Selling Cybersecurity Without Fear Tactics: A Guide for MSPs

Let’s be honest—cybersecurity sells, and it’s tempting to lean on scary headlines.
“Hackers are targeting your business!”
“Ransomware could wipe out your data!”
While technically true, fear-based selling wears thin. It breeds skepticism, fatigue, and often ends in “I’ll think about it” instead of a sale.
So, how do you sell cybersecurity in a way that’s effective, trust-building, and value-driven?
Let’s dive in.
Step 1: Focus on Trust, Not Terror
Clients—especially SMBs—aren’t looking for horror stories. They want:
- To understand risk, not panic over it
- A clear solution they can afford
- Confidence that you’ve got them covered
Position yourself as a guide, not a doomsday prophet.
✅ Instead of: “Hackers could steal your data any second!”
💡 Try: “Cyberattacks are rising for businesses your size—here’s what others are doing to stay protected.”
🔗 According to Cybersecurity Ventures, global cybercrime costs will hit $10.5 trillion annually by 2025.
(Source: Cybersecurity Ventures)

Step 2: Lead with Education
MSPs that educate sell more—period.
Instead of overwhelming clients with jargon, simplify the narrative:
- Explain why email is the #1 attack vector
- Show how phishing, spoofing, and ransomware actually happen
- Demo how tools like ExchangeDefender filter threats before they reach inboxes
🎯 Use visuals, infographics, or even real (anonymized) examples from recent incidents.
🔗 75% of organizations around the world experienced a phishing attack in 2023
(Source: Proofpoint 2023 State of the Phish Report)

Step 3: Talk ROI, Not Just Risk
Security isn’t just about prevention—it’s about business continuity and saving money in the long run.
Explain how cybersecurity:
- Reduces downtime and data loss
- Cuts insurance premiums
- Keeps clients compliant with industry regulations
- Saves on remediation and PR costs
🛠 Example: “Email continuity through ExchangeDefender means even during outages or attacks, your team stays productive and your business doesn’t lose momentum.”

Step 4: Sell Simplicity & Scalability
Most SMBs worry security will be:
- Too technical
- Too expensive
- Too hard to manage
Reassure them by offering packaged, easy-to-deploy solutions like ExchangeDefender, which include:
- Email Security
- Spear phishing Training
- Email Outage Protection
- Encryption
- Secure File Sharing
You’re not just selling a tool—you’re offering peace of mind as a service.

Step 5: Use Stories, Not Stats (Alone)
Stats are powerful, but stories sell. Share case studies or anonymized “almost-breaches” that were stopped thanks to your services.
Example:
“One of our clients almost wired $30,000 to a spoofed vendor—our email filter caught it just in time. They didn’t even know they’d been targeted.”
That sticks way more than a pie chart ever could.
Want to show your clients you’re not just selling—you’re protecting?
👉 Let us help you white-label powerful email security, make it easy to deploy, and even easier to sell.
🔗 Learn more about becoming a partner: https://www.exchangedefender.com/partners
ExchangeDefender SMTP Headers
ExchangeDefender mail flow and email analysis troubleshooting is at times a long and difficult process that has been automated through our admin portal at https://admin.exchangedefender.com. We realize that it’s not an option for some of our end users and new MSPs so we often get tickets in our support portal asking us why a certain message got delayed, rejected, classified as SPAM or allowed to get through if it had SPAM content, etc.
In order to troubleshoot an issue with a specific message we always ask for SMTP headers. The following blog post will help you find them in Outlook Web App, Outlook 2013 and Outlook 2016.
Outlook Web App
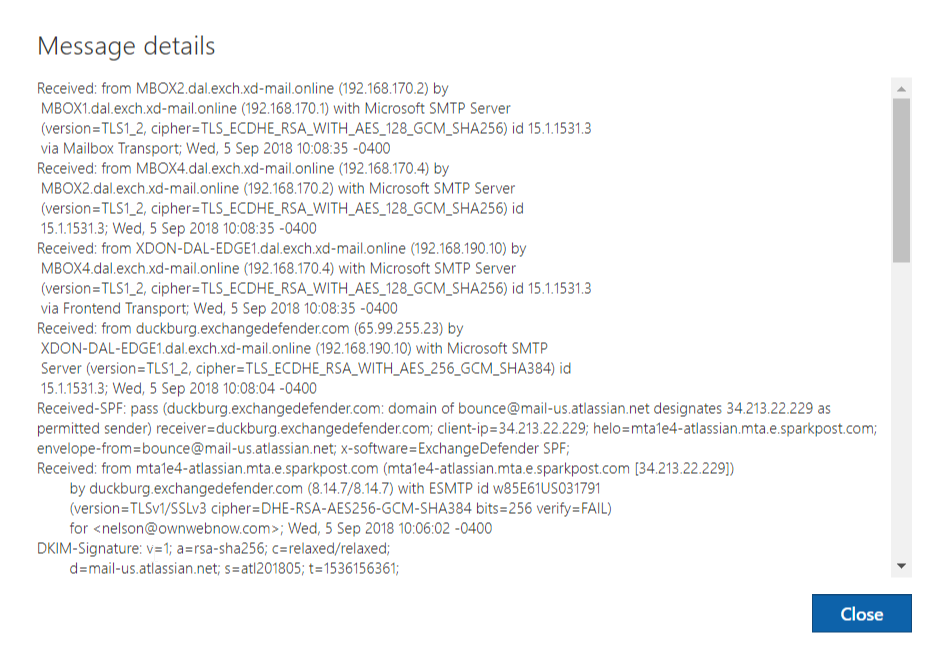
From the message listing, right click on the message and select “View Message Details”:
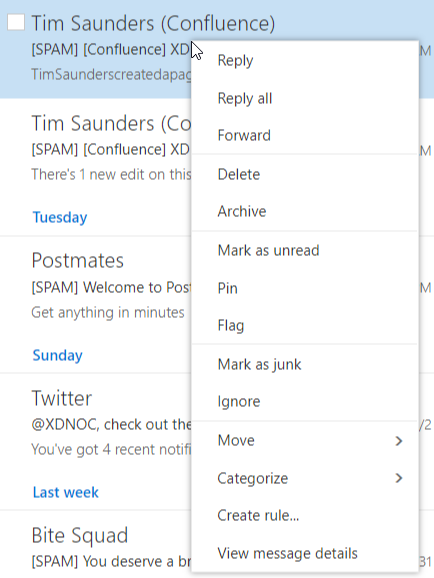
You will see Message details screen. Copy and paste it in the ticket and we can help you with the rest.
Outlook 2013 / Outlook 2016
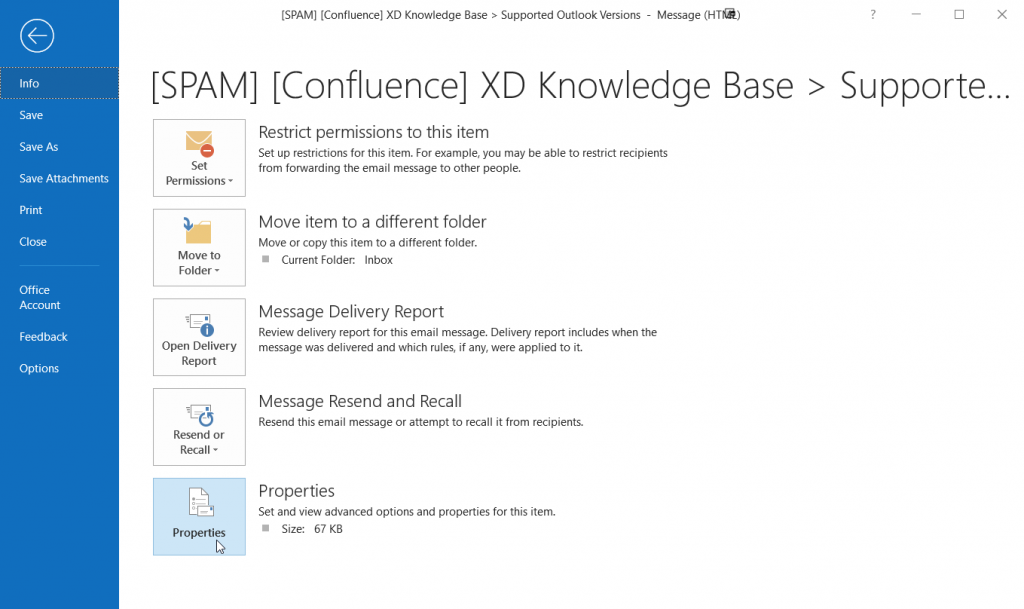
From the message listing double click on the message so it pops up in it’s own Outlook window.
Then click on File and you will be shown the message file options:
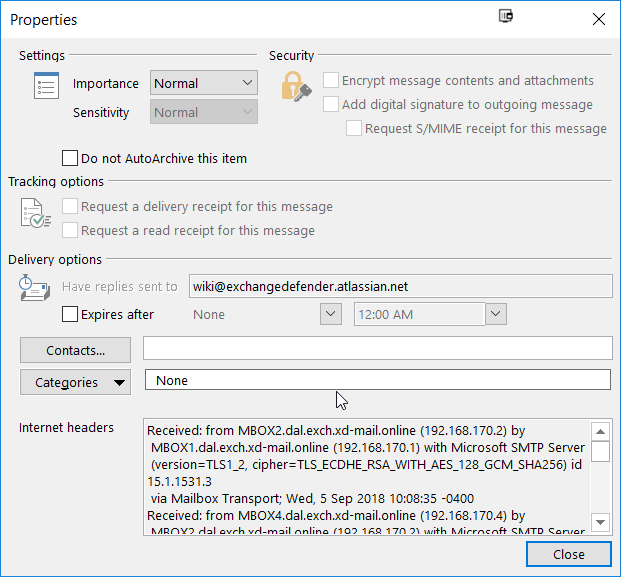
Click on Properties and you will see the SMTP headers. Copy and paste it in the ticket and we can help you with the rest.
Important: Please copy and paste the contents of the screen into our support ticket instead of taking a screenshot. Sometimes the SMTP headers contain characters that are very similar (qf9mfIlI1IlI) and it can take a lot longer to locate the message rather than having a specific text search.
What happens next is that our team is able to locate the specific message in our database and then with that data do further analysis using the node that processed the message and look at all the logs generated by hundreds of different services that are analyzing every message for dangerous content.