Building a Sales Case for Encryption
If you’re running an I.T. business trying to understand HIPAA compliance as far as email security is concerned, you’re not alone. I.T. shops are scrambling to find solutions for their clients that are “HIPAA Compliant.” But what exactly does that mean? For the most part, HIPAA compliance states that you need a set of policies and procedures in place on appropriate use and safeguarding protected health information or PHI, processes to validate those policies and procedures are followed, and supporting technology to facilitate secure and protected communications. In my opinion, it does a very poor job at defining with any reasonable detail as to “how” to protect PHI in email form. The Privacy Rule requires a covered entity participating in the exchange of electronic protected health information (ePHI) to have in place appropriate administrative, technical, and physical safeguards to protect the privacy of PHI, including practical safeguards to protect against any intentional or unintentional use or disclosure in violation of the Privacy Rule.
Furthermore, the standard for transmission security (which can be read here: http://www.hhs.gov/ocr/privacy/hipaa/administrative/securityrule/techsafeguards.pdf) has been updated to enforce the use of encryption. It states that covered entities police themselves in regards to the use of public networks, possess a solution to protect ePHI as it is transmitted, and document that solution. The Security Rule goes on to state that it is perfectly acceptable to transmit ePHI to be sent over a public network as long as it is “adequately protected.”
If you’re not confused yet, I salute you. What I have gathered is that HIPAA = security + training + polices + procedures–all of which “should be” monitored and audited for compliance. It is the equivalent of saying, “You shouldn’t speed because you might get a ticket.” In this case, you should provide some reasonable level of security, train your staff and end-users on said security, create policies and procedures to comply with HIPAA guidelines. Otherwise, that “speeding ticket” can have a minimum fine of simply a warning to a maximum penalty of $1.5 million dollars with the possibility of up to 10 years in prison–depending on the severity of the breach (see: http://www.mcguirewoods.com/Client-Resources/Alerts/2013/2/HIPAA-Omnibus-Final-Rule-Implements-Tiered-Penalty-Structure-HIPAA-Violations.aspx).
It’s my opinion that the goal here is to protect the transmission and storage of sensitive patient data while trying not to impose a decisive method on how that data should be protected. While I am not claiming to speak for any government official; in a way, I believe the government body is saying, “Listen, be smart. Do everything in your power and ability to protect data in transit and the storage or that data. And if we deem there to be a compliance issue, we will weigh that violation and determine a suitable penalty.” While there’s a veil of ambiguity that shrouds the strategy or implementation of ePHI compliance, you have to admire any body of government that takes an approach of flexibility–allowing the entities to take a best practices approach to the technology that is available. In fact, as previously mentioned above, technology (or the security of that technology) is only a piece of the HIPAA compliance equation. However, since is mainly a technology blog, let’s talk about how ExchangeDefender’s Corporate Encryption can help you become HIPAA compliant with your clients.
ExchangeDefender Corporate Encryption highlights four major are of concern with thinking about email security:
• Pattern Matching – Pattern-based encryption that can detect credit card numbers, social security numbers, dates of birth and other account-specific data.
• Lexicon Keyword Matching – Lexicon dictionaries can contain words and word patterns that can trigger encryption mechanisms and protect from data leakage.
• Corporate Encryption Mechanisms – Corporate encryption mechanisms can automatically encrypt messages or forward the contents to the administrator for the corporate review.
• Comprehensive Reporting – Comprehensive reporting of all email activity as well as a Compliance Officer (CO) reporting with search capabilities provide proof of regulatory compliance and simplify reporting.
ExchangeDefender Corporate Encryption provides an easy and seamless way for organizations of all sizes to implement content protection and comprehensive control over information being sent through email. Powered by ExchangeDefender, Corporate Encryption complies with the SOX, HIPAA, SEC and local government requirements for information encryption while providing powerful audit and policy wizards to meet organizations unique goals. We provide all these features without you having to invest in expensive equipment and colocations fees. If you have additional question about our Corporate Encryption service or any of our ExchangeDefender solutions, give us a call at 877-546-0316. We will be more than happy to assist you in building a solid business solution portfolio.
Benefits of Cloud Computing
In today’s traditional small business office, the best managed in-house servers are still a liability. Unmanaged in-house servers are time bombs. Why do I say this? Because the hardware used to manage your business is still onsite. From my experience, most hardware is unfortunately sitting unsecured in a closet that also houses cleaning products and printer toner or somewhere under a desk with a Post-It note on it stating, “Do Not Power Off.” With LOB applications and other SMB services such as hosted email, compliance archiving, and file sharing in the cloud; your business has nothing onsite to own, update, maintain, or repair. This makes your availability and accessibility to data and services accessible from any Internet connected device.
Availability of Data and Services
No matter how redundant you think your onsite technology is, your efforts will pale in comparison to the most basic Tier 1 data center requirements, standards, and uptime. Consider this: There are 525,800 minutes in a year. Tier 1 data center are required to maintain an uptime of 99.671%, or 523,870.78 of those 525,800 minutes. That means that the lowest tier data center (Tier 1) cannot exceed a downtime of 1,729 minutes annually. For those of you converting the number into hours or scared of math, this equates to no more than 28 hours a year of downtime. While you may be thinking a day plus 4 hours is a lot of downtime, the majority of this time is scheduled maintenance that would be needed anyway regardless where your equipment was located. Even with a minimal guaranteed uptime of 99.6%, your company is still minimizing downtime by utilizing cloud services.
What if the onsite equipment started to fail. If you are a company with no one on staff dedicated to technology issues, you now have to add additional hours to your downtime to locate and schedule professionals to diagnosis, repair, and test a fix. This doesn’t include any additional hours for physical equipment that may need to be order to complete the repair. If you’re an I.T. professional, wouldn’t it be great not to have to worry about monitoring, maintaining, updating or repairing in-house servers on a consistent basis? Imagine the time you could then dedicate to working on your business.
Accessibility of Data and Services
I, like many others I know in various industries, work remotely. There are times when I’m summoned to the office for special events, meetings, or conferences; but other than that, I work in the cloud. From my home office and using something as small as my iPhone, I can access tickets in our support portal, make and receive business calls, send and receive company email–and if necessary, even compose a blog post. Although the majority of time is spent performing these activities on my iMac strictly out of comfortability, point being our company can operate anywhere with minimal technology. Traditional desktop and LOB applications are being redesigned to operate in a cloud environment–thus breaking the symbiotic relationship between software and desktops/servers. With cloud computing, gone are the days of blue screens, random restarts, and incompatibilities between OS and applications.
If you are a Trusted Advisor in technology for your clients, you can no longer afford to carry around the liability of maintaining data or services on a retiring platform. The wheel has been created. The cloud is here to stay. You can’t continue ignoring the future and pushing your clients on technology you are only familiar with, i.e. SBSers. You have to relinquish the “Admin” ego and implement the best solution for your clients need. Today, those needs no longer involve bloated expenses for hardware purchases. By offering cloud services, you can offer your clients a worry-free environment where their data is available and easily accessible.
Global Businesses are integrating Cross Platform Communications but are they ready?
Businesses globally are adopting cloud services and solutions to merge communications across multiple platforms. The days of convoluted practices to remotely access information, documents, and people are long gone and mobile communications with tablets, smartphones, laptops, and even consumer appliances are now accessible from anywhere, at any time.
The biggest problem with this new frontier of technology accessibility is the fact that it is run very much like the “wild wild west.” There are not yet business standards or practices for the solutions, applications, communications platforms, or security, which creates what some might deem as a lawless environment for mid-sized businesses that once held ultimate control over their networks.
Though this description may seem extreme or far-fetched, the reality is that it is not that far off, especially given the state of mobile device adoption in the workplace or what some might call BYOD.
ExchangeDefender is providing ways for VAR’s, MSP’s, Master MSP’s, Solution Providers, Cloud Brokers, and distributors to provide customers with a set of standardized business practices and solutions, that can help clean up the mobile and technology driven wild wild west.
This has been accomplished by identifying key areas in which businesses today require standardization and best practices to control and manage their internal networks, communication, and documents through cloud-based solutions.
These are:
Communications – Email, messaging services, file sharing, collaboration, and content management solutions.
Communication is the lifeblood to any business. By standardizing on a hosted exchange solution, businesses can rest assured that they will have access to their information from anywhere in the world at anytime. This coupled with Sharepoint, Lync, and CloudShare services provides a complete email and messaging solution that can be provided, to give customers business grade messaging across all device platforms.
Security, Business Continuity, and Compliance – Antispam, encryption, compliance, archiving, and backup solutions.
The importance of keeping communications secure, free from outside eyes, constantly backed up, and available when needed is key to any business practice. Some businesses require specific levels of compliance in order to maintain legal requirements. Having this information can significantly increase an IT companies credibility by assuring that their customers meet all of the compliance, archive, and ecryption requirements set forth by their industry.
Infrastructure – Dedicated Servers, Virtual Servers, colocation services, and Web hosting.
Cloud infrastructure solutions provide businesses with cost effective ways of providing global resources without the high costs of hardware and maintenance. Virtual servers significantly decrease energy consumption and overhead costs, while increasing productivity, redundancy, security, and availability for workers across multi office or single location deployments.
As medium sized businesses continue to flourish and remote offices, mobile workers, and interconnected personnel continue to thrive; cloud services will be at the frontline of standardization practices for business.
ExchangeDefender partners will remain ahead of the game and able to provide all of the necessary solutions to take away any concerns customers may have about having a secure global network, whether it is a traditional, mobile, or hybrid network.
Having discussions and marketing about the growing wild wild west of technology and rogue nature of introducing mobile solutions into environments must be done now. Waiting for a breach or security issue to inform customers of readily available solutions may inadvertently cause downtime, high risks, or worse yet cost business revenues.
For this reason it is important to thoroughly study the types of issues that are facing medium sized companies, as well as creating awareness around solutions that can overcome any potential issue today. With tablets, mobile, and alternative devices connecting to networks everyday, the influxes of unknowns are overwhelming to network managers, so education becomes the key. Utilize your ExchangeDefender team to help point you in the right direction and feel free to ask questions if there is something you don’t understand.
Large Scale Migration
 The most important aspect of a large scale migration is communication. This can make a migration that either turns you into a trusted company relationship or the most recent “IT guy” that was fired by that company. There is a delicate balance that you must preserve between the needs of the technology and the needs of the business owner. The best way to do that is to be as meticulous as possible with your communication process.
The most important aspect of a large scale migration is communication. This can make a migration that either turns you into a trusted company relationship or the most recent “IT guy” that was fired by that company. There is a delicate balance that you must preserve between the needs of the technology and the needs of the business owner. The best way to do that is to be as meticulous as possible with your communication process.
Prep work, communicate.
The first thing you must do is map out an initial time line and start testing the process. This time line will start solely based on the IT departments recommendations. These recommendations are generally based on the hardware or support life cycles and the length of time to complete it. Once you have that sorted out, you probably want to add another two weeks to a month of notice and relay that information to the decision makers at the affected company.
Test, communicate.
Once you’ve received a response, you make adjustments as necessary to your schedule and begin a live test where permissible. We also see excellent guides on the internet on how to do any migration imaginable; the most important point to consider is that no two are alike. So you found a frame work to use on the internet, so you have to take the next step. What we typically do is use test mailboxes, we migrate them individually, and then we move them as batches, repeatedly. The bottom line is this; the more work you do before the migration the less likely you will have to pay overtime for a botched migration.
Execute, communicate, then communicate again
Once you’re satisfied, you reach out to your clients again and confirm that you’re ready to start as you previously agreed. This is where the process will vary when dealing with end users versus an IT partner. We can get away with the following notices: an announcement, a reminder, a start, a mid-point, a completion and a couple of follow-ups. We are about to do this due to the fact that we’re dealing with top notch technology professionals. However, with end users you have to have a more controlling approach, depending on the size of the business, you may opt to have everyone come into the office and leave their mobile devices with you for the migration, or you can do appointments. The most important thing in the process is to check as often as your staffing will allow it, that everything is going smoothly and that the expectations you set are being met. I would even advise a follow up call at 1 week and 2 weeks out to pick up the “slow to report issue” folks.
Taming Your Email
If I ever opened Outlook in the mornings and saw a slew of emails (unread or read) in my inbox, I’d get depressed. Seriously, how can one not feel anxious when seeing (1,323) unread messages sitting in their inbox? If you need a full searchable, secured, and compliance archive solution; then take a look at our long-term Compliance Archive service. Otherwise, take a look below at some of the things I do to prevent email from taking over my life:
• Operate a Zero-Sum email policy. If an email arrives in your inbox, address it, file it, or delete it. In simpler terms, my inbox is not a storage folder–it’s an inbox.
• Never use your Deleted/Trash folder as a storage folder. If you need to file that piece of mail somewhere other than your inbox, then create a folder for that specific purpose. Your deleted folder should be empty most of the time. In fact, you can configure most email applications to remove all contents in the Deleted/Trash folder when you exit the application. Those still reading this probably just laughed at me for suggesting that an email application is ever closed. Which brings me to my next suggestion…
• Close your email application when you are finished working. Trust me when I tell you that your email is still flowing. The brain operates on triggers. By closing down your email application at the end of the day, or when you are not using it tricks your mind into relaxing a bit. Granted, it will probably take your brain a few days to stop freaking out that the email application has been closed; but you will thank me later. We have conditioned our brains to a pavlovian response: Tingle Dingle, check email, tingle dingle, check email, tingle dingle, check email. Get the picture? Your brain is on high alert, waiting for that sound. Close down the app, place your device on silent, and relax.
• Unsubscribe. Most SPAM really isn’t SPAM at all, it’s BACN (pronounced Bacon). If you are unfamiliar with this term, BACN is email that has been subscribed to, but most likely never gets read–think newsletters, sales ads, etc. Now, why they call this BACN is a mystery. Personally if I ask for bacon, I eat the bacon; but I digress. If an email that appears to be BACN arrives into your inbox and you have no desire to ever read these types of emails again from this particular business; unsubscribe. If you received an obviously suspicious piece of email from someone you do not recognize, do not unsubscribe – report it as SPAM. Many spammers use recognizable names to embed their advertising but the unsubscribe link on the bottom just takes you to their site that confirms your email address as valid. Soon after you click it you’ll see an exponential increase in SPAM.
Needless to say, ExchangeDefender is a great solution to keep the email overload from impacting your productivity. Through use of web file sharing to send important documents, compliance archiving to keep 10 years of email and locate anything you need instantaneously, encryption to protect and secure data, we are continuously looking at how we waste time in our Inbox and we fix it with ExchangeDefender.
Michael Alligood
Partner Account Manager
michael@ownwebnow.com
877-546-0316 x707
Competing with Office 365
 Almost on a daily basis I get the question: how do you compare to Office 365? Microsoft’s $6.00 offering is making it hard for a lot of MSP’s to compete, or provide something other than 365, but that shouldn’t be the way it works. As always we are here to help, so I have compiled a list of top three selling points for why ExchangeDefender is the best choice. Use these and you will close the sale with ExchangeDefender, not Office 365.
Almost on a daily basis I get the question: how do you compare to Office 365? Microsoft’s $6.00 offering is making it hard for a lot of MSP’s to compete, or provide something other than 365, but that shouldn’t be the way it works. As always we are here to help, so I have compiled a list of top three selling points for why ExchangeDefender is the best choice. Use these and you will close the sale with ExchangeDefender, not Office 365.
White Label:
Everything we do is completely white label, you can brand ExchangeDefender and make it your own. For branding in the admin panel simply login using your SP credentials, click on the configuration tab, then branding. You can brand the portal with your logo, tagline, and even your customized name for the product.
In addition to all of our services being white label, we also offer free brandable marketing collateral. For free collateral just visit http://www.exchangedefender.com/marketing_xd.php and click on the product you wish to brand. Just click on the download button and you can add your logo, your colors and anything you wish to make this truly a part of your overall solution.
Remember: Your client or prospect is talking to you for a reason – your products and solutions need to reflect your key advantages, not someone elses. After all, if you are just going to resell the same solution anyone can buy at any time then why should anyone do business with you or consider your expertise?
24/7 Support through us
Small businesses are always concerned about the cost. Many business owners are very price conscious and want to find the best bang for their buck. Microsoft charges your client on a per request basis, so each time they call in they’re charged a support fee. I think this is a very important factor to stress, because the end user goes with the notion that they will not experience any problems or it will be tiny enough they won’t have to pay an arm and a leg, or they think it will still be cheaper in the long run, but bad news for them, it won’t be. Depending on your business model, you either include so many hour of support, or you bill in additional blocks of time, this way the customer has more control and the rates are a lot less than what Microsoft would charge. The customer needs to know that in the long run they will end up paying out more to Microsoft for support than what they’re saving on the monthly fee.
In addition to saving money on support, you will also save time. With Microsoft the client must call their support department directly which can create headaches and completely waste all of the end users time. As the servicing partner you can open a ticket with us or speak to our support staff directly, this leads to a quicker resolution time and a more satisfied customers.
Everyone goes into the cloud expecting the best case scenario. Truth is, all technology is susceptible to failure and the bottom line is that you have a plan for how to deal with things like outages, DDoS attacks and communicate effectively with your clients about their service. When you’re “just a reseller” you get none of the profit and all the blame.
Personal Relationships
At ExchangeDefender we make it our priority to build personal relationships with each and every one of our partners. We are always available, someone will be here to answer your questions. Speaking from the business side I know many of our partners and speak with them on a regular basis to make sure that everything is going smoothly and to offer any help that I can. As far as the support staff goes, they’re readily available through the portal 24/7 and by phone from 4 am EST to 7:30 pm EST. Over time you will become familiar with them the more you speak with them on the phone or deal with them directly in the portal. With Microsoft you are unable to have this personal relationship, every time you call you speak to someone different. Not to mention you’re lucky if your previous issue was documented or that the person you’re speaking to has the level of knowledge to resolve your issue.
So the next time you’re in a situation where you’re against Office 365, just remember these key points and you’ll be able to close the sale with ExchangeDefender!
As the cloud solutions emerge and mature quickly it is important to know who you work with, know that you can count on them and expect them to work with you not against you. These are just the top 3 of our competitive advantages of why you should consider us, next week I will write about the top three reasons your client should chose your ExchangeDefender Hosted Exchange, Sharepoint and Lync offering instead of Microsoft.
Anastasia Wiggins
Partner Account Manager
anastasia@ownwebnow.com
877-546-0316 x739
Motivate Employees By Posting Performance Graphs
 The health and performance of a company is a measurable and dynamically changing set of information, which can be easily created and viewed by management. Many MSP’s have already found that posting call performance, ticket handling times, and managed services metrics, helps to give employees an insight into how they are performing from a technical aspect; but what about the general revenue trend and health of the company?
The health and performance of a company is a measurable and dynamically changing set of information, which can be easily created and viewed by management. Many MSP’s have already found that posting call performance, ticket handling times, and managed services metrics, helps to give employees an insight into how they are performing from a technical aspect; but what about the general revenue trend and health of the company?
People by nature are competitive. This is why sales organizations, or departments often post large boards with information labeling the sales leaders and their numbers. These boards are meant to motivate individuals to strive to be at the top and spark the competitive nature of individuals to strive to be better. You see this in almost every industry, even retail and food service industries post motivators like, top sales and employee of the month boards in their respective break rooms or employee common areas.
Though sales and technical performance is commonly shared with employees, most SMB businesses rarely share overall company revenues, growth, or health with the employees that help to make up the business. Since, every person in an organization has a vested interest in seeing a company succeed, sharing this information may help to motivate employees as a team, much like the individual sales and technical motivators do.
The biggest concern that most business owners and managers have for not sharing vital company information is potential animosity. It may be thought that if a company is doing well and employees gain insight into numbers, they may be more likely to expect larger salaries or increased pay for their work. Though this may be an initial thought if this information is posted, it will not be the norm after it is part of normal routine. This means that once you are posting information regularly, it just becomes second nature.
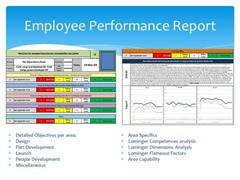 This information becomes significantly important to employees especially if there is a downward trend in the business. This new insight can help to explain management decisions, cut backs in hours, as well as hiring freezes, or any other things that may affect their day-to-day job based on a slow down in business. It also becomes a motivator and visual proof that everyone needs to step it up to increase efficiencies, sales, and revenues.
This information becomes significantly important to employees especially if there is a downward trend in the business. This new insight can help to explain management decisions, cut backs in hours, as well as hiring freezes, or any other things that may affect their day-to-day job based on a slow down in business. It also becomes a motivator and visual proof that everyone needs to step it up to increase efficiencies, sales, and revenues.
The easiest way to implement and post this information is by creating a visual graph that can be hung up in employee common areas. Most spreadsheet and word processor programs allow easy creation of these graphs, which can be printed out and posted. Some companies choose to post this information monthly, where others choose to post quarterly. This becomes an internal decision, but note that monthly provides better motivation.
It is recommended to include overall revenues along with the graph, though again this is an internal decision. This can provide indicators and trends as well as insights; providing employees with information that would have only previously come as management hearsay or owner propaganda. It is not recommended however to send this information via email. In email form, the information is less likely to have an impact or be read, and will not be visually represented daily for all to see and discuss.
By providing company performance information to employees, not only are you making them an accountable asset to the business, but you are also running the business like an enterprise. Corporate public companies must divulge all of their numbers and performance publically, giving everyone deep visibility into the health of the company. Your employees will find motivation in the information, camaraderie, and be proud to help the business grow.
To-Do, or To-Don’t: That is the Question

Over the years, I’ve read hundreds of organizational and business books. The problem with the majority of these books is that they regurgitate the same information or have eight updated “new common sense” editions; “How to Organize Your Business! — 8th edition, now including Working off Lists!” (facepalm)
For the most part, the organizational books all have very similar methods for classifying and arranging everything in your personal and business lives. Normally, this process begins by creating and working off a To-Do list–prioritizing and checking off items as they are completed. This process has two man-made, deep-rooted problems:
- There are too many items to complete on the list; and
- There is not enough time to complete the items on the list.
Notice I said man-made problems. I say this because your list should first be filtered, then prioritized. So, let’s look a little deeper into these two excuses…
There are too many items to complete on my list.
When we create lists, we tend to be under dramatic (not stressing the importance of the task enough) or overdramatic (the opposite of what I just said.) Do all the items on your list need to be accomplished today? Are their items on your list that have low priority? If so, remove them. Place those items on the reverse side or on a completely separate list. The goal here is to accomplish the items that need completion by a certain time or day. If you find an item that is neither important or time-sensitive, remove it.
Another good rule of thumb is to create the list with enough detail so others could follow it. If you need to replace a light bulb in your bathroom and know that the only place close enough that sells that particular lightbulb is Home Depot; then on your To-Do list write:
- Go to Home Depot;
- Purchase replacement lightbulb for master bathroom vanity;
- Go home;
- Replace burned out master bathroom vanity bulb with the newly purchased replacement bulb.
Some would call these directions anal-retentive. However, remember what I said earlier: Create the list with enough detail so others could follow it. Some could argue that step 3 could be eliminated. Fair enough. But leave it on the list because I’ll show you how it’s relevant in a few moments. Moving on…
There is not enough time to complete the items on the list.
Bluntly speaking, there are 24 hours in a day. If you can’t accomplish a daily To-Do list in 1,440 minutes, you have bigger time management issues than you think. I understand that life intervenes and things don’t always work out as planned, but you’re probably wasting more time than you think on items that you shouldn’t be.
Prudently, we all should plan for the upcoming day the night before. This allows us time to collect all our thoughts on the subject at hand without wasting precious time the day of trying to create and prioritize lists. If I need to leave the office and run errands, I try to include drive time, completion time, etc. So if I have to run to the post office to pick up an item, I would calculate 15 minutes (including traffic), 5-8 minutes in line, accepting the package, then another 15 minutes driving back to the office. Now underneath that item is where I start creating another list: My To-Don’t List. In this instance, my To-Don’t list would include: Don’t stop at Starbucks! Similarly, if I have to do Internet research on a specific subject: Don’t log into Facebook!
Now, do you remember my light bulb example and how one could argue that step 3. (Go home) could be removed. What if you didn’t go straight home and stopped off at a friends house or went to the driving range. In doing so, you were late getting home, and didn’t think about replacing the burned out bulb in the bathroom–even though you purchased a new bulb that very day. Would you consider this item as completed on your list? No.
We take small deviations during the day that add up to time we should have spent completing our tasks. In reading organizational book after organizational book, I found they do a good job in explaining how to identify and protect your time against “time suckers” such as email and walk-in coworkers. However, these books fail to explain the biggest time sucker is actually yourself. This is where having a To-Don’t list comes into play. After creating your prioritized To-Do list, create a separate list of things you will not do so you can maintain your commitments and complete your To-Do list. It may seems silly to write down items you don’t plan to do. However, it’s been my experience that the items we don’t plan to do take up the most time.
Michael D. Alligood,
Partner Communications Manager
ExchangeDefender | Shockey Monkey
877-546-0316 x707
michael@ownwebnow.com
ExchangeDefender Service Provider Portal
What is it?
For the most part, the majority of ExchangeDefender services are ordered within the OwnWebNow support portal at https://support.ownwebnow.com. However, ExchangeDefender for Service Providers portal (or ExchangeDefender SP for short,) is where you, the partner, will order and manage the ExchangeDefender service for your clients. The ExchangeDefender SP portal is designed for IT Solution Providers that want to offer their own ExchangeDefender service under their own brand–including color templates and logo uploads.
How do I order it?
To order an ExchangeDefender Service Providers portal:
- Log into your OwnWebNow Support Portal (https://support.ownwebnow.com);
- Click on the Service Manager tab;
- Click on ExchangeDefender SP;
- Click the New Account button on the upper right of the screen;
- By clicking the New Account button, this will initiate the setup process;
Step 1. Contacts and Contracts
- This information should be pre-populated with your administrative contact and billing information. If not, please provide this information.
- Pricing: Although it is listed as $2.00 per month for ExchangeDefender SP portals; as an ExchangeDefender partner, you will exempt from this fee.
- If you agree, check the following boxes:
- Terms of Services;
- Acceptable Use Policy; and
- Service Level Agreement.
- Click Next
Step 2. Service Configuration
On this page, you will start branding your ExchangeDefender SP portal.
- First, provide an MSP ID. The Service Provider ID is a signal word that identifies your company, e.g. ABCTech, OwnWebNow, etc.;
- Secondly, choose a product name. The product name is what you wish your ExchangeDefender service to be called, e.g. Awesome Email Scanning Service, ABCTech AntiSPAM Solutions, etc.;
- Fill in all the necessary Admin contact information;
- Click Review to proceed to the final step.
Step 3. Review and Finalize
If all of the information presented on this page is correct, please click Finalize Order. This will finalize this order and provision your portal. After you finalize your ExchangeDefender SP order, you will receive an email containing information about your new SP portal. After you order the ExchangeDefender accounts within your newly created SP portal, you will need to follow our deploy guide, located at: http://exchangedefender.com/media/ExchangeDefender_Deployment_Guide.pdf.
Ordering an ExchangeDefender SP portal is a one-time process. You do not need to order a new portal every time you wish to on-board a new ExchangeDefender client. You will use this newly created portal to add new client wishing to use ExchangeDefender, as well as manage existing client you previously signup for ExchangeDefender services. However, if you wish to use and resell ExchangeDefender Essentials, you will create and use a separate ExchangeDefender Essentials SP portal.
Remember, you will now use this newly created ExchangeDefender Service Provider portal to order and manage the ExchangeDefender service only. All other orderings, including Hosted Exchange, Offsite Backup, etc., will be ordered in the OwnWebNow support portal (https://support.ownwebnow.com). All service tickets concerning issue for any ExchangeDefender service should be opened in the OwnWebNow support portal (https://support.ownwebnow.com) as well.
