Documentation
DMARC
Introduction to DMARC
ExchangeDefender is fully compliant with DMARC email authentication protocol and actively implements open standards such as SPF and DKIM to assure authorized email delivery.
ExchangeDefender supports SPF and DKIM validation and enforcement for incoming messages, and from November 1st, 2021 actively signs all outbound/sent mail with DKIM. These features assure our clients domains are protected from email spoofing and forgery, while mail that does not comply with senders DMARC (SPF/DKIM) policies is routed/returned appropriately.
To find out more about email authorization standards like SPF (https://en.wikipedia.org/wiki/Sender_Policy_Framework, Sender Policy Framework), DKIM (https://en.wikipedia.org/wiki/DomainKeys_Identified_Mail, DomainKeys Identified Mail) and how they are used to achieve DMARC alignment (Domain-based Message Authentication, Reporting and Conformance, https://en.wikipedia.org/wiki/DMARC) to prevent unauthorized email delivery (https://en.wikipedia.org/wiki/Email_spoofing, spoofing) please check out RFC 7489 (https://tools.ietf.org/html/rfc7489).
ExchangeDefender DKIM Implementation
ExchangeDefender fully supports DKIM for both incoming and outgoing mail. On the incoming side, we verify DKIM signatures. On the outgoing side, all your sent mail going through ExchangeDefender will be signed with a 2048-bit key allowing others to confirm no one has forged mail from your domain or tampered with messages while en route.
Inbound DKIM implementation is automatic and fully transparent to the user. If the senders email server is having a problem with DKIM signatures (not DMARC) and messages appear forged/tampered with, they will be accepted by ExchangeDefender and users SPAM policy will determine if the message is delivered, quarantined for review, or deleted.
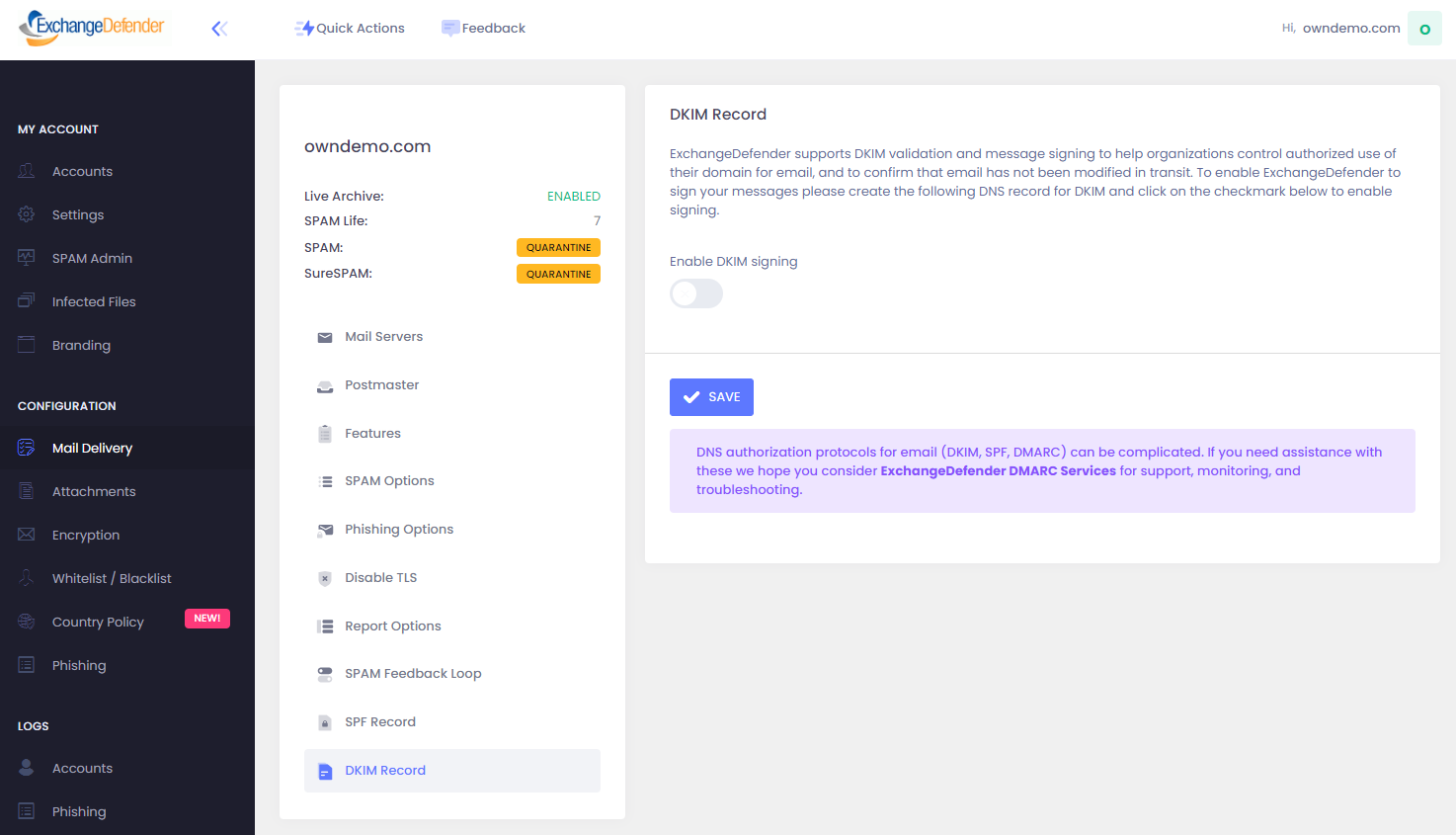
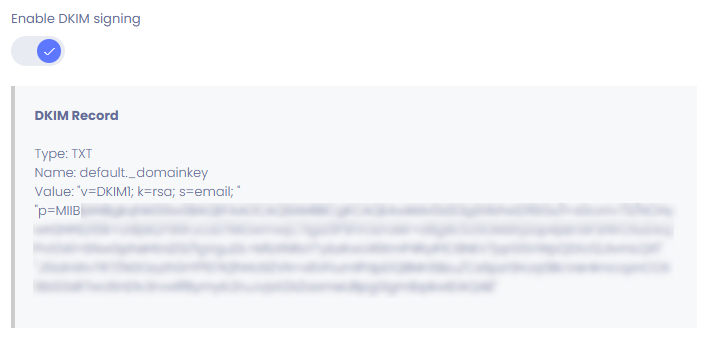
Outbound DKIM implementation is optional and can be enabled or disabled by Domain Administrators on demand at https://admin.exchangedefender.com. Click on Mail Delivery, DKIM Record, and Enable DKIM Signing.
After enabling DKIM signing, your public DKIM key will be provided immediately and ExchangeDefender will begin signing outbound messages within one hour.
DKIM Deployment
ExchangeDefender provides a universal DKIM key in DNS via CNAME record. Instead of manually crafting a DKIM TXT record, customers are able to simply CNAME default-dkim.proxy.exchangedefender.com
You will need to contact your DNS administrator and request that they create the following DNS record for your domains:
Record type: CNAME
Host: default._domainkey
Target/Value: default-dkim.proxy.exchangedefender.com
If your domain is already using the default domain selector, you can use the alternate CNAME DKIM selector: exchangedefender.
Record type: CNAME
Host: exchangedefender._domainkey
Target/Value: exchangedefender-dkim.proxy.exchangedefender.com<
Please note: some CNAME records require a period "." at the end of the CNAME target.
Advanced Deployment
You can optionally deploy a DNS TXT record directly if you are unable to use the default CNAME record. This method is no longer recommended over the previously mentioned CNAME method as TXT records are more prone to input errors. Customers are still able to generate unique DKIM keys for their domains if necessary (for example, to comply with regulations)
Ask your DNS administrator to create the following DNS record for you:
Type: TXT
Host: default._domainkey
TXT Value: (value from admin.exchangedefender.com from the previous step)
DKIM Validation
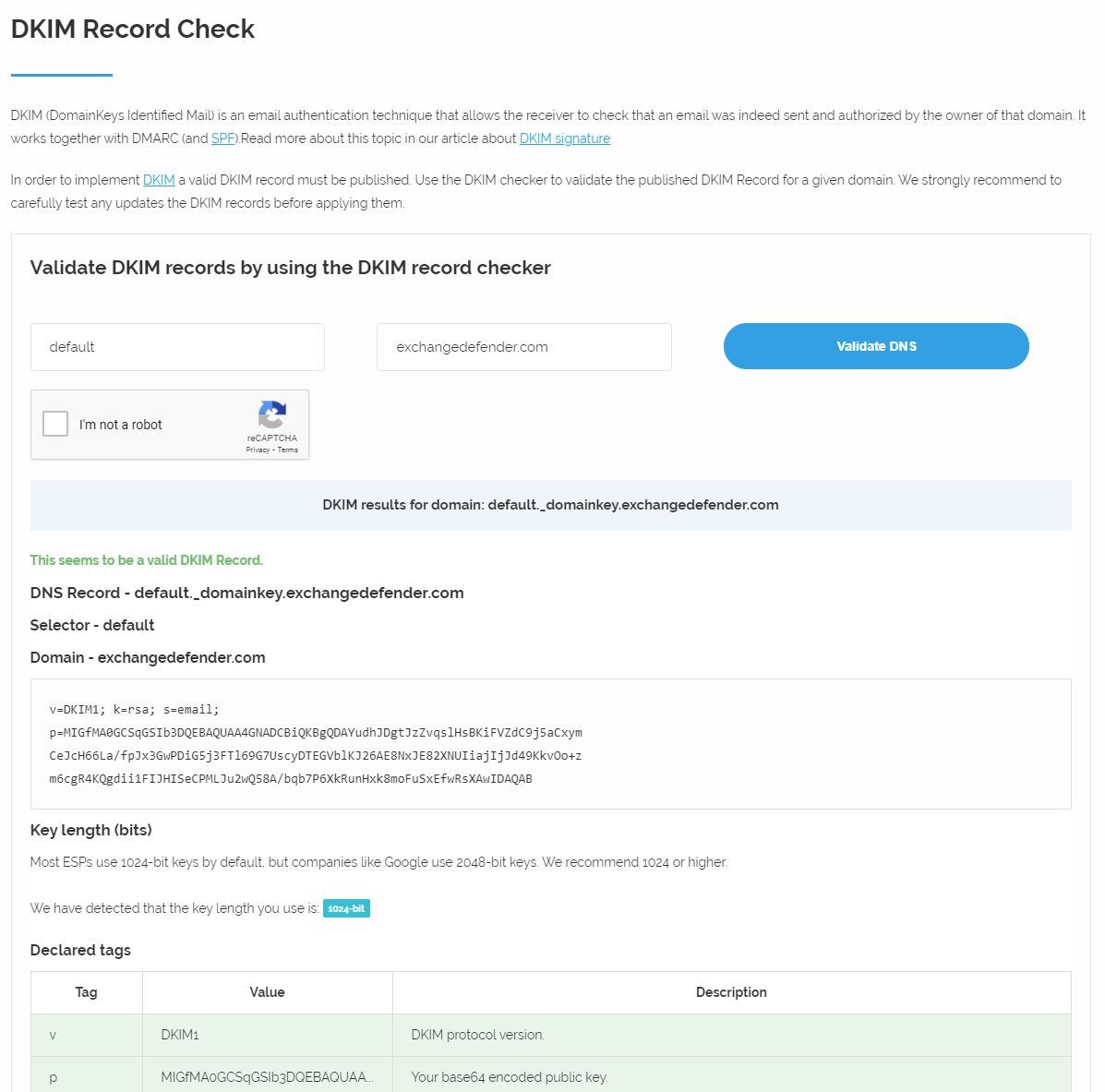
After your DNS admin has created the DKIM record, please go to this site to validate it:
https://www.dmarcanalyzer.com/dkim/dkim-checker/
Select default for hostname and your domain name and click on (Validate DNS)
If your domain DKIM is validated, you're all done.
If your validation fails for any reason, contact your DNS administrator. ExchangeDefender will not be able to assist / troubleshoot any DNS-related issues as have no control over how the DNS administrator manages the domain. In general, if there is an issue with the DKIM it's due to parsing / maximum key length in the DNS providers configuration. Some may require you to break up the key into two records, it is best to consult your DNS host for the best way to create the DKIM record.
ExchangeDefender SPF Implementation
ExchangeDefender supports SPF and makes it easy for clients that route their outbound mail through us to implement SPF. ExchangeDefender has a public SPF record that can easily be included or used exclusively with the following TXT record:
“v=spf1 include:proxy.exchangedefender.com -all”
If you already have an existing SPF record, you can simply add “include: proxy.exchangedefender.com” before the SPF policy decleration (~/-/+all)
It is recommended that you contact your DNS admin / host for assistance with DNS records; If your current DNS provider is unable to assist you, we can offer to migrate you to our Managed DNS service.
Using bypass.exchangedefender.com to work around DMARC problems
DMARC problems are not frequent, but when they do appear due to shadow IT or even a simple mistake in senders DMARC configuration, they can be a nightmare. ExchangeDefender fully implements DMARC and if the senders policy is a strict reject (p=REJECT), ExchangeDefender is required to reject the message. Messages that have been tampered / forged / unauthorized by DMARC policy never reaches our antispam controls, it is not possible to “whitelist” a message because the message will not be accepted.
We realize there are business case scenarios where compromising security for a one-off messages is required. In order to accomplish that, ExchangeDefender offers a bypass service which is included free with your ExchangeDefender Pro subscription. The ExchangeDefender Bypass Service (bypass.exchangedefender.com) allows you to generate a disposable email address that can receive a message (or multiple messages) without any security precautions. Being able to create, enable, and disable these addresses on demand (which cannot be guessed easily) can help you accept messages in the short term while the sender is alerted to the problem and given a chance to address it.
ExchangeDefender DMARC Services
ExchangeDefender clients benefit from a platform that fully implements SPF, DKIM, and DMARC solutions for mail going to and from your organization. Furthermore, ExchangeDefender Pro subscribers have access to our bypass.exchangedefender.com (https://bypass.exchangedefender.com) to work around domain owners who have misconfigured their SPF/DKIM/DMARC policies and still get the mail delivered to our clients.
We know that DNS and management of authorization protocols can be complex. If you need any assistance, or would just like ExchangeDefender to handle all of this for you, please contact us about ExchangeDefender DNS subscription service.
ExchangeDefender Policy
While we encourage all of our clients to implement both SPF and DKIM, we understand that there are sometimes business scenario cases under which this is impossible. If you find yourself in this predicament you should immediately change where your name servers are hosted and take full control of your organizations identity online. But if that is still something you may not be able to do, ExchangeDefender can still protect you from phishing attacks and spoofing launched using your own domain name. If you’ve ever received email from yourself or from a colleague (but the email actually came from a server in Poland) then this setting will help you.
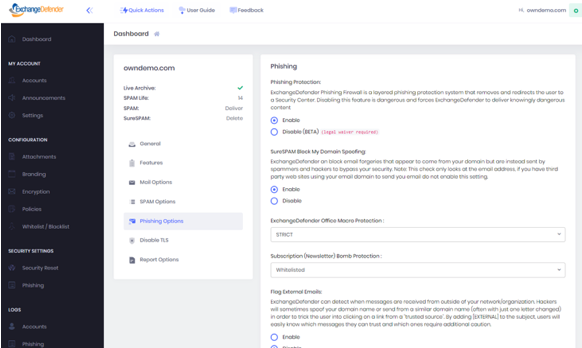
Go to https://admin.exchangedefender.com and login as the domain administrator (username is your domain name).
Click on Security Settings > Phishing
Under “Flag External Emails” click on Enable and then Save.
After this setting is applied, all messages from your domain that were sent from outside of the ExchangeDefender network will go into the SureSPAM quarantine. Just tell users not to trust, whitelist, or release messages that are coming from your own domain because they are certainly not legitimate.
Frequently Asked Questions
How do I whitelist DMARC rejection?
There is no way to whitelist DMARC rejections because messages are not processed by ExchangeDefender. If the organization has a DMARC p=reject policy, ExchangeDefender is not in control of that policy and it can only be fixed on the sender side. While you can whitelist domains that have an invalid DKIM or SPF records, DMARC is unique because it requires us to not accept forged messages.
To work around this protocol limitation, please use the ExchangeDefender Bypass Service: https://bypass.exchangedefender.com
Can I use a selector other than default?
Domains are permitted to have an unlimited number of DKIM keys, partitioned by a "selector." DKIM selector's are DNS TXT records used to match the DKIM signature of the message to its respective DKIM public key published in DNS. Email messages signed with DKIM will contain a reference to the DKIM selector that must be used to verify the authenticity of the message. Common practice in the industry is to use a selector named "default" for the first record, however, as previously mentioned, domains can have many DKIM keys and the selector used is specified when signing the message. There is no requirement that DKIM records must use a selector named default.
If your domain already has a default record published you can use the alternative record below which uses the selector exchangedefender. Just replace $YOURDOMAIN$ with your domain (if your domain name is wrkoo.net, the record will be: exchangedefender._domainkey.wrkoo.net)
Host: exchangedefender._domainkey.$YOURDOMAIN$.com
"v=DKIM1; k=rsa; s=email; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAugDL9DDLQCigkcAntWad9gRUlJ9UT1LHJOcvxbUMQUB2dGkn0JSDTnfaLpMW8BKGxVKHTgLk4/TAGLY+R0Lg+bc3ZiwG32SjKwJWRSlwN5CwIQKNj1f07JThxHHR0nKlp3oph1+CZcuyiZo5/KwfI4g7Tv77wU+WX0RACkuutH+W/Y9nLXZ8SsnpKrONIgygDJzbjfTicKUYdt4NGaei9gimrax25x7Zkpav8RiG+Qx1csnzYwQ2zXx/wbpTm9IYDPDKf70bAtDYcJONPtx7AGDb+d/sWPgbxfHQ9MP5hZs0q4w41cjoCNHntG8s1Xgr6lNtVg7WQ0Pfu6T5hRSMcQIDAQAB"
I have compliance requirements and need a custom DKIM keys.
If you have specific compliance requirements or key requirements, we can assist you. Please contact us with the specific inquiry or open a support request at support.exchangedefender.com.
There is a one-time $300 setup fee for custom record setup and $100 for maintenance. For more advanced requirements such as daily key rotation, DNS must be hosted at ExchangeDefender or approved DNS provider.
What is wrong with my DKIM record? It fails validation.
Please contact the company that currently manages your DNS (you can locate them at lookup.icann.org) and tell them you need help creating a 2048-bit TXT record.
Every DNS service and DNS control panel have their own specific limitations, gimmics, gotchas, and restrictions. Any mistake can cause the entire record to fail, impacting all of the operations (email, web, ecommerce) that rely on DNS. ExchangeDefender support staff is not allowed to guess and are required by process to advise you to contact your DNS provider. As mentioned before, if you cannot get your current DNS provider to help we will help move your DNS to our infrastructure where we have control and ability to support/warranty the work.
That said, DNS/DKIM issues fall into 3 categories:
1) DNS provider doesn't support >1024bit keys. Solution: Move to another DNS provider that does (Cloudflare, Hurricane Electric)
2) DNS key value doesn't support spaces/quotes/etc. Solution: Try removing all quotation marks, spaces, etc from the p= section of the DKIM record.
3) DNS key is too long for the control panel. Solution: Some control panels allow chunking, or splitting of the DNS record into separate keys.
In all 3 instances, you will need to contact the DNS provider for resolution. All ExchangeDefender does is issue the public key and we're certain it works. Go ahead, validate it yourself:
nslookup -q=txt default._domainkey.demo.exchangedefender.com 8.8.8.8
Server: 8.8.8.8
Address: 8.8.8.8#53
Non-authoritative answer:
default._domainkey.demo.exchangedefender.com text = "v=DKIM1; k=rsa; s=email; " "p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAwkMvl3dS3g9XbhxtD16tSx/l+s0cxVv73/NCHywH2HFED61k+orBj4QY96FJcUD7MOwmwjC7Igtz5P9fVOLFoMr+d8g8c5J5OIA8Xj2ap4jsEnSF3rRrCNJDxojPvtGA1+ENwGpheHtniZG/fgVguDL+M1zXNRsYTybzKwU49tmP4RyIFIC8NEV7jqrGSVWpQSXc12JlvmLQX1" "J5tdnWvTR7/NGOzyth0rYP1STKj1hHU9ZVN+x8VFiumlPdpDQBMn5Bzu/Cs6pzrSHJqGBcVer4mccpnCOX9bG3sR7wU6nDIv3rvwIlfBymylcZruJvjsXZAZaameUBpgGgmibpkwIDAQAB"
How can I get DNS support?
To obtain DNS support, you will need to contact your DNS administrator or DNS registrar. If you do not know who that is, please go to https://lookup.icann.org, type in your domain name and scroll down to Registrar Information. Each DNS provider has their own setup / control panel / policies and should be consulted for any DNS related issue.
ExchangeDefender Support is prohibited from offering DNS troubleshooting or advice, all we will be able to provide you with is the public record (https://toolbox.googleapps.com/apps/dig) and this document. If you are unable to make any progress with your current DNS provider, we can offer to migrate you to ExchangeDefender Managed DNS.
Is DMARC only required if we send mail through ExchangeDefender?
DMARC is required if you use ExchangeDefender in any capacity.
DMARC, with restrictive SPF and 2048-bit DKIM, is required for ExchangeDefender (whether you only use us for inbound, outbound, IoT, Encryption, LiveArchive, Compliance, Enterprise Mail Services, etc). Because our infrastructure is also subject to attack when your domain gets hijacked and massive NDR/bounce broadcast storm begins, DMARC is required.
What happens if we don't comply with DMARC requirements?
Effective November 1, 2021, ExchangeDefender domains that are not deployed correctly according to the Deployment Guide and DMARC Guide will no longer be supported by ExchangeDefender. Because lack of DMARC often gets domains added on internal blacklists (that are not published), ExchangeDefender will not offer any assistance with the domain for thirty (30) days after the domain is brought into compliance.
Lack of DMARC compliance will also eventually result in bounces, delivery errors, lower security profile. There is no technical reason for ignoring DMARC compliance requirements and ignoring it is dangerous