Why Email Backup Should Be Part of Your Disaster Recovery Plan

Because when your inbox goes dark, your business shouldn’t.
🚨 The Problem: Email Outages Happen
Imagine this: a sudden power outage, a server crash, or a cyberattack strikes. Your team can’t send or receive emails. Projects stall, client communications halt, and productivity plummets. It’s not just inconvenient—it’s a business risk.
🛡️ The Solution: Email Backup with ExchangeDefender LiveArchive
Enter ExchangeDefender LiveArchive—your safety net when email systems fail. LiveArchive ensures uninterrupted access to your emails, even during outages. Here’s how it supports your disaster recovery plan:
- 24/7 Email Access: Keep your team connected with continuous email availability.
- Seamless Integration: Works alongside your existing email infrastructure without disruption.
- Real-Time Archiving: Automatically backs up emails, ensuring no data loss.
- User-Friendly Interface: Access archived emails easily through a web portal.
📈 Why It Matters
Incorporating email backup into your disaster recovery strategy isn’t just smart—it’s essential. It minimizes downtime, protects sensitive information, and maintains client trust. With LiveArchive, your business stays resilient, no matter what.
Don’t let an email outage derail your operations. Integrate ExchangeDefender LiveArchive into your disaster recovery plan today.
Top 5 Email Threats You Didn’t Know Were Hiding in Your Inbox

Let’s face it—email is the lifeblood of modern business. But behind every “urgent” subject line or familiar sender name, there could be something much more sinister lurking. At ExchangeDefender, we spend our days defending inboxes against threats most people don’t even know exist. So today, we’re spilling the secrets. Here are 5 sneaky email threats that could be hiding in plain sight:
1. Lookalike Domains (a.k.a. Evil Twins)

These emails come from addresses that look legit—maybe a single letter off from your CEO’s real email, or a domain that’s cleverly misspelled.
Why it’s dangerous: They’re made to trick you into clicking links or wiring money.
How we stop it: ExchangeDefender uses advanced domain and sender verification to block imposters fast.
2. Zero-Day Attachments
These are brand-new threats that haven’t even made it to antivirus databases yet. They come disguised as invoices, resumes, or project files.
Why it’s dangerous: Traditional filters might miss them.
How we stop it: Real-time scanning and sandboxing help catch unknown threats before you open them.
3. Credential Harvesting Links
Not all phishing scams are loud and obvious. Some hide in the form of password reset requests or shared documents.
Why it’s dangerous: One click can expose your login—and open the door to your entire system.
How we stop it: Link analysis and real-time URL scanning keep you protected, even from shortened or masked links.
4. Conversation Hijacking
Hackers insert themselves into real email threads and respond like they’re part of your team. Creepy, right?
Why it’s dangerous: You’re more likely to trust something that feels familiar.
How we stop it: Behavioral monitoring flags unusual responses—even when they happen mid-thread.
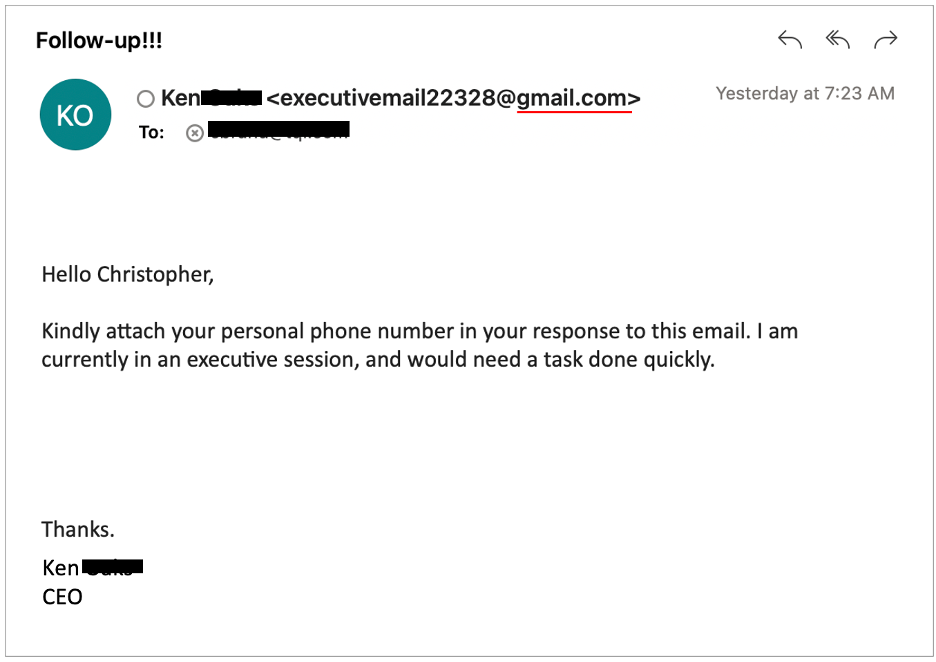
5. Impersonation of Internal Staff
Ever get a weird request from “Accounting” or “HR”? Sometimes, attackers mimic your internal teams to request sensitive info or payments.
Why it’s dangerous: These attacks rely on trust and internal knowledge.
How we stop it: ExchangeDefender uses AI and policy enforcement to detect when internal communication doesn’t add up.
So, What Can You Do?
Well, you already did the first step: you’re here. 🧠👏
The next step? Put a solution like ExchangeDefender Email Security between your team and the bad guys. We’re built to detect, block, and neutralize all of these threats—before they hit your inbox.
Because email should be for collaboration, not chaos.
👉 Learn more about how ExchangeDefender protects your business: https://exchangedefender.com/email-security