Trusted sender keeps on ending up in SPAM

One of the most common complaints we get from our clients has to do with allow/whitelist policies and to make the long story short this happens because of the way your service provider configured ExchangeDefender. The long story, technical background, and best practices are outlined at https://www.exchangedefender.com/docs/whitelist. It usually sounds like this:
“I keep whitelisting this email address that sends me my OTP password / password reminder / login code / transaction confirmation / newsletter and they keep on ending up in SPAM!”
This happens for clients that configure ExchangeDefender to block email forgeries and spoofing.
You see, the email address that is showing up in ExchangeDefender and your Outlook/Gmail is not the actual email address that the message was sent from. Large volume emails (OTP, password reminders, notifications) are not sent by humans, they are computer generated and there is a random email address for every notification they sent out (so when/if it bounces they can track it).
These automated email addresses tend to have a long randomly generated identifier in them and generally look like this:
010001890676a389-ee862f60-d7ea-4ba1-a113-f16935e2afeb-000000@amazonses.com
But in your Outlook/Gmail the spoofed/faked email appears to have come from DoNotReply@someotpsite.cz which has the domain you trust and attempt to allow/whitelist. If you pull up the SMTP headers from the quarantined email you can see this email address in the envelope-from field:
Received: from inbound10.exchangedefender.com (65.99.255.114) by
owa.exchangedefenderdemo.com (10.10.10.5) with Microsoft SMTP Server (TLS) id 14.3.498.0;
Thu, 29 Jun 2023 05:23:03 -0400
Received-SPF: pass (inbound10.exchangedefender.com: domain of 010001890675c389-ee862f60-d7ea-4ba1-a113-f16935e2afeb-000000@amazonses.com designates 54.240.77.69 as permitted sender) receiver=inbound10.exchangedefender.com; client-ip=54.240.77.69; helo=a77-69.smtp-out.amazonses.com; envelope-from=010001890676a389-ee862f60-d7ea-4ba1-a113-f16935e2afeb-000000@amazonses.com; x-software=ExchangeDefender SPF;
Authentication-Results: inbound10.exchangedefender.com; dmarc=pass (p=quarantine dis=none) header.from=someotpsite.cz
Authentication-Results: inbound10.exchangedefender.com;
dkim=pass (1024-bit key) header.d=someotpsite.cz header.i=@someotpsite.cz header.b=”QPv3HP79″;
dkim=pass (1024-bit key) header.d=amazonses.com header.i=@amazonses.com header.b=”MsX8RGl7″
Received: from a77-69.smtp-out.amazonses.com (a77-69.smtp-out.amazonses.com
[54.240.77.69]) by inbound10.exchangedefender.com (8.14.7/8.14.7) with ESMTP
id 35T9M86a030204
<demo@exchangedefenderdemo.com>; Thu, 29 Jun 2023 05:22:09 -0400
From: <DoNotReply@someotpsite.cz>
To: <demo@exchangedefenderdemo.com>
Subject: ConnectWise Manage Security Code
…
Solving this issue requires your ExchangeDefender admin to decide how permissive they want to be of email forgeries and fakes. ExchangeDefender provides two ways to manage this in the ExchangeDefender Domain Admin app at https://admin.exchangedefender.com (see documentation)
Option 1: Allow email from the bulk email network
ExchangeDefender enables you to automatically pass through messages coming from specific bulk/spam mail providers. It’s located at https://admin.exchangedefender.com under Advanced Features > Bulk Mailer Policy:
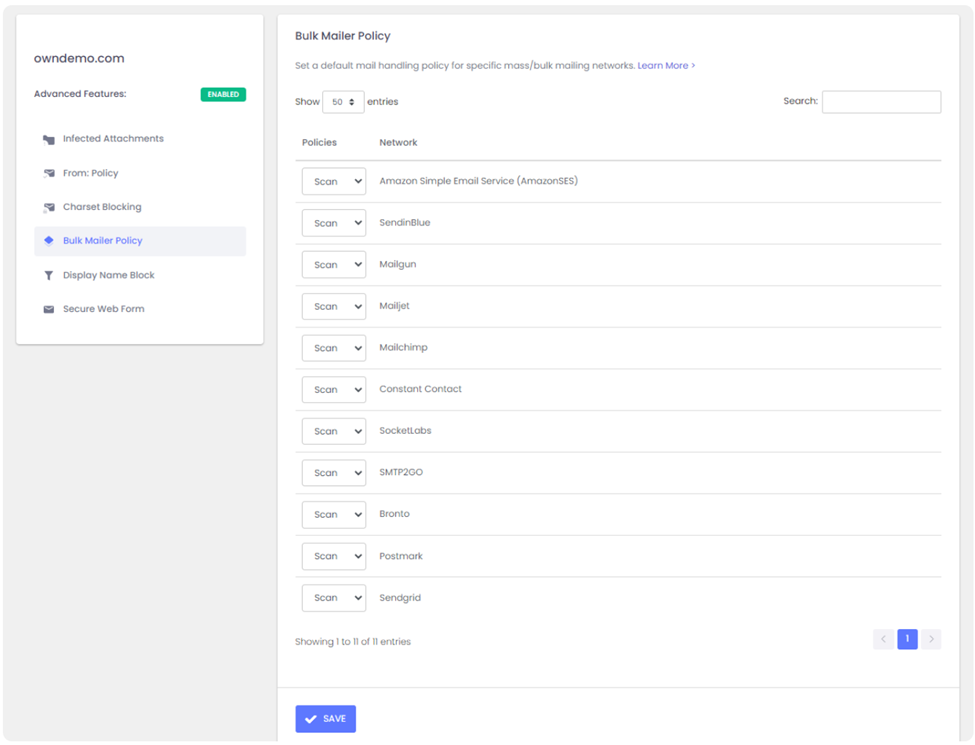
In our example SMTP header the message came from AmazonSES so if you change the policy from Scan to Allow, ExchangeDefender will simply deliver these messages to your mailbox without quarantining it as a forgery/spoof (which it is).
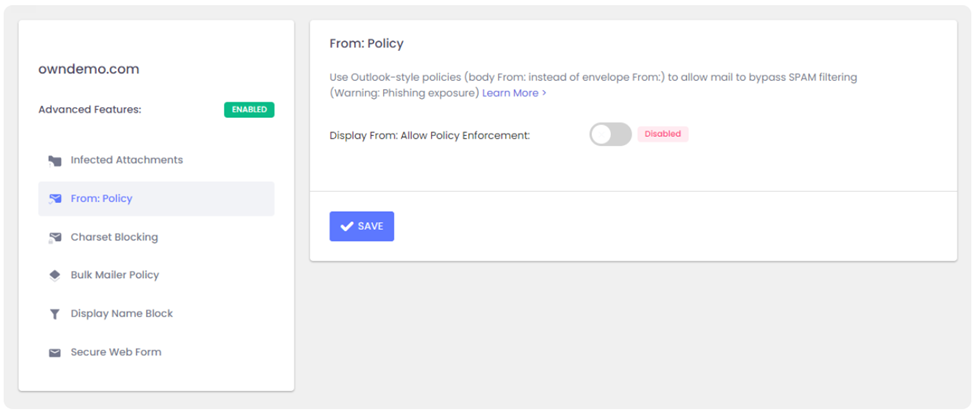
Option 2: Choose a relaxed From: policy
This is a less secure option that will allow forgeries and effectively lowers your security level to that of M365/Office365 – and we strongly discourage you from doing that. However, if the client requires it you can get it done under Advanced Features > From: Policy:
Summary
If you’re seeing notification emails in your SPAM quarantine even though you’ve trusted the sender repeatedly, it’s doing so because the message is being spoofed and your admin has configured ExchangeDefender to block that activity. You can relax the security restrictions by choosing to either allow the bulk mail network or you can build your trust rules on the less-secure From: address.
Our team is always here to help but they aren’t allowed to guess without seeing the SMTP headers first – so if you ever run into an issue that you’d like us to take a look at grab the headers and provide them at https://support.exchangedefender.com and we’ll advise from there.
Service Provider Dude, where is my SPAM?

ExchangeDefender is the ultimate cybersecurity wrapper for an organization and we already discussed how Users and Domain Admins can locate messages ExchangeDefender was configured to keep out of the mailbox.
ExchangeDefender users have a beautiful and powerful way to access their quarantined mail and work around email problems, domain admins have flexible settings, policies and access to the logs to keep the organization protected. So what do ExchangeDefender Service Providers have that others don’t?
ExchangeDefender Service Provider access enables you to do deep troubleshooting and emergency “incident response” activities. Service Provider login is the highest level of control in ExchangeDefender so you have access to all the data that ExchangeDefender has.
Accessing Logs
ExchangeDefender Service Provider access gives you access to the centralized log facility where you can locate any message ExchangeDefender has processed from a central pane of glass.
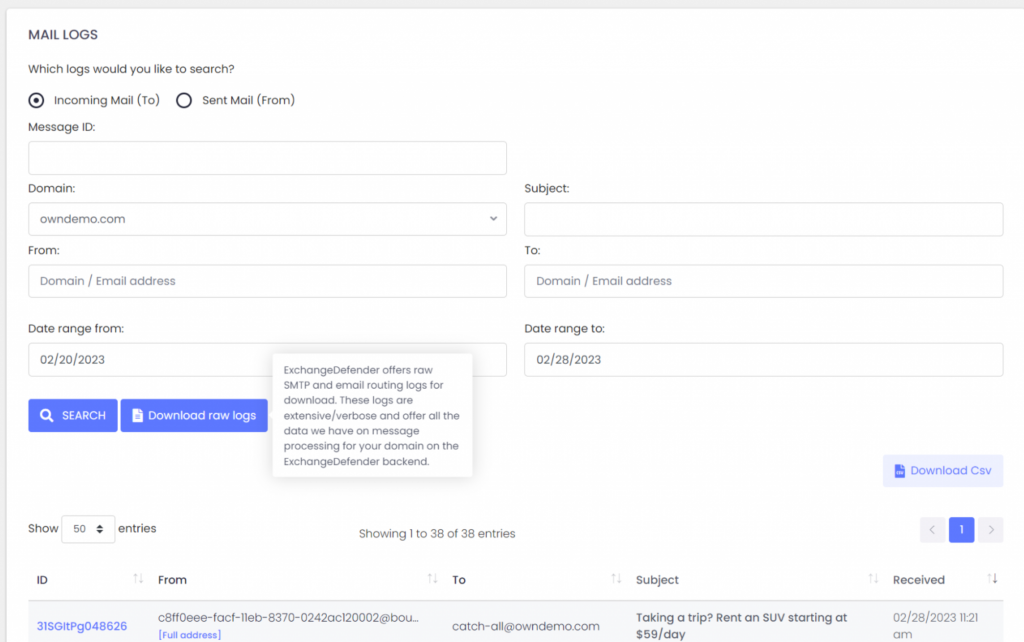
You can download any search results as a CSV file that can be better visualized and analyzed in a spreadsheet and reporting tool of your choice. This is particularly useful when you don’t know the sender or are searching for an automated sender with a fake tracing email address.
Our partners frequently rely on this facility to troubleshoot for missing messages.
Downloading Raw Logs
ExchangeDefender Service Providers also have access to raw SMTP Mail Logs which give our partners direct access to low level SMTP transactions and error logs. It’s located in the same location as log search.
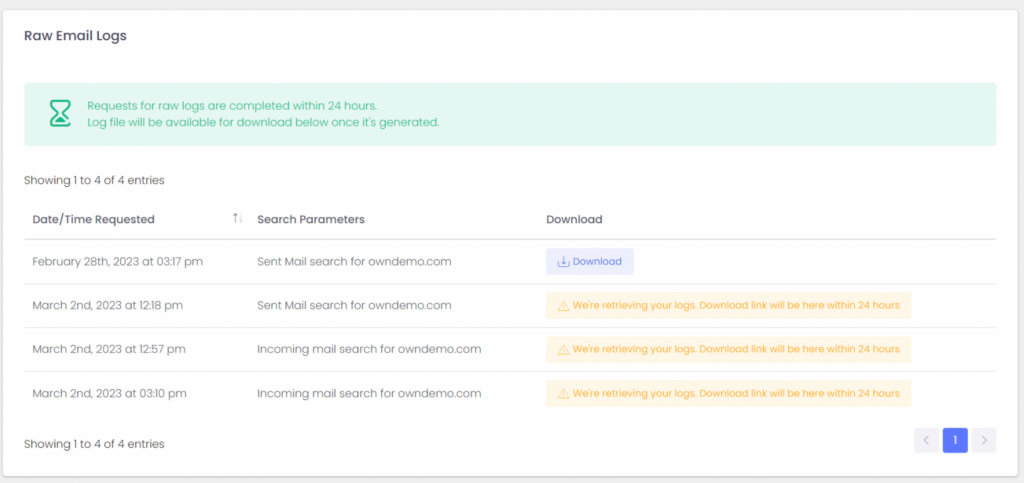
Service Providers rely on these logs as the ultimate source of truth regarding the traffic for the ExchangeDefender protected domain. This is a fantastic tool if you’re looking for intermittent delivery errors or policy violations or just have a very specific email or server you’re looking for.
Logs will get pulled from all our services and will be available for download within 24 hours. Don’t let the boilerplate distract you, almost all of our clients will get their logs within the hour. From there you can load the logs into your favorite analytics tool and dig for the errors and problems in the mail flow.
To sum it up
ExchangeDefender can help you account for every message going in and out of your organization. While users have a powerful and beautiful way to access their quarantined mail or continue where they left off during an outage or email problem, domain admins and service providers have far more access to the logs so they can troubleshoot around different settings and policies.
Domain Admin Dude, where is my SPAM?

In our previous post we discussed how users can get to their own SPAM quarantines but did you know that you as the domain administrator have access to EVERYONE’s junk mail?
ExchangeDefender Admin Portal features a SPAM Admin section where you can release ANY message caught by ExchangeDefender to ANY user in your organization.
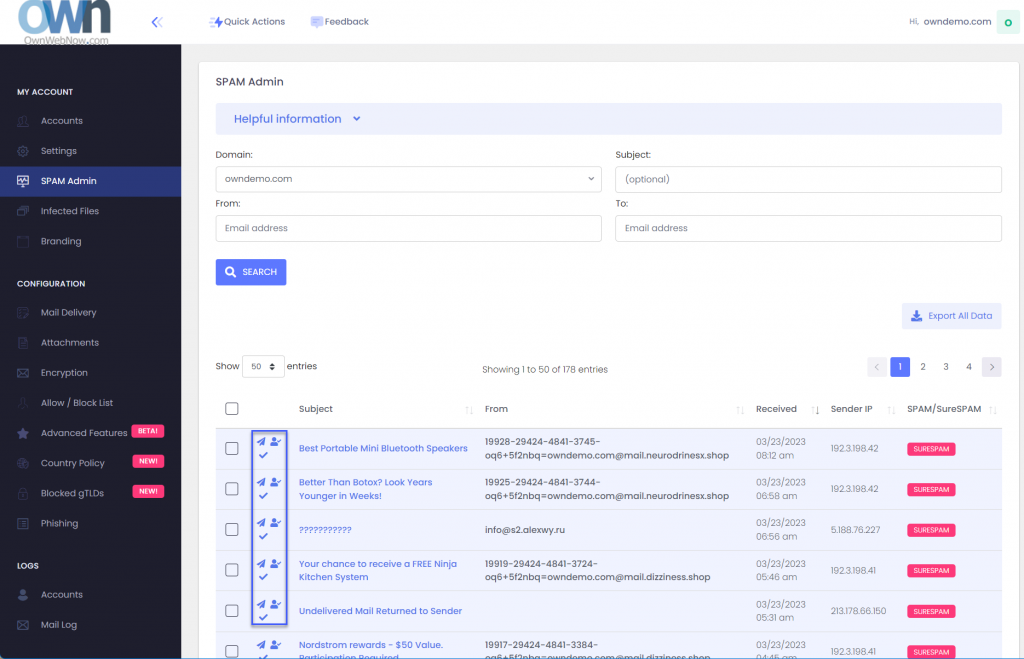
The three icons next to the message are Release Message, Allow Sender, and Mark as reviewed. Releasing a message will get it to the end users mailbox while allow sender will create an Allow policy for that email address so it skips SPAM checks in the future.
Many organizations designate a SPAM Admin that is in charge of fishing out important messages, attachments, and other content that was blocked by an IT or corporate policy. If you have a lot of users that are not tech-savvy this feature will save you a ton of time.
I already have an Allow Policy and my mail from this sender is always ending up in Junk Mail!
ExchangeDefender Advanced Features can help you here as this problem is so common we’ve built an entire feature to help solve it. The issue is, most of the messages coming are from automated systems (password reminders, newsletters, appointment confirmations, etc) that are sent by a computer instead of someone’s Outlook or phone. They all rely on mass/bulk mail systems like Amazon SES, Sendgrid, etc and those networks use a fake email address to send a message every time (so they can track bounces). You can’t create an allow policy (whitelist) for those addresses as they change every time, so take a look at the Bulk Mailer Policy section:
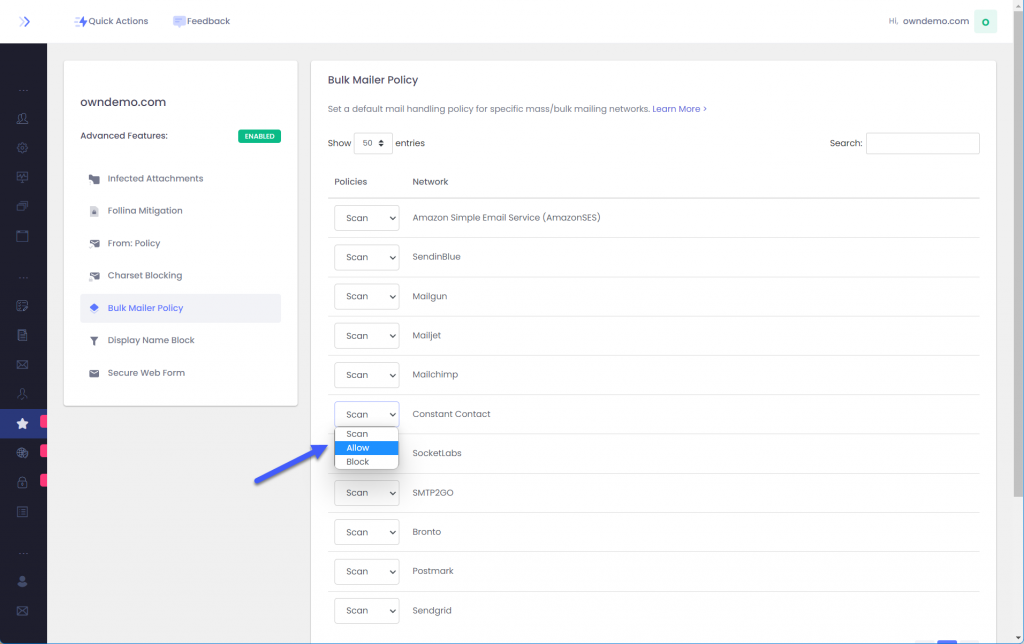
Here you can tweak the policy applied to each bulk mailer network to accommodate your users. By default we scan each message from these networks for SPAM contents but depending on the problem you are trying to solve with SPAM you can change it to Block or Allow messages from that network.
I already did all that, seriously, where is my email?
Most of policy enforcement problems stem from not knowing which message the user is looking. As mentioned earlier, automated systems forge the email address they send mail from so the address you see in Outlook is not the actual email address. It’s tough to make policies or find the message when you don’t know the senders email address: ExchangeDefender Mail Log to the rescue:
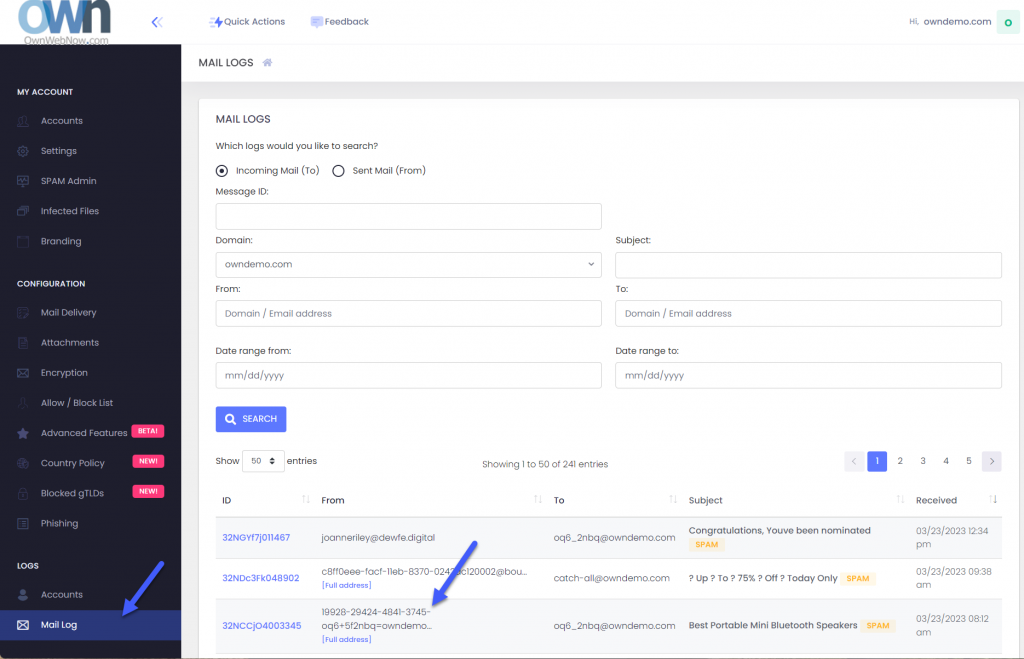
As the Domain Admin you have access to all the email logs for your domains. Click on Mail log and you’ll be able to search for the message based on time, date, subject, etc.
You can also scroll through the mail log. See the [Full address] below some senders? Those are the fake tracking email addresses we’re talking about. Generally you can create a domain-wide allow policy for the entire domain if you trust that the sender isn’t going to send malicious content (we’ll still check if any attachments are infected and apply your file/extension policy).
To sum it up
As an ExchangeDefender Domain admin you have powerful tools to locate SPAM, apply allow or block policies, and to scope them down to the bulk mailer network that is usually the #1 culprit. Go figure, nobody wants these messages and they sometimes get inadvertently reported as junk anyhow.
ExchangeDefender can save hours of going through transaction and message logs by presenting all of your messages in a user-friendly way where you can quickly release them to your user, create an allow policy so it doesn’t get intercepted again, and designate clients trusted partners/networks that should always go straight to their mailbox.
Dude, Where’s My SPAM?
ExchangeDefender protects you from dangerous email by blocking their delivery directly into your Inbox. Sometimes the way your IT admin has configured ExchangeDefender (security policies, admin policies, business restrictions) can become more aggressive and quarantine legitimate email messages. Other times the email sent by a legitimate sender is so misconfigured (broken DNS, email structure, RBLs, etc).
ExchangeDefender makes it easy to secure your Inbox and easy to get to messages that it’s been told to block.
If you’re expecting an important email and it hasn’t arrived read on for how to access it.
ExchangeDefender Quarantine
ExchangeDefender Quarantine is a web app accessible from any modern web browser, desktop and mobile. Not only will it show you everything we’ve kept from your Inbox, you’ll also be able to read/reply/forward/print the messages immediately and make sure they never end up in the SPAM.
First, open a browser and go to https://admin.exchangedefender.com
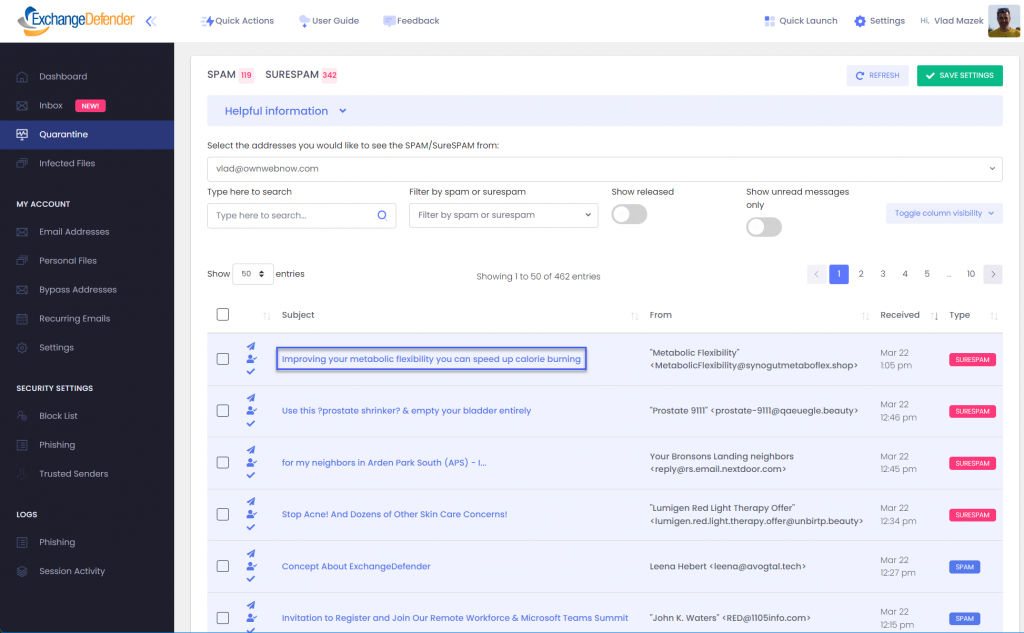
Click on Quarantine and we’ll show you all the messages that are currently waiting. Note that the from address is the real/machine email address, not a fake/forged one you see in Outlook. This will make it easy to tell who is just spoofing and who is legitimate.
If you click on the subject, your message will open and you will able to act on it just like you do from any other email client right there in the same browser window.
If you click on the icon to the right of that (user with a checkmark) the system will create an Allow policy to let messages from this sender skip SPAM checks next time and arrive directly in your Inbox.
Option 2: ExchangeDefender Inbox
Sometimes the message isn’t in the Quarantine and it isn’t in your inbox. So where did it go?
99.9% of the time, the message has been miscategorized by your email infrastructure. This happens often when [relay permissions aren’t configured correctly] or the email itself triggers some other internal security process (desktop AV, firewall, etc) that blocks you from accessing it.
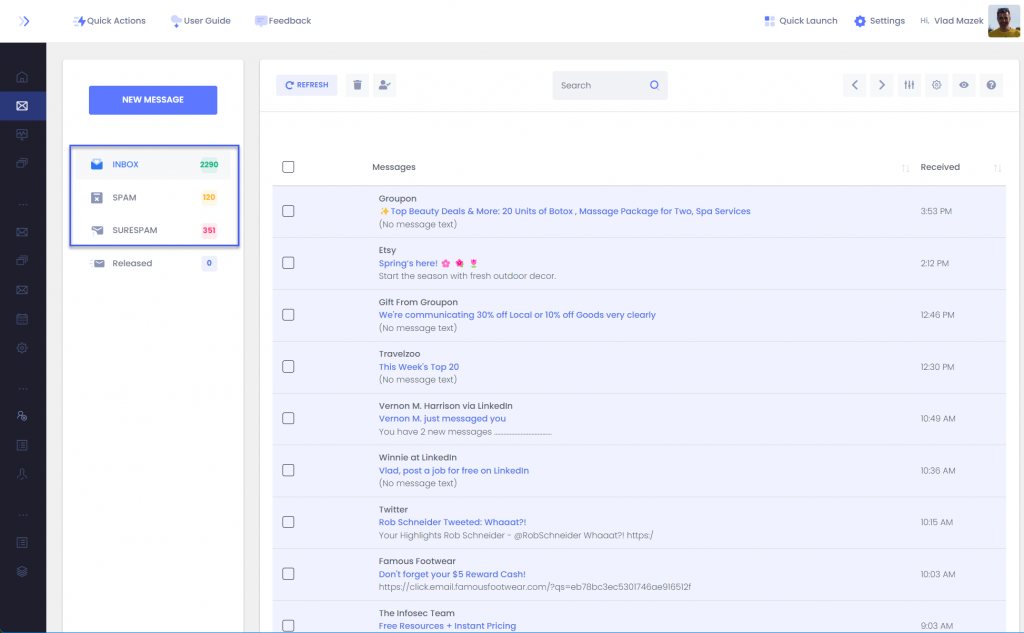
Solution: The best hack to employ here is to rely on the ExchangeDefender Inbox. We cache all the messages going to your server and if you click on Inbox you’ll be able to see messages we sent to your mailbox.
To sum it up
The easiest way to access all the messages ExchangeDefender is keeping from your mailbox is to go to https://admin.exchangedefender.com and click on Quarantine. For messages that don’t get delivered after they’ve been processed by ExchangeDefender stay on https://admin.exchangedefender.com and click on Inbox.
For more information about ExchangeDefender web app
Still can’t find the message? Tune in next week to see how your [domain admin] or [service provider] can help.
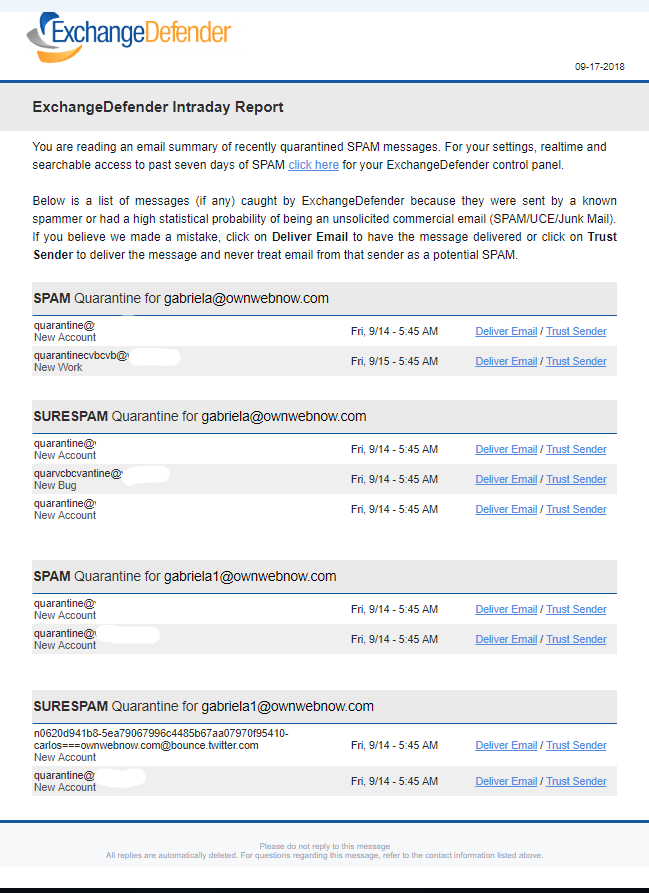
ExchangeDefender Introduces New SPAM Reports
SPAM Email Reports
ExchangeDefender SPAM Email Reports remain one of our most popular features and after nearly 6 years since the last major revision we’re looking to improve both the value and the functionality. For many of our end users, ExchangeDefender is the sole provider of cyber security training and information – so the responsibility of better educating our clients on the threats they are likely to face via email and web is crucial.
Then there is the look and feel of it. White collar workforce has largely gone away from dual monitor configurations to smaller portable devices on which users don’t spend the whole day in Outlook – so our email reports that were designed for the Microsoft desktop era needed a little face lift.
New ExchangeDefender SPAM Email Reports are launching on October 1st 2018 and we’ve made several significant changes to the look and feel based on user feedback.
– New reports feature “friendly” From addresses, instead of the actual From: line we’ve always used.
– Contrast has been improved as well as spacing, so finding information in the email is much simpler.
– Font size, padding, colors, etc has been modernized as well, allowing the report to look amazing on both small phone screens and large wide-screen computer displays.
On the backend, our reports and email release requests are starting to embed our support at the point of release, making sure our end users get exactly what they are expecting right away. If the message isn’t displaying correctly, or if it cannot be located, or if the message is continuously ending up in the SPAM quarantine even though the user believes they whitelisted it (99.999999999% they whitelist the disposable from tracking email which changes every time a message is sent, instead of whitelisting the domain) – our support will be there to assist them immediately without picking up a phone, without opening up a support ticket, without escalating it to the office manager or creating additional work. On demand service #ftw.
Our mission to help protect our clients from dangerous and malicious content also has to account for threats before they become problems – which is why we’re investing in training and info collateral aimed at the users so they are aware of new ways hackers are trying to exploit them. This info will be featured prominently in the service and we will cover it in detail as we ramp up production but for the time being we understand our end users have limited time and limited interest in what is going on in the world of cyber crime – so we will limit our content to 140 characters and feature relevant stuff only, nothing commercial.
If you have any suggestions or ideas for our Email SPAM Reports, please do not hesitate to let us know.