LiveArchive To Be Discontinued and Replaced Dec 2023
ExchangeDefender will be discontinuing the current LiveArchive service on December 31, 2023. LiveArchive is being replaced by a new service in Q4 2023 (Oct-Dec 2023).
ExchangeDefender Inbox will be providing the business continuity aspect of LiveArchive. Inbox will give our clients the ability to send and receive emails in real time from the web interface during any outage or service issue.

ExchangeDefender Inbox has been in production for over a year with great customer feedback and partner sales success – clients love it because it’s fast, efficient, and simple to use (conveniently available at admin alongside their SPAM quarantine, bypass, virtual email addresses, and recurring email)
LiveArchive product had a great run for over a decade and numerous releases but it suffered in the SMB/MSP space because users only became aware of it when things blew up. Some faced issues with credentials, access, different UI were only compounded by the technical challenges. Furthermore, most of our partners relied on the product as the backup service and we’ve executed many projects helping our partners export their client’s email as a means of Exchange recovery.
LiveArchive has been used more as a live backup and data recovery service than a business continuity solution (note: NOT the case with Inbox, convenient access and ease of use has many users relying on it as their primary email)
Over the years the business recovery and email archiving projects we’ve helped our partners perform have inspired us to give LiveArchive new life as a reimagined email failover solution that addresses the technical and cybersecurity issues of the current decade!
I’d like to wrap this up with some good news – Yes, you will still have access to over a year of inbound/outbound email. Yes, it will still be FREE and included in the upcoming release which will be announced on September 1st, and remain included in ExchangeDefender free of charge (hint: start learning about Amazon S3 or Minio S3) Another bit of good news is that we’re not about to raise prices either, this new feature set is free to our partners who want to implement their own archiving or backup process.
Something old, new, borrowed, and blue!
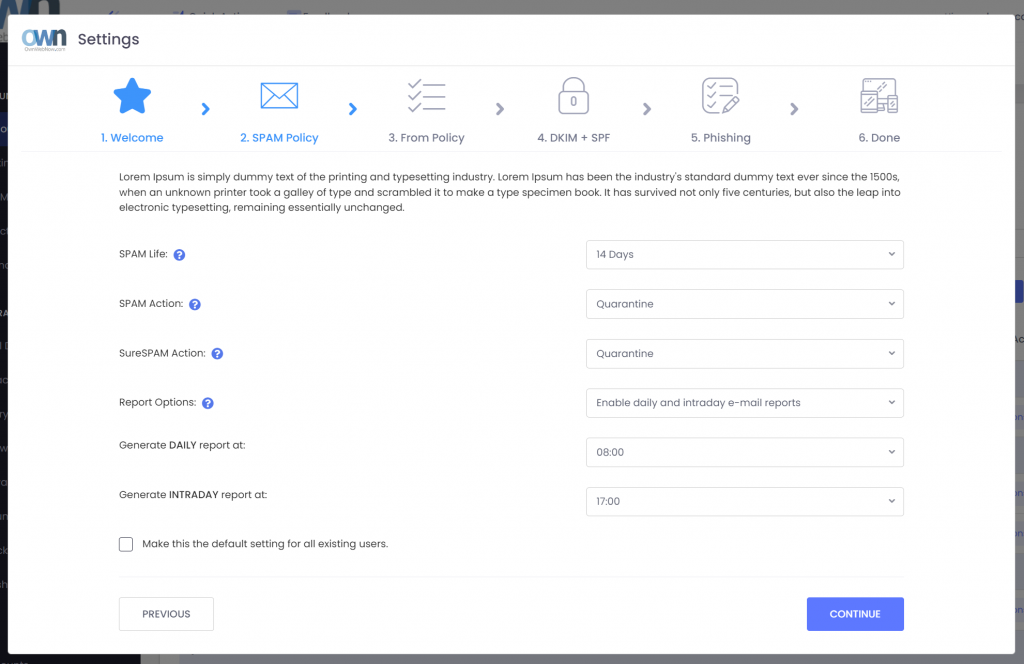
As the throwback to the Victorian era implies, ExchangeDefender looks forward to providing your protection and prosperity. From September to November of 2023 we will be launching a ton of new features and we want to invite you to a webinar that will explain all the details you need to know:

The pricing will not change but you’ll get many new features and security settings.
We are responding to the demands and problems our clients face every day exchanging information across the Internet securely.
What worked a decade or two ago, heck even a week or two ago in some cases, is no longer adequate. That’s what you pay us for and the primary value we provide – keeping new exploits and attacks on your technology away from your server/cloud/tenant.
To get the same level of protection and monitoring you’d need a dedicated cybersecurity team for even the smallest of organizations – and we’re taking big steps to simplify that process and give you the ability to control your security without having to deal with every little detail.
We’re excited and hope you get a chance to join us for this webinar – we promise it will save you a ton of time and get you ahead of what will be a very busy quarter.
Trusted sender keeps on ending up in SPAM

One of the most common complaints we get from our clients has to do with allow/whitelist policies and to make the long story short this happens because of the way your service provider configured ExchangeDefender. The long story, technical background, and best practices are outlined at https://www.exchangedefender.com/docs/whitelist. It usually sounds like this:
“I keep whitelisting this email address that sends me my OTP password / password reminder / login code / transaction confirmation / newsletter and they keep on ending up in SPAM!”
This happens for clients that configure ExchangeDefender to block email forgeries and spoofing.
You see, the email address that is showing up in ExchangeDefender and your Outlook/Gmail is not the actual email address that the message was sent from. Large volume emails (OTP, password reminders, notifications) are not sent by humans, they are computer generated and there is a random email address for every notification they sent out (so when/if it bounces they can track it).
These automated email addresses tend to have a long randomly generated identifier in them and generally look like this:
010001890676a389-ee862f60-d7ea-4ba1-a113-f16935e2afeb-000000@amazonses.com
But in your Outlook/Gmail the spoofed/faked email appears to have come from DoNotReply@someotpsite.cz which has the domain you trust and attempt to allow/whitelist. If you pull up the SMTP headers from the quarantined email you can see this email address in the envelope-from field:
Received: from inbound10.exchangedefender.com (65.99.255.114) by
owa.exchangedefenderdemo.com (10.10.10.5) with Microsoft SMTP Server (TLS) id 14.3.498.0;
Thu, 29 Jun 2023 05:23:03 -0400
Received-SPF: pass (inbound10.exchangedefender.com: domain of 010001890675c389-ee862f60-d7ea-4ba1-a113-f16935e2afeb-000000@amazonses.com designates 54.240.77.69 as permitted sender) receiver=inbound10.exchangedefender.com; client-ip=54.240.77.69; helo=a77-69.smtp-out.amazonses.com; envelope-from=010001890676a389-ee862f60-d7ea-4ba1-a113-f16935e2afeb-000000@amazonses.com; x-software=ExchangeDefender SPF;
Authentication-Results: inbound10.exchangedefender.com; dmarc=pass (p=quarantine dis=none) header.from=someotpsite.cz
Authentication-Results: inbound10.exchangedefender.com;
dkim=pass (1024-bit key) header.d=someotpsite.cz header.i=@someotpsite.cz header.b=”QPv3HP79″;
dkim=pass (1024-bit key) header.d=amazonses.com header.i=@amazonses.com header.b=”MsX8RGl7″
Received: from a77-69.smtp-out.amazonses.com (a77-69.smtp-out.amazonses.com
[54.240.77.69]) by inbound10.exchangedefender.com (8.14.7/8.14.7) with ESMTP
id 35T9M86a030204
<demo@exchangedefenderdemo.com>; Thu, 29 Jun 2023 05:22:09 -0400
From: <DoNotReply@someotpsite.cz>
To: <demo@exchangedefenderdemo.com>
Subject: ConnectWise Manage Security Code
…
Solving this issue requires your ExchangeDefender admin to decide how permissive they want to be of email forgeries and fakes. ExchangeDefender provides two ways to manage this in the ExchangeDefender Domain Admin app at https://admin.exchangedefender.com (see documentation)
Option 1: Allow email from the bulk email network
ExchangeDefender enables you to automatically pass through messages coming from specific bulk/spam mail providers. It’s located at https://admin.exchangedefender.com under Advanced Features > Bulk Mailer Policy:
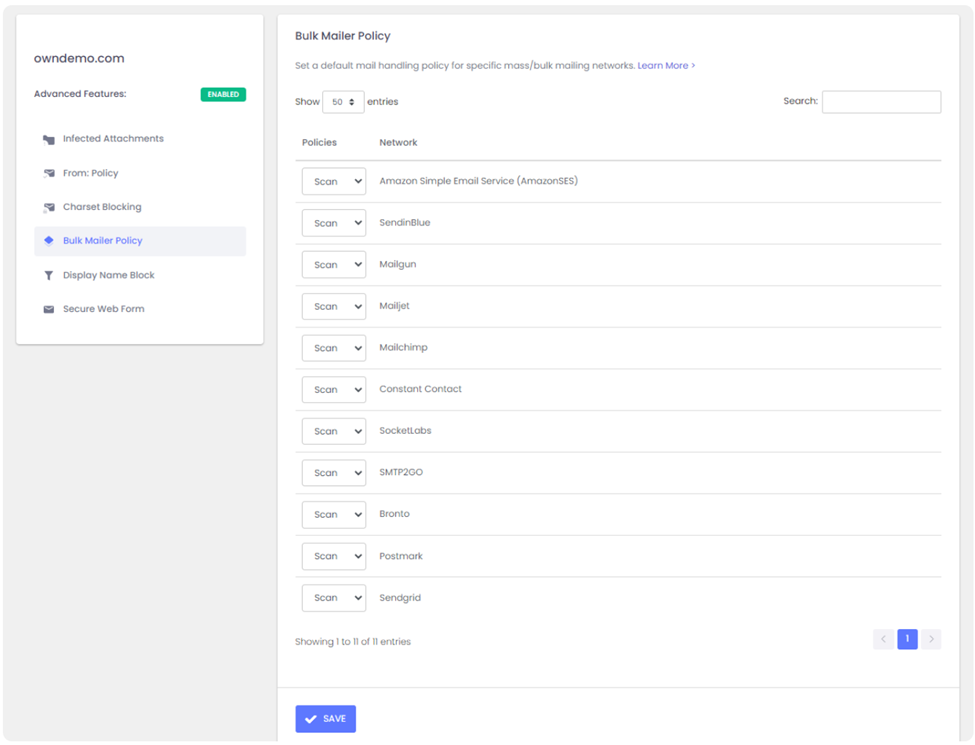
In our example SMTP header the message came from AmazonSES so if you change the policy from Scan to Allow, ExchangeDefender will simply deliver these messages to your mailbox without quarantining it as a forgery/spoof (which it is).
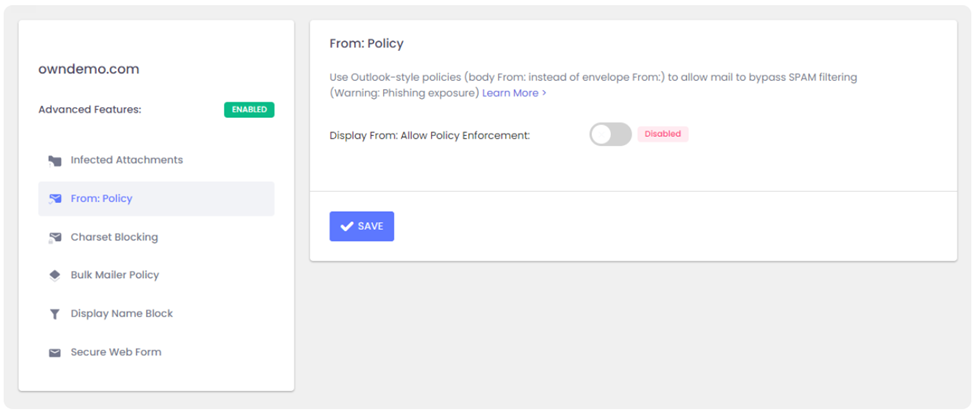
Option 2: Choose a relaxed From: policy
This is a less secure option that will allow forgeries and effectively lowers your security level to that of M365/Office365 – and we strongly discourage you from doing that. However, if the client requires it you can get it done under Advanced Features > From: Policy:
Summary
If you’re seeing notification emails in your SPAM quarantine even though you’ve trusted the sender repeatedly, it’s doing so because the message is being spoofed and your admin has configured ExchangeDefender to block that activity. You can relax the security restrictions by choosing to either allow the bulk mail network or you can build your trust rules on the less-secure From: address.
Our team is always here to help but they aren’t allowed to guess without seeing the SMTP headers first – so if you ever run into an issue that you’d like us to take a look at grab the headers and provide them at https://support.exchangedefender.com and we’ll advise from there.