user experience. It’s no secret that we’ve been making ExchangeDefender friendlier and friendlier and I can’t wait to reveal why… soon.
In the meantime, allow me to introduce you to the ExchangeDefender Advanced Settings. These settings are controlled under the Domain Administrator section of https://admin.exchangedefender.com:
ExchangeDefender helps bridge the need for security and productivity: If the security tool is too convoluted, takes too many clicks, features lots of paragraphs instead of intuitive controls — it’s simple to see why casual users get their security compromised and experience nothing but frustration just trying to get to their email.
We’re changing all that and look forward to introducing you to the new ExchangeDefender shortly.
oAuth Launch Scheduled for May 19th, 2022
In January 2021 we launched *our oAuth implementation* to help clients get rid of passwords. On May 19th, 2022 our legacy systems (existing email/txt 2FA/MFA) will be shut down and all ExchangeDefender services will rely on oAuth for authentication. Clients will not see a major difference and will login the same way they always have at https://admin.exchangedefender.com:
The new authorization backend will help improve the security of all users that rely on ExchangeDefender to keep them safe: better password policies, no need to reauthenticate every time you visit our services, support for hardware authentication devices and tokens, support for software authentication such as Google/Microsoft/Authy authenticator solutions, and a lot more.
The era where someone can get access to all your data just by guessing or hacking your password is coming to an end. More importantly, industry standards and cybersecurity insurance underwriters are requiring 2FA/MFA and this is a huge opportunity for our partners to deploy a more secure access to the arguably most insecure and public endpoint in every organization: email.
We look forward to keeping all your data secure and your users safe from dangerous email exploits.
ExchangeDefender CEO talks email-borne threats with Cybernews
Recently, Cybernews reached out to ExchangeDefender CEO, Vlad Mazek to learn more about how we keep businesses safe from cyber-attacks using top of the line security solutions. The informative discussion centers around the topic of cybersecurity, and what that means for the modern business.
With the recent rise in phishing attacks, it is smart to double-check if it’s really your coworker that emailed you.
By now, it’s probably hard to find an Internet user who has never received emails from someone claiming to be a long-lost relative who wants to share their fortune. While the majority of us are familiar with this type of malware, phishing attacks shouldn’t be underestimated. Nowadays, when threat actors start to include more personal details, posing as coworkers or even bosses, staying vigilant is key.
To discuss the topic of cybersecurity and phishing prevention, we reached out to Vlad Mazek, the CEO of ExchangeDefender, a company eliminating email threats before they even reach your inbox.
ExchangeDefender has been providing various security solutions for more than 2 decades. What was your journey like throughout the years?
We originally started ExchangeDefender to improve the reliability of our Microsoft Exchange servers by offloading all the security tools to a more scalable infrastructure. Over the years we’ve expanded our security portfolio to protect other email servers, as well as deliver more secure ways to rely on common office tasks such as file sharing, collaboration, and compliance.
Can you tell us a little bit about what you do? What are the main problems you help solve?
We used to say “We kill SPAM for a living” and to this day we simply eliminate common threats that lead to security compromises and service outages by providing email encryption, long-term archiving & eDiscovery.
We make it easier to rely on email for secure and reliable communication; which we do by keeping potentially dangerous content away from your webmail, mailbox, desktop, or phone. Simply put, we make it easy to get things done more securely.
What technologies do you use to detect and stop threats in their tracks?
We primarily rely on our internal early warning system which tracks unusual activity from known threat actors. Because of our size and client base, we often have the luxury of being among the first to be targeted which helps us identify safe and unsafe developments before they go “viral”.
We also participate in many proprietary, open-source, and data/intel sharing projects that help raise the security profile of everyone involved.
How did the pandemic affect the cybersecurity landscape? Were there any new features added to your services?
Pandemic actually improved the security landscape for our clients because they suddenly had to shift to a remote work model which inherently came with more stringent security requirements and more awareness for security policies and secure collaboration.
We noticed a significant shift from traditional office communication methods to SMS/TXT and we moved quickly to make all of our services SMS-aware. Mobile phones have become a security identification token, a mobile presence device, and far too often a failover computer. That’s why we invested heavily in extending our services to meet our clients’ needs to go beyond just sending email messages.
What sectors (for example, financial, healthcare, etc.) do you think should put extra attention towards email security?
The best way to answer this question is to think like a hacker because for them it’s not personal, it’s business.
Organizations get compromised for one of two reasons:
- They have assets (data) that are valuable
- They have a reputation that is valuable
If you have a lot of valuable data or a trustworthy relationship with your clients, you’re a valuable target regardless of your industry. It would be difficult to hack a financial institution because they have dedicated IT and security teams, go through routine audits, and can respond to threats quickly. Compare that to a small CPA firm that uses standard tools and an antivirus bundle that came with their PC.
When it comes to cyber threats carried out via email, what are the most common ones?
Email is the most popular way to get cyber threats into an organization, according to a recent study over 90% of security compromises started with email and it has not changed significantly in the past few years: the #1 cyber threat is from spear phishing. Spear phishing is a practice of forging the identity of the sender and the look of the email to something the recipient would find trustworthy enough to click on. What has changed significantly is the end goal of spear phishing:
- Deployment of RAT (Remote Access Trojan) software
- Theft of PII (personally identifiable information)
- Theft of security credentials
This list actually flipped in the last two years mostly due to the sophistication of RAT software that can give an attacker access to the entire network instead of just a single PC or cloud account. The latest variants target UEFI bios which keep the threat in place even after you get rid of the infected hard drives. As these threats evolve, they also highlight other security issues on the network which makes them difficult to remove and require constant monitoring.
With so many teams working remotely nowadays, what are the best practices when it comes to secure file sharing?
The single most important recent advancement in overall IT security that really deserves wider adoption is the use of MFA/2FA/OTP: multi-factor authentication that requires secondary verification before accessing any sensitive system or information. Working remotely, outside of a managed network and access to IT staff, creates a new universe of security threats that should be mitigated by:
- Deploying & requiring MFA for access
- Deploying a more aggressive backup and imaging solution
- Controlling and reducing the attack surface (by limiting access only to required web sites & services)
Besides secure collaboration solutions, what other security measures do you think modern companies should invest in?
You are probably already spending too much on overlapping, redundant, and underutilized security solutions.
The best security investment you can make today is to get an audit of your existing security portfolio and its integration. Being secure doesn’t come simply from paying for a security software/service license – it has to be properly integrated, configured, and monitored in order to truly keep users away from dangerous content. Due to the chronic lack of security focus and the habit of deprioritizing security for the sake of end-user comfort, many organizations find themselves in a perilous situation with cyber insurance demands.
We are seeing organizations getting compromised not because they don’t have security solutions or adequate training but because they don’t take the time to properly and fully implement the security solutions they are already paying for. An overwhelming majority of ExchangeDefender subscribers rely on less than 30% of the security features they already pay for.
Can you give us a sneak peek into some of your future plans for ExchangeDefender?
Our biggest technical investment for 2022/2023 is to make it possible to access external content (email attachments, files, messages, sites & services) in a secure online sandbox environment where dangerous content wouldn’t even have a chance to reach the user’s desktop, phone, or network.
Our biggest investment is in the area of security audits and assessments. While there is always a shiny new tool or service that promises better security, our data indicates that it’s rarely the lack of a tool, and more often the lack of proper deployment and management of sensitive information that leads to a security compromise.
We’ve helped countless businesses that have been compromised over the years and it usually comes down to neglect of security processes combined with a lack of a plan to respond and recover from a hack. Our future plans are to help organizations change that scenario because cybersecurity isn’t something you buy, it’s something you do.
To celebrate the launch of our new small business service plans, we are currently offering 30-day free trials for any service. Interested in ExchangeDefender? Please visit www.exchangedefender.com/business to request your free trial today!
NEW: ExchangeDefender SPAM Manager Desktop App

We have been working on something cool based on the feedback from our clients. It’s a multi-platform app (Windows, Mac, Linux) that reminds you to check your SPAM, and when you do the message is just one click away – making it just as productive as Outlook & Outlook Web App.
It’s also a lot more secure.
Our portal remains the #1 way clients interact with ExchangeDefender at https://admin.exchangedefender.com. Most people already have it bookmarked. But for those that need a little extra push, a reminder (every 5/15/30/60 minutes) that there is SPAM waiting, a desktop notification, a secure way to access, read/reply/forward/delete the message – for you we have the ExchangeDefender SPAM Manager app:
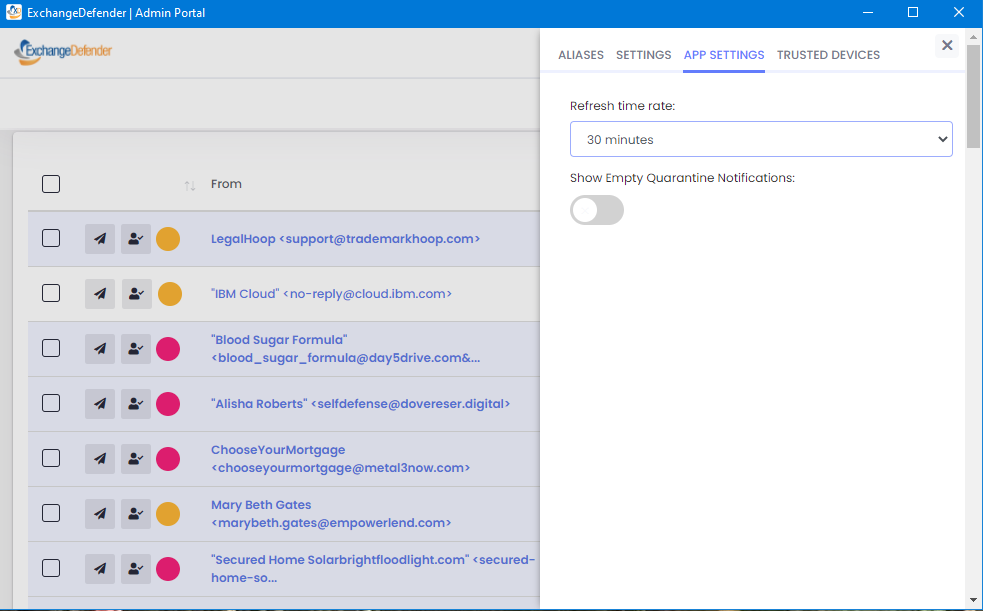
If you have users relying on the legacy ExchangeDefender Quarantine Email Reports, this is it’s new secure version.
We are currently wrapping up beta testing the app across all three platforms, if you’d like to take a look please open a ticket at https://support.exchangedefender.com and we’ll send you the link!
Essential file sharing tips from the professionals

When file sharing via the cloud became the norm, it revolutionized how we collaborated, and how we got business done. File sharing enables numerous people to have access to the same file(s), and be able to read, view, modify, or print it. Storage included, file sharing allows you to share files with anyone, and is the most common way to share large files. The increase ease of collaboration has made it easy for us to forget that the information we share at work must be handled with great care due to its sensitive nature. To make sure you’ve got the essentials to share safely, we asked our file sharing professionals what they think is most important when it comes to sharing via the cloud with others.
#1 – Use a secure file sharing platform
This tip is probably the most important. You’ll want to choose a secure file sharing service that is enterprise-grade had offers end-to-end encryption. This level of security will keep hackers away, and prevent them from stealing or viewing your data. ExchangeDefender’s professional file sharing software allows users to upload, manage, and share files securely using 128bit encryption for data protection. It also offers security settings for users, and advanced security controls for administrators.
#2 – Set permissions on your files and folders
It is crucial for administrators to control access to files and folders that include both important business information, and confidential client information. A good file sharing platform will allow you to apply restrictions or rules to files or groups of people. This will limit the information from being viewed or shared by the wrong individuals. Essentially, admins can control access by creating restrictions as to what a user can do, like the ability to view, download or delete files. ExchangeDefender Web File Server enables you to password protect a library, set automatic expiration dates, and even receive email notifications when new files have been added by coworkers, or downloaded by your clients.
#3 – Always check the file activity
Just like you check your bank account daily, or every few days – you’ll want to check the activity occurring inside of your file sharing software. Make it company policy to run an audit on your files weekly to see who has been accessing company resources. Reviewing your library frequently will allow to stay on top of the permissions you’ve set, and also determine whether certain files are no longer needed. A great file sharing system should give you detailed access to security and activity logs – this way you can instantly know who did what, and when.
#4 – Train employees on how to share
No doubt you’ll want the actual software to be easy to use, and the ability to quickly adopt for the whole organization. The next step after is to train and educate your coworkers on the importance of file sharing sensitive information at work. There are many risks associated with mishandling confidential information that could cause the company, or your client a lot of damage. Be sure to create clear rules on appropriate ways to share information with external parties. A good way to get everyone on board, is once you’ve invested in a secure file sharing software of your choice, have a lunch and learn together and go through the main features and daily functions you’ll be using.
#5 – Keep it in the cloud
At this point, everything that’s new is located in the cloud and its for good reason. The Cloud makes things easy, much easier. A quick implementation is crucial for the office, and a cloud solution is the way to go to make that happen. The right file sharing service will provide your workplace with the perfect setup that is easy to use, manage, and experience growth.
ExchangerDefender Web File Sharing makes it easy for teams to share documents without having to rely on email, or old file servers. Try for 14 days free!
ExchangeDefender Advanced Features & Policies: Bulk Mailer Policy
Today, we are excited to showcase our brand new feature: Bulk Mailer Policy. This new feature was first announced last week as part as the new release of ExchangeDefender Advanced Features and Policies. (It is available to all of our ExchangeDefender PRO clients.) Bulk Mailer Policy simplifies process of blocking or allowing mail from bulk mail operations that are increasingly used by developers and hackers alike to relay mail.
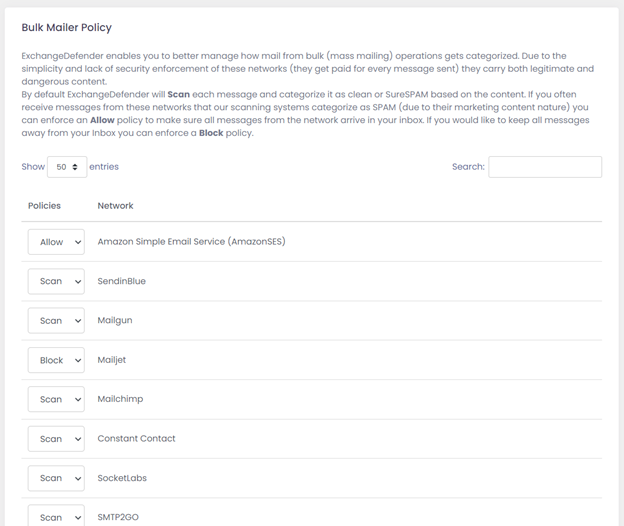
Bulk mail operations, such as AmazonSES and Sendgrid, are large scale SMTP networks designed to enable developers to reliably deliver and manage email subscriptions. As such, bulk mailers generate a new sender email address (envelope-from) that the mail would bounce to if the message could not be delivered for any reason. Every time an email goes out a new sender bounce email address is created by the sender – solely for tracking the delivery and activity of that one message. Long story short, it makes it very frustrating to build a policy against something that is random and changes often.
ExchangeDefender Bulk Mailer Policy simplifies that process by maintaining a list of IP addresses the network is using (as defined by their SPF record) to relay messages. There are three options:
Scan – This is the default policy; every message is scanned by ExchangeDefender for SPAM content and it gets flagged as SPAM/SureSPAM if it looks like SPAM.
Allow – This policy will result in ExchangeDefender not scanning any mail from this network for SPAM content (viruses, malware, etc are still considered) and delivering it automatically.
Block – This policy will result in ExchangeDefender automatically labeling the message as SureSPAM.
The Bad:
Bulk mail sending networks have minimal requirements for subscription/use, and many are actively abused to relay dangerous content.
The Good:
The main benefit of this feature is that ExchangeDefender is actively tracking IP address blocks associated with each network, minimizing the amount of time IT has to spend managing allow/block policy.
ExchangeDefender Advanced Features & Policies are available at https://admin.ExchangeDefender.com and should be setup and managed by a competent IT staff that can manage the entire scope of the policy. The issue with bulk mailer networks is that they are massive, easy to access, and often tied into shared hosting environments that are frequently compromised – what makes them convenient is what makes them dangerous. Unfortunately, if your 2FA/OTP or web site developer uses such networks, you have no choice but to allow the traffic through, and ExchangeDefender makes that easy! We make it just as easy to block them. Whether it should be enabled or disabled, and how, is something that each organization will have to assess and consider along with other cybersecurity policies that need to be in place.
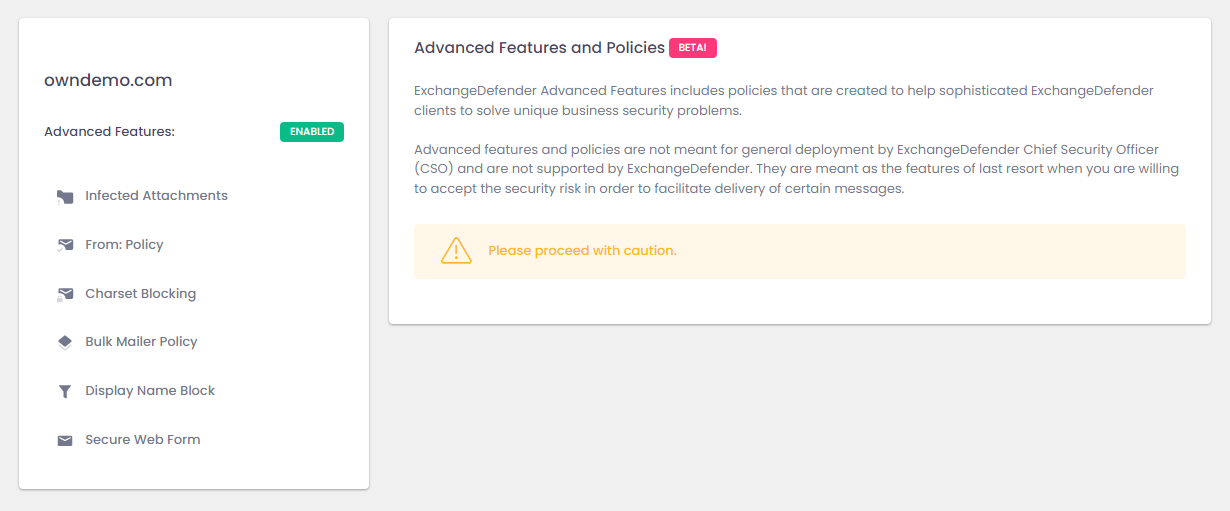
ExchangeDefender Advanced Features & Policies
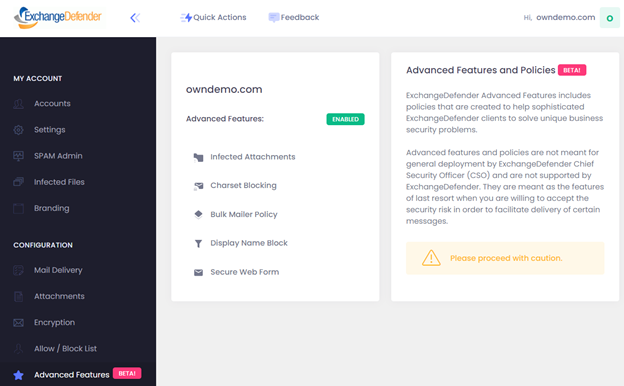
ExchangeDefender is pleased to announce the launch of Advanced Features and Policies, available to all our clients at https://admin.exchangedefender.com. These advanced features are meant to help sophisticated IT personnel establish policies for unique business case scenarios, and better protect their clients from email threats.
Advanced Features & Policies features are available on the Domain Admin section of our administrative portal at https://admin.exchangedefender.com. All features are disabled by default, due to their complexity, and must be enabled by the Domain Admin.
Note about support: ExchangeDefender technical support is available to assist with these features 24/7/365 at https://support.ExchangeDefender.com. We are always happy to help point our clients in the right direction when considering these features. We do not provide troubleshooting or policy analysis for these features, however, as many of these features will by design enable ExchangeDefender to override established IT security best practices. We don’t recommend them, we do not support them, but as always we will attempt to help out and secure the client.
Features at a glance:
Infected Attachments – This policy enables Domain Administrators to allow users direct access to infected or blocked email attachments.
Charset Blocking – This policy enables Domain Administrators to block emails with specific character sets from reaching the Inbox.
Bulk Mailer Policy – This policy enables Domain Administrators to override ExchangeDefender scanning for top 10 mass mailing networks (AmazonSES, MailChimp, Sendgrid, etc)
Display Name Block – This policy enables Domain Administrators to block messages with specific sender names from reaching Inbox.
Secure Web Form – This policy enables ExchangeDefender Encryption clients to receive secure/encrypted messages from third parties.
All of these features were developed with the help of our partners and clients who were experiencing unique issues that ExchangeDefender and other cybersecurity solutions/devices do not address. The hackers are advancing faster than IT can cope and we hope some of these features are as helpful to you as they were to other clients of ours that just needed to “make things work” and ExchangeDefender is always easy to reach.
As we continue to build ExchangeDefender we anticipate to introduce more Advanced Settings that would enable Domain Administrators to build a more powerful security wrapper around their email experience. To get more information about these features please watch our last webinar (available at https://support.ExchangeDefender.com) where our CEO explains the motivation and implementation scenarios.