St Patty’s Day Promotion
Come celebrate St. Patrick’s Day with our promotion going on, starting March 17th and ending April 17th. We are offering $3.00 off Full Hosted Exchange with an order of 5 mailboxes or more. Just use the code: XDLUCKY16 when ordering your mailboxes. If you have any questions or concerns please feel free emailing us at partners@exchangedefender.com or calling us at (877) 546-0316.
Support Portal Maintenance
We’d like to take this opportunity to apologize for the lengthy outage that our support portal had. We were doing a massive backend software upgrade that did not go as planned and took longer than expected. Any changes made by our staff on your behalf will be added into the portal to ensure the continuity of what was created/modified. Again, I’d like to thank you all for your patience.
How ExchangeDefender Protects You From Ransomware
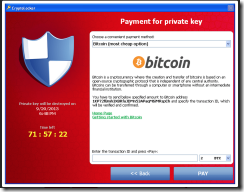 There has been a lot of news coverage of the new wave of ransomware infecting businesses, encrypting hard drives and data on network shares and creating a “ransom” demand in order to unencrypt it. Initially these viruses traveled as typical viruses do – as executable attachments or inside zip files. Most popular of these was CryptoLocker which has made millions of dollars from businesses that didn’t have adequate protection, most recently from a Hollywood hospital that paid $17,000 to get it’s data back. But ransomware has taken a more evil turn – traveling not as an executable that users have been trained to avoid but as a macro inside Word and Excel documents that users often open without a second thought.
There has been a lot of news coverage of the new wave of ransomware infecting businesses, encrypting hard drives and data on network shares and creating a “ransom” demand in order to unencrypt it. Initially these viruses traveled as typical viruses do – as executable attachments or inside zip files. Most popular of these was CryptoLocker which has made millions of dollars from businesses that didn’t have adequate protection, most recently from a Hollywood hospital that paid $17,000 to get it’s data back. But ransomware has taken a more evil turn – traveling not as an executable that users have been trained to avoid but as a macro inside Word and Excel documents that users often open without a second thought.
As with any threat, it’s important to layer protection and defend your business with a good firewall, good desktop security product as well as a perimeter scanning service we provide through ExchangeDefender.
ExchangeDefender Layered Protection
Before we discuss how ExchangeDefender protects you from ransomware, the most important aspect of IT security isn’t prevention – it’s education:
If you receive an attachment of any kind from a source you don’t recognize: do not open it.
If you receive an attachment from a source that you do recognize but it looks and feels suspicious: do not open it. If the email address looks wrong, if there are misspelled words, unusual formatting or unusual activity: stop.
But let’s talk about prevention. Our partners have many options of using ExchangeDefender to stop the spread of dangerous malware.
Attachment & Content Type Blocking: The following process is the most flawless, but most disruptive, way to address an epidemic. You can choose to let ExchangeDefender block attachments that are used by Microsoft Office documents. We do not recommend this route but it’s nice to know it’s there for the events in which people are getting infected and virus scanning has not been able to pick up threats faster than they are infecting systems.
OLE Virus Filtering: ExchangeDefender will block macro (.vbs) attachments outright. But with the rise of Locky ransomware we now also scan Microsoft Office documents and look for infected and dangerous malware placed in those.
Known Threat Sources: ExchangeDefender also blocks dangerous content before it’s even an issue. Most of the threatening content is sent from the same sources that are popular with spammers, hackers and malware distributors: hacked PCs, servers, and blog sites. We maintain a realtime list of networks that spread dangerous content and routinely block their ability to infect our users.
Firewall & Site Blocking: Ultimately, the largest single source of infections isn’t the ExchangeDefender protected or hosted mailbox – it comes through Yahoo mail, Gmail and other non-business email service. If you aren’t blocking those at your work you need to be.
What else can be done?
As mentioned above, client education is the #1 way to address these. Contact our marketing department and ask them to build you a branded best practices flyer for email and Outlook (Hosted Exchange clients only). There are very simple ways to tell when a message is not from your bank or from UPS.
Establish a regularly scheduled backup system for all critical client PCs.
Layer your antivirus protection. No, one AV vendor is not enough and ExchangeDefender uses several commercial and dozens of proprietary data sources to detect and isolate dangerous content. No matter how much you love your single AV vendor and they claim they are the best – like everyone else they will have an infection evade their scan. If you only have one AV engine, consider adding something like ClamAV to your arsenal.
Establish a review of policies and security implementations. We often see that partners rarely configure ExchangeDefender or monitor it in a way that gives them actionable intelligence. The same can be said for client PCs: Are you monitoring your AV implementations? Are you checking that users aren’t turning off AV or firewalls? Are you looking at strange traffic patterns, use of private proxy or VPN networks to evade network security policies?
CryptoLocker and Locky are neither the first nor the most dangerous threats networks face. But with ExchangeDefender, education and layered security we can keep most online outbreaks from affecting business operations.
