ExchangeDefender: Overhaul of Phishing Protection
ExchangeDefender is thrilled to announce the new Phishing Firewall in the cloud, going into full production – Wednesday, June 12th, 2019 for all ExchangeDefender Pro and Enterprise protected clients. The old way of highlighting, underlining, inserting warnings and so on will be removed from the service at the same time because it lacks the ability to protect clients in real-time.
The ExchangeDefender Phishing Firewall (EPF) is a real-time, active pishing protection. As ExchangeDefender processes inbound mail, it will rewrite every link to proxy it through EPF when user clicks on it. If the site is safe, the user will be automatically redirected to it and will not even know that EPF is in the way. If the site is not on the safe list, end users will see this warning:

They will have the option to just click on the link and proceed, add to whitelist (at which point they are automatically allowed through in the future) or add to blacklist.
Because of the way phishing works, and all identity theft or forgery in general, it is impossible to secure email messages in transit without making annoying modifications to the message that often distort the look and feel of it. Majority of those links are in the 95% of the mail that passes through ExchangeDefender as SPAM/SureSPAM, meaning that they would never even be seen by anyone. By moving the Phishing Firewall to the cloud, we can now secure every device and provide additional metrics and advisory on top of it to protect our clients from 0-day exploits.
This feature is provided to our clients free of charge and replaces expensive “security awareness training” solutions that users typically hate and do nothing to adequately secure the client. With Exchange Phishing Firewall we enable our clients to create custom policies, maintain whitelists, blacklists, get enterprise reporting and more. It further allows us to go one step beyond – in the upcoming releases we’ll offer the ability to display a screenshot of the site as well as link intelligence data (How long ago was the domain name registered? Where is the IP you’re about to go to located? Is the domain a close spelling error of a widely recognized site? Is the forged site just a cloud hosted Google, Microsoft or Amazon cloud service instance that is holding or redirecting you to another more dangerous location?)
If you’re currently on ExchangeDefender Essentials, we encourage you to schedule a demo with our team to check this feature out as it’s significantly cheaper than antivirus or “security training” solutions and will do a far better job. If you’re on ExchangeDefender Pro or ExchangeDefender Enterprise, you will get this feature free of charge. On Monday, June 10 we will send an email notification announcing this launch to our partners, MSPs, and Service Providers. On Tuesday, June 11 we will send an email notification to end users. Finally, on Wednesday, June 12th we will go live with the service and hope to minimize the annoyance of phishing once and for all. Email is the single most popular attack vector, with 91% of the compromises starting through a phishing attack, and we look forward to protecting all our users even better.
Phishing: Beware of Strangers
This Thursday, June 6th, we will be announcing a major overhaul in the way we deal with spear phishing SPAM. No, it’s not a mind-blowing patent-pending stroke-of-genius sort of stuff, it’s much closer to what your parents told you growing up: Don’t get into a car with strangers don’t click on links or open attachments from strangers.
In a way, ExchangeDefender has had protection from this issue for years. If you had a decent IT Solution Provider implementing ExchangeDefender for you, they would have setup your SPF record and eliminated this issue – but many don’t. Or they would have turned on ExchangeDefender protection where all messages spoofing/forging your domain would automatically get junked – almost none of them do. Which is why ExchangeDefender as a service has become less of an IT tool and more of an end user suite of services to get stuff done.
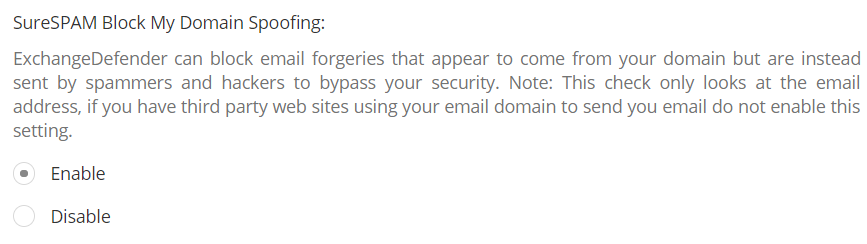
When features like this are left disabled “because they might become support issues” it becomes really difficult to secure users. But I get it, IT companies have a business to run too, which is why we’ve really stepped up our support efforts and are going to be there to help folks get things done without becoming an additional problem for the IT department. Doing so has really made us rethink how we implement features and how the service behavior needs to speak the same language as the end user. Which brings me to phishing beyond forgeries.
Can you spot a stranger?One of the new phishing protection features in ExchangeDefender will allow you to flag messages that are coming from outside of your organization. You will have two settings – to modify the subject and to modify the header of the message so when you look inside of your mailbox you’ll know what came from a stranger right away. Try it:
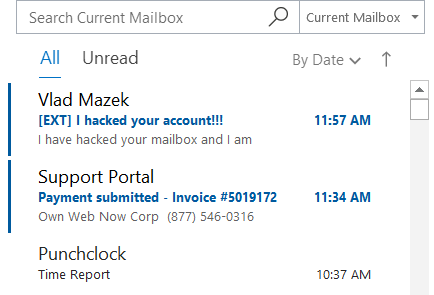
Even from the message listing you’ll know which messages shouldn’t even be opened. But suppose you ignored even that – you can set another warning, printed inside of the message, giving the user even more of an instruction of what to do.
Warning: Message was sent from outside of the organization. Do not click on links or open attachments if you don’t recognize the sender.
Far from subtle. And it has to be – because most people check email quickly, between tasks, or are simply interrupted by it. ExchangeDefender has your back, and we’ll make sure we alert you to possible issues before they become problems. Which we hope everyone will be aboard with.

Please join us, June 6th at Noon, for our NEW webinar featuring ExchangeDefender’s Phishing and Spoofing protection, plus see what’s new with Encryption, WFS, and Wrkoo!
