ExchangeDefender Corporate Encryption: New Features

ExchangeDefender Corporate Encryption
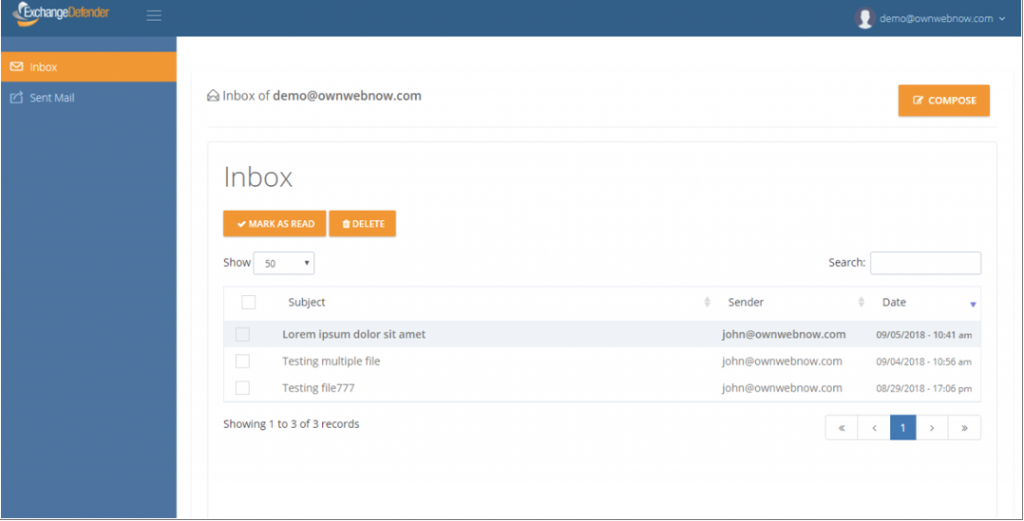
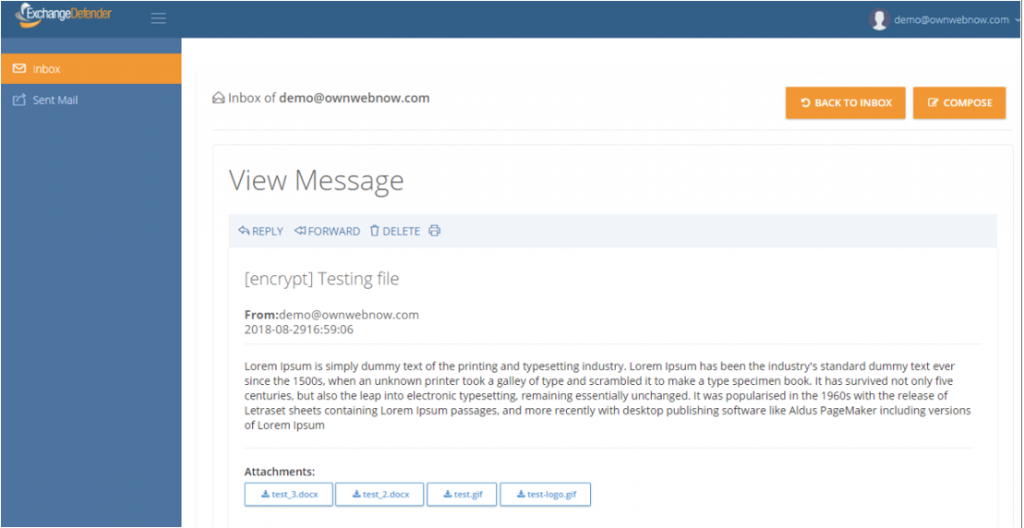
ExchangeDefender Corporate Encryption now allows you to send encrypted attachments and share files securely from any device, even many of you that aren’t on Microsoft Outlook/Exchange. It was one of the more popular parts of the webinar we held yesterday (hope you had a chance to attend it, you can watch it anytime in our secure portal at https://support.ownwebnow.com)
ExchangeDefender Corporate Encryption was designed to eliminate the pain point of traditional key-based email encryption: too much software, too much management, exchange of public keys, software deployment, and more. It also eliminates the complaints about cloud based solutions that are often clunky, unfriendly, not to mention expensive. ExchangeDefender Corporate Encryption is none of those: it is friendly, affordable, requires no additional software or hardware.
And as of this week, it allows the sender and the recipient to exchange attachments so that the content is encrypted in both directions. Furthermore, because it is cloud based, you can resume work when you get back to your desk. The upgrades to the UI allow you to quickly see new messages, respond to them, or forward them elsewhere. It is truly turning into a highly secure, policy-based, email solution for businesses that require compliance and content security.
We’ve also made the UI more friendly by putting actions on top of the page so that it resembles popular webmail products end users have gotten used to for over a decade. Attachments are a lot more prominent and go both ways: not only can you send them, but when the recipient logs into our portal to reply they can attach anything they want to in response as well – assuring that content is protected and encrypted at all times.
ExchangeDefender SMTP Headers
ExchangeDefender mail flow and email analysis troubleshooting is at times a long and difficult process that has been automated through our admin portal at https://admin.exchangedefender.com. We realize that it’s not an option for some of our end users and new MSPs so we often get tickets in our support portal asking us why a certain message got delayed, rejected, classified as SPAM or allowed to get through if it had SPAM content, etc.
In order to troubleshoot an issue with a specific message we always ask for SMTP headers. The following blog post will help you find them in Outlook Web App, Outlook 2013 and Outlook 2016.
Outlook Web App
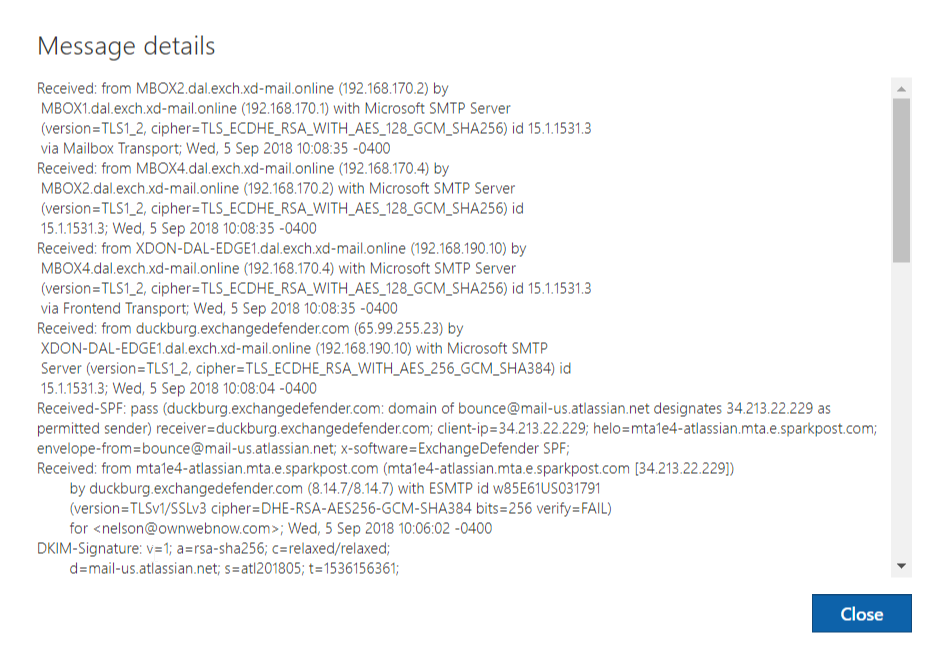
From the message listing, right click on the message and select “View Message Details”:
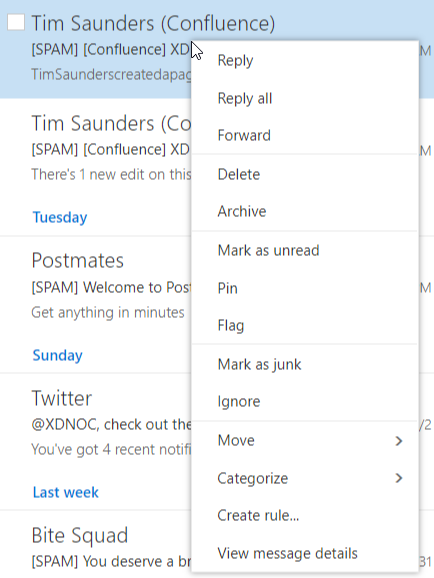
You will see Message details screen. Copy and paste it in the ticket and we can help you with the rest.
Outlook 2013 / Outlook 2016
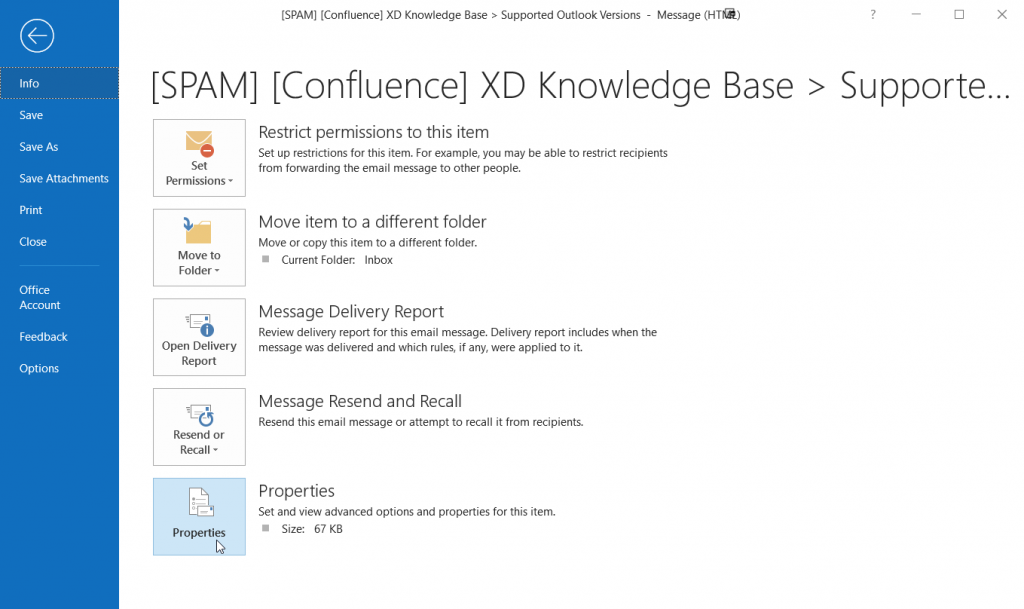
From the message listing double click on the message so it pops up in it’s own Outlook window.
Then click on File and you will be shown the message file options:
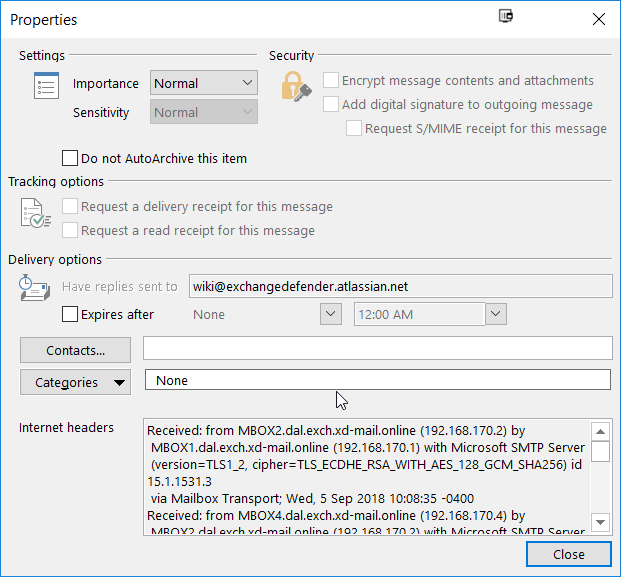
Click on Properties and you will see the SMTP headers. Copy and paste it in the ticket and we can help you with the rest.
Important: Please copy and paste the contents of the screen into our support ticket instead of taking a screenshot. Sometimes the SMTP headers contain characters that are very similar (qf9mfIlI1IlI) and it can take a lot longer to locate the message rather than having a specific text search.
What happens next is that our team is able to locate the specific message in our database and then with that data do further analysis using the node that processed the message and look at all the logs generated by hundreds of different services that are analyzing every message for dangerous content.
How to Market Email Security Solutions

We’ve had the opportunity to spend quite a bit of time with our top small business partners over the summer as they hold meet & greets / lunch & learns while kids are out of school and staff takes vacations. We got to see firsthand how the features and the problems are both the same as they have always been (budget, buy-in) and completely different in a way that technology solves business problems – cloud compliance, vendor/mobility management. One of the businesses that moved to ExchangeDefender was able to get rid of 7 (seven!!) different vendors involved in email & mobility solutions alone.
It’s all about the Story.
ExchangeDefender is increasingly becoming the modular security solution that can help service your mobile & security needs end to end. From email hosting to support for everything that entails, from managing mobile devices to assuring their compliance, archiving, business continuity and data management – ExchangeDefender does it all from a single pane of glass. All you have to do is change the way you tell the story.
Product vs. Service
Typically, small business partners follow the same “vendor” approach to positioning ExchangeDefender “we kill SPAM for a living” and then mention the other nice “bonus” features we offer. While that may work on larger companies with CIOs where a point solution is necessary (or required for redundancy), in small business you need more finesse as you introduce our solution as the Swiss knife for typical SMB problems. Small business decision makers typically aren’t that interested in technology specs, even if they are familiar with the problems, they are looking at the price and at the time this the solution is going to take away.
So here is what works for us:
We position ExchangeDefender as a service (not even mentioning the cloud) that takes care of keeping junk out of the mailbox, keeping people productive and safe, making sure any outages have a workaround and as needed we also do encryption to protect data automatically and compliance archiving to help meet regulatory requirements and keep fines away – and we build, manage and support 100% of it end to end. In a way, we’re the last security product you need to look at and the only one you need to contact when there is a problem.
Give it a shot – this is fully compliant with the Elevator Pitch™ guerrilla marketing and truly disarms the most common objection in SMB which is “we already have something” – everyone has something, they just don’t know where it is, who does it, how it’s used and what it does – and that’s the biggest selling point of ExchangeDefender. You don’t have a dozen vendors for email, mobile, security, archiving, compliance, encryption, DDoS protection, business continuity, mobile device wipes, etc, etc you get the picture. Instead of going in and trying to sell yourself, you’re going in and looking at ways to save them money “Well, you won’t need to renew this product, or this service, your old firewall won’t have to be upgraded, you now get all the additional features, etc”
In a way, our go to market has been the same as it’s always been – but with the cloud you’re dealing with small businesses with data all over the place and providing security to a mobile organization with decentralized storage is no longer a “security” pitch, it’s a management pitch that gives them back their time.
ExchangeDefender 9 – September Update
ExchangeDefender 9 is off to a fantastic start, as mentioned in the previous post we’ll keep you up to date with any new bugs and fixes as we find and fix them here (http://www.exchangedefender.com/blog/2018/08/exchangedefender-9-launch-bugfix/). Great news on that front is that the entire codebase is new and thanks to new development methodology fixes for minor issues won’t take long. Neither will the addition of the new features: which is what we’d like to discuss today.
The following big features are coming in September and we’ll cover them in detail leading up to the release: ExchangeDefender encryption is getting a major upgrade in threaded conversations and ability to include attachments both ways, our support portal will begin mixing in live chat and status updates so you know immediately where your ticket is in our system and who is working on it, and we’re taking a major step forward to help you manage your security credentials.
ExchangeDefender Encryption Upgrade
ExchangeDefender Encryption is getting a major expansion of features when it comes to handling files and conversations. Specifically, we never want you to have to leave the ExchangeDefender web site in order to communicate effectively and securely. Starting in September, we’re adding two major features to enhance our clients ability to exchange secure content with remote recipients: threaded views and attachment uploads.
Presently, only our clients (protected by ExchangeDefender) can send encrypted attachments. Soon, senders and recipients will be able to work through our portal to send encrypted contents back and forth. The way we’ll present the entire conversation will really take our clients productivity to the next level.
Support / Ticket Live Chat
We’ve been testing a live chat/alert/popup functionality in our support portal where we can huddle up and work on the ticket in realtime with the entire team. This is a far cry from the traditional model where a ticket is accepted, assigned, worked on and completed by a single tech within a SLA mandated period of time.
In the new model, we all have the ability to work on every issue at once and quickly add relevant resources to the conversation: which is effectively what the new support is going to look like. So instead of a ticket being a single monolith of a problem that is handed from one person to the next in it’s entirety, we can now break it down into manageable pieces and a senior engineer can quickly pinpoint, triage and offer guidance that would let other technicians that are available assist the client far faster.
You will also be able to see who is viewing and working on your ticket and where/when the next update will come – this will eliminate the need for phone calls, escalation/status update requests and so on because the system is 100% reactive to what is going on – if the engineer is looking at the ticket they have a counter and they are printed on the ticket. We look forward to extending this functionality to our clients in September, we’ve been using it internally to raving reviews by our staff.
Password Policy Enforcement
ExchangeDefender is a security product – one whose origins and some features trace back to the 90s. In the past 15 months the product has been rewritten entirely, giving us far more flexibility to help you manage your users and their passwords. In September we will start storing passwords with irreversible encryption and complying with many new technologies such as Magic Link that will make password tracking a thing of the past. Additionally we’re rolling out 2FA/OTP across ExchangeDefender with our own API to extend to other applications in the ExchangeDefender universe.
There will be many more features coming along as all our departments have stepped their game up – but these major ones will definitely change the way you work with ExchangeDefender and how much we’re able to do for you and your clients. Privacy, security and management are in the news every single night and we hope to give our clients and partners a level of control over their data that will make it easier for them to sleep at night.
ExchangeDefender and Mobile Device Security
Mobile Device Security
ExchangeDefender protects pretty much any device that has access to email – and a category most prone to email-borne security exploits are mobile devices. ExchangeDefender Pro and our Exchange hosting services can nearly eliminate an attack vector through malware detection, phishing attempt alerts and can help you wipe a device remotely without having physical access to it.
The number one way to get malicious content to a mobile device is still via email – it’s so easy to trick a user to click on a malicious link and on a mobile device it is far harder to tell if the sender is legitimate or spoofed. Hackers format messages in such a way that it’s easy to see legitimate links and accidentally click on malicious ones so ExchangeDefender is extremely useful in making sure any such dangerous content is stripped off in the cloud. Anyone can email any content they wish to your mobile device and with ExchangeDefender you are assured that even the most aggressive of 0 day exploits do not arrive in your users mailbox.
Phishing, or forging/deceiving an identity of a third party, is a popular way for hackers to get users to click on links that appear to be legitimate. It’s very easy to copy a look of an Amazon or bank email notification and get the user to click on the link that takes them to a forged web site to download malicious content. Unlike Malware protection, which removes dangerous content from the email, phishing protection deactivates links in email messages and highlights phishing attempts when links to third party sites do not match the domain name of the sender. If you were getting an email from jeff@amazon.com would he be including a link to http://1001smallbizscamsandfrauds-519.org? Our system will deactivate that link and keep your user safe from whatever is on the malicious site.
Remote Wipe & Device loss management
In the event that your users device is lost, users employment is terminated, you don’t have physical access to the device but need to wipe it for security reasons – you can start a remote device wipe through your Outlook Web App under Settings > Mail > Options > Mobile devices and selecting Wipe Device. Within moments the device will be wiped clean of any data, content and settings and this works for both iPhone and Android devices (tables and phones).
ExchangeDefender Pro offers users a VPN server to connect to in a secure manner no matter where they go. Public Wifi hotspots tend to have questionable security at best and can be used to compromise a device that is connecting blindly across the Internet. Connecting your phone automatically to a VPN can assure that email access (and all the confidential data in the email) can never be snooped on.
We are currently in beta with our mobile OTP/2FA applications which will further turn the mobile device into a part of your authentication so you don’t have to remember complex passwords at all. In the meantime, it’s important to let the users know what ExchangeDefender is currently capable of doing for them and to enable/configure those features so they are actively protecting every email user in your organization.
ExchangeDefender Support: Enhanced Security and Password Management

Password Policies
You’ve seen us blog endlessly about improved security that is being rolled out with all the brand new features across our entire product and service portfolio. Trust us, this is not a simple process of just changing the password complexity requirements, people hate password changes and for the most part have become predictable in what their current and next password will be. Add to it the fact that almost everyone uses the exact same password all over the web and not a single day passes by without at least one major provider having a data breach. Sometimes it becomes comical – even LifeLock had a security issue today where they exposed a bunch of data and had to take their site offline!
So passwords suck and short of using our One Time Password / Two Factor Authentication service, it’s going to remain that way. The cool thing about ExchangeDefender, and all of our service, is that we’re going to help you better manage security and password expiration so that your users and services can remain protected and still user friendly.
New password policy at ExchangeDefender, for all of our services going forward, will be a required mixture of upper case, lower case, numbers and special characters with minimum length of 9 characters.
That is just the beginning. Some services will require a transparent OTP/2FA using your email address or cell phone as an additional real-time identity verification process. If you are about to make a large-scale change, we want to make sure it’s you and not just someone that got your password. Calling in will now require PIN or txt verification as will any service request changes – the cool thing is, if you can provide us with that information we can do just about everything you want or need through phone and chat.
The reality of security on the web is that it’s as weak as the laziest user – and it only takes one careless one to mess up the entire organization. We are on your side, we are on your team – that’s why you hire ExchangeDefender – so we’re stepping things up in terms of support and management functionality to help identify, train, and assist users when they run into an issue. Passwords and password changes may continue to suck until the end of time – but we are currently making huge changes in the way we handle support in order to help our partners and CIO’s become more productive by letting us both better secure and support users.
So You Think GDPR Doesn’t Apply to You?
That Four Letter Monster: GDPR
We know – you’re tired about hearing about GDPR – and you’ve probably received a billion emails about it from marketers all over the world urging you to “confirm” your subscription. As our CEO recently posted on Facebook:
“There were two kinds of IT people this week on Facebook – those that whined about
GDPR and those that got richer as a result of it.”
You can hear more of Vlad’s unfiltered thoughts on GDPR in the Game Changer webinar held earlier this month, but needless to say the GDPR is something that is here to stay and with every public privacy breach the notion of government regulation worldwide is going to start with GDPR as the foundation.
What this means for you – regardless of whether you’re the CIO or an MSP partner – is that client data privacy, disclosure, search, and reports will start consuming more of your time.
Do you currently have a solution in place that can quickly tell you what sort of data you have on your clients? Beyond your CRM.
What about the invoices that get emailed out with account numbers and addresses?
What about any contracts or agreements that got emailed back and forth?
I think you see where we are going with this: you need to prepare your IT for eDiscovery even if you don’t have urgent, current, and pressing reason to do so. Penalties for exposing financial data are extreme and the more the world gets used to privacy disclosure and where client data may be stored the more requests and inquiries you will start seeing. Businesses (aka “people with money”) are the low hanging fruit that will be sued first.
This is by no means a new trend: We have been selling Compliance Archive and Corporate Encryption for years but GDPR has really put the demand for these products into a new gear. For our partners, this has significantly increased both sales and service requests that are a giant opportunity for many to be ahead of the curve and regulatory changes worldwide.
Get ready for it today and call us – we have the products, the service, documentation, marketing collateral and back office legal support –
all you need to do is present it to the client and can help you do the rest.
ExchangeDefender IoT Email Relay Service

The Internet of Things
ExchangeDefender IoT has concluded it’s beta period and we’re thrilled to announce that the system will go into production this week. We have blogged about this previously and the demand for this service really surprised us – so we’re rolling with the production and adding all the new features into the beta product as the applications for this service are quite extensive. To sum it up:
ExchangeDefender’s IoT Email Relay Service
ExchangeDefender IoT Email Relay Service is a custom email smarthost (outbound relay) designed specifically for Internet of Things devices and services to securely dispatch realtime email alerts. Feature-wise:
– XD IoT Relay assigns every device has it’s own account/credentials so if one device is compromised the email capabilities of others aren’t impacted.
– XD IoT Relay is secure permitting traffic only via TLS/SSL SMTP protocol to assure security credentials cannot be sniffed on the network.
– XD IoT Relay allows dynamic IP ranges, allowing for cell/4G/LTE devices and sensors with remote/unsecure network connectivity to relay alerts.
– XD IoT Relay is compatible with every device that can send out email via SMTP/SSL (should be all of them) and is backed by our support and automated throttle management (in the event of an infection)
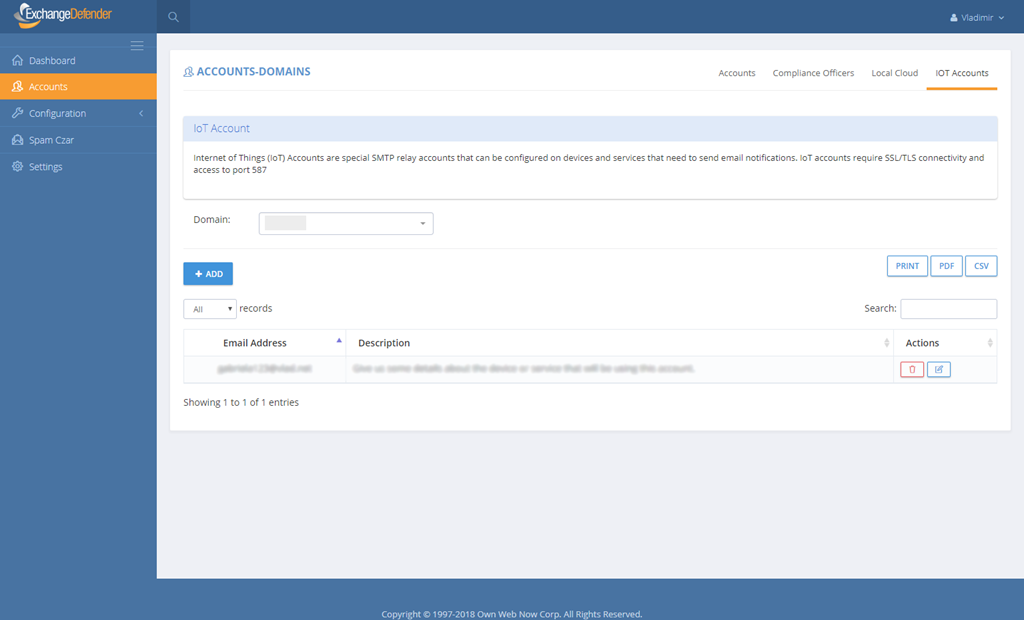
New feature is available in the ExchangeDefender admin portal under Domain Admin > Accounts > IoT Accounts.
Simply add a new account for each device you wish to have relay rights for (they are free for now) and configure your device to relay through outbound-auth.exchangedefender.com. Our service is globally redundant (no single point of failure) and is under our SPF/DMARC announced range.
We will be blogging more about this feature as we develop it and get a better handle of how it’s used but the feedback so far has been very positive and constructive. The biggest surprise (read: shock) is the level of unreliability of some of these devices/sensors and their rather infant API/app development – but they all know how to send email so many of our partners are looking to us to help fill the void between these devices/sensors going dark/offline and production email notification service. Many of our partners also looked to use this for printers, blogs, contact forms and a seemingly endless set of services that a remote ISP should be providing but they don’t – so when it comes to business and email people come to ExchangeDefender.
P.S. If you’d like to hear more about this feature and all the other new stuff we have set for ExchangeDefender in 2018, please download the webinar where we go into the details of how/why/what that might give you a broader perspective on how to position, sell, and implement these new features. Please click here to download the webinar.
General Data Protection (GDPR) and ExchangeDefender: Get your resources to demonstrate compliance
ExchangeDefender, at it’s core, is all about protecting our clients: it should come as no surprise that we are big fans of GDPR. If you haven’t been inundated by GDPR, or by a million “we’ve updated our privacy policy” emails from every web site you’ve ever signed up for, or you’ve landed here simply because the deadline is tomorrow, Friday, May 25th: rest assured we’ve got you covered.
ExchangeDefender is 100% compliant with GDPR. You are covered as are your clients on ExchangeDefender and we have presence across European Union to handle any issues or complaints that come up as a result of GDPR implementation.
What you need to know
GDPR, essentially (and no, this is not legal advice), is a European Union data privacy regulation that turns the tables on marketers and gives residents of EU very specific rights and control over their personal data. The regulation is very broad in terms of scrutinizing everyone that may be holding (controller) or managing/processing (processor) personal data and ExchangeDefender fits both of those roles at times depending on the product or service we’re talking about.
If you’d rather do without me talking at you for 6 minutes, we have a ton of other resources that you can share with your clients. I would start with this document available for download here:
What you need to do now
1. Start by reviewing our new Privacy Policy. I know, I know, you’re done with
2. Contact us if you’re seriously building out a business around GDPR and get our marketing folks to hook you up with branded collateral (minimum client count
3. Review our GDPR collateral, particularly the webinar with the deep dive of the ExchangeDefender implementation. This is the most important thing you could do but it’s 27 minutes long and I know everyone doesn’t have that kind of time or attention span – I get it – but if you’re seriously working with us and need GDPR assistance, you will have to go through the training eventually.
Where to go next
We are very excited about GDPR and have put significant resources to design our products and services around the regulation because we believe it will have a broad impact well beyond Europe. Privacy, data integrity, right to be forgotten, right to withdraw consent, right to find out what sort of information companies have about you – those are fundamental rights in our opinion.
And if you ignore them the penalties are going to be extensive.
What we’re choosing to do at ExchangeDefender is to create a service around protecting people on the Internet – not just from SPAM but really safeguarding all communication you do as a business. Take a look at our GDPR resources and see how we can get you started on the same path – at the very least you can use our reach and resources to comply with GDPR.
Top 5 Mistakes Companies Make With Compliance
ExchangeDefender Compliance Archive was designed as a blend of services and products to help organizations achieve regulatory compliance. This complex process is always evolving with new regulatory requirements, changes in organization structure, and unique reporting requirements.
At ExchangeDefender we specialize in helping organizations with their eDiscovery needs. Here are the biggest fallacies we hear all the time:
“We have a backup”
Email backups are not sufficient for nearly any modern regulatory compliance requirements for email retention. Not only can the messages be deleted before backups run, but running reports across the entire organization is next to impossible, not to mention excessively expensive. We recently assisted a partner managing a small 15 employee office in their backup and restore process to locate a message from 5 years ago, costing the organization over $18,000 in IT labor alone.
“We have a product/compliance service”
Having a product or a service subscription is different from being in compliance with regulatory requirements. The difference between having a product and being in compliance is similar to “We have a CPA” and “We have filed our tax returns on time” – mistaking the two can be costly and dangerous.
“We are never going to need that”
Most organizations downplay the importance of long term email archiving and eDiscovery. An overwhelming majority of subscribers to our eDiscovery service don’t have a specific regulatory requirement at all, they do it to effectively defend themselves from legal threats that are all too common these days. With email being the gateway for all corporate communication, it is the first place record retentions, legal holds, and subpoenas are issued for electronic records and there needs to be a system in place to effectively deliver that information.
“What we have is enough”
Regulatory compliance goes far beyond poorly interpreted recommendations and laws. It is a process of producing reports, identifying problems, and assuring that corporate communications policies are being followed, or at least addressed, in case there is an issue. If the organization does not have people in charge of managing the compliance on a monthly basis or there are no current reports searching for dangerous or sensitive content or there is no ongoing maintenance or an established incident record – the organization is likely out of compliance even if they purchased the right software or signed up for the right service at one point.
“We have a someone managing that”
Someone is not a good person to rely on when you get a subpoena and they are even more difficult to get into a courtroom. Plus, how much would you trust them to demonstrate expertise and defend the implementation of the compliance archiving and eDiscovery solution? Many organizations make a mistake of thinking that just signing up for a service or purchasing a product is sufficient for compliance but it’s really just a starting point. You need the personnel, product, service, and reporting to fully achieve regulatory compliance.
ExchangeDefender Compliance Archiving and eDiscovery are a part of a professional service that helps get your organization and its means of communication on path to achieving regulatory compliance. Whenever someone is fully confident that they have their compliance in order we simply ask them to “show me your last Compliance Officer Report” and almost everyone struggles to produce the report or even name the Compliance Officer, the processes being used for archiving, the type of data protection, or the way in which the entire process is tested and audited. With ExchangeDefender Compliance Archiving, you not only get a service, you get a partner that will work with you every step of the way in achieving your regulatory and organizational needs for proper record keeping.